Scammers Unleash Flood of Slick Online Gaming Sites
Credit to Author: BrianKrebs| Date: Wed, 30 Jul 2025 18:46:34 +0000
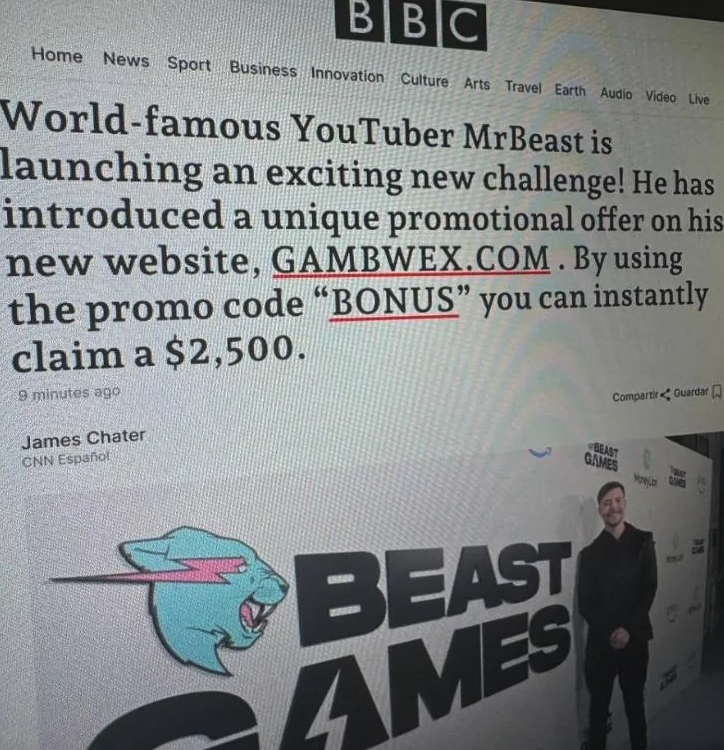
Fraudsters are flooding Discord and other social media platforms with ads for hundreds of polished online gaming and wagering websites that lure people with free credits and eventually abscond with any cryptocurrency funds deposited by players. Here’s a closer look at the social engineering tactics and remarkable traits of this sprawling network of more than 1,200 scam sites.
Read more