Dridex bots deliver Entropy ransomware in recent attacks

Credit to Author: Andrew Brandt| Date: Wed, 23 Feb 2022 11:30:07 +0000
Some code used in the ransomware bear a resemblance to code used in Dridex malware, hinting at a common origin
Read more
Credit to Author: Andrew Brandt| Date: Wed, 23 Feb 2022 11:30:07 +0000
Some code used in the ransomware bear a resemblance to code used in Dridex malware, hinting at a common origin
Read more
Credit to Author: Christopher Budd| Date: Wed, 09 Feb 2022 18:48:31 +0000
Active Directory, Visual Studio, and Microsoft Dynamics & Power BI business packages also got updates
Read more
Credit to Author: Sergei Shevchenko| Date: Tue, 17 Mar 2020 08:00:58 +0000
Security software frequently blocks “bundleware” installers – software distribution tools that bundle their advertised applications with (usually undesired) additional software – as potentially undesirable applications. But one widely-used software distribution tool for MacOS applications goes to great lengths to avoid being blocked as “bundleware” – using a number of anti-forensics techniques that are more common […]<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/n8Txqmat4RA” height=”1″ width=”1″ alt=””/>
Read more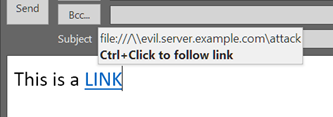
Credit to Author: alexandrebecholey| Date: Thu, 12 Mar 2020 15:34:59 +0000
Microsoft issues its latest set of cumulative updates for Windows and other Microsoft products this week, but the March, 2020 Patch Tuesday is notable not only because of the sheer volume of fixes, but because it will prevent one very serious bug in its Server Message Block (SMB) technology (download the patch right now) that […]<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/d5Hn2Ie7ee4″ height=”1″ width=”1″ alt=””/>
Read more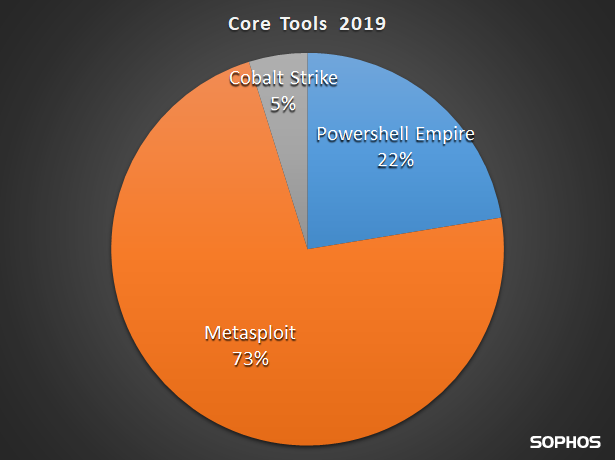
Credit to Author: Tad Heppner| Date: Tue, 25 Feb 2020 13:45:19 +0000
A comprehensive security solution needs a sense of subtlety: not all machine code lends itself to be classified easily as malicious. As with most things in life, there’s a grey area in malware detection that includes hacking tools, poorly designed or easily exploitable applications, or borderline adware that provides little benefit to the unfortunate user […]<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/TR1pieWZO1k” height=”1″ width=”1″ alt=””/>
Read more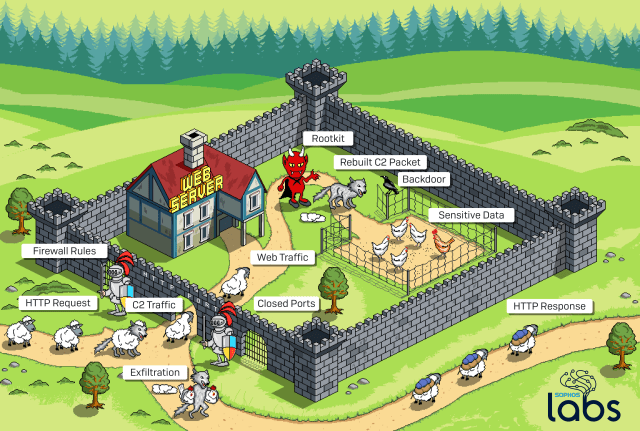
Credit to Author: Sergei Shevchenko| Date: Tue, 25 Feb 2020 13:30:43 +0000
In the course of investigating a malware infection of cloud infrastructure servers hosted in the Amazon Web Services (AWS) cloud, SophosLabs discovered a sophisticated attack that employed a unique combination of techniques to evade detection and that permits the malware to communicate freely with its command and control (C2) servers through a firewall that should, […]<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/IHnT34CbOqM” height=”1″ width=”1″ alt=””/>
Read more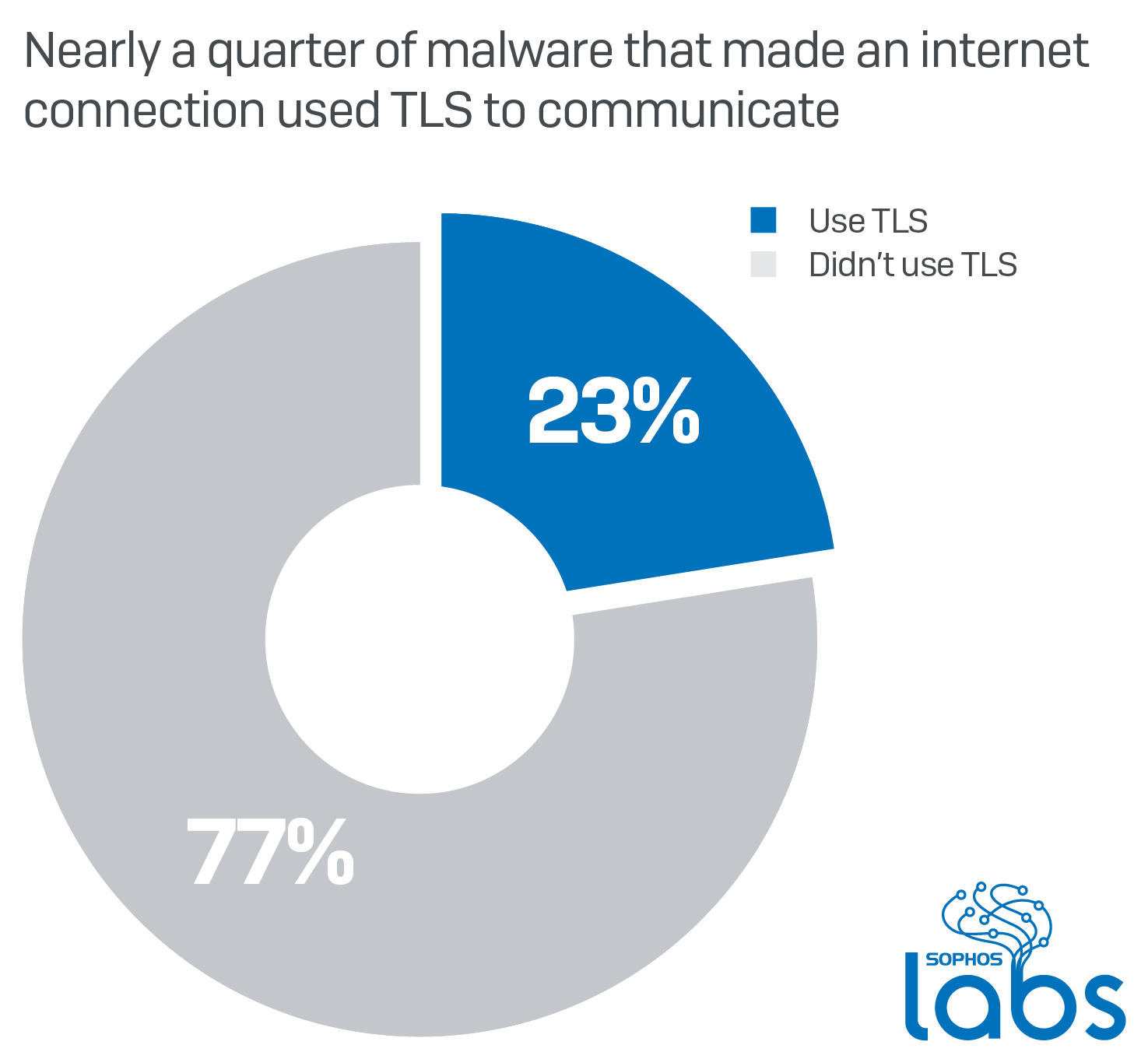
Credit to Author: Luca Nagy| Date: Tue, 18 Feb 2020 13:30:07 +0000
Encryption is one of the strongest weapons malware authors can leverage: They can use it to obfuscate their code, to prevent users (in the case of ransomware) from being able to access their files, and for securing their malicious network communication. As websites and apps more widely adopt TLS (Transport Layer Security) and communicate over […]<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/XXvUtjG7XVU” height=”1″ width=”1″ alt=””/>
Read more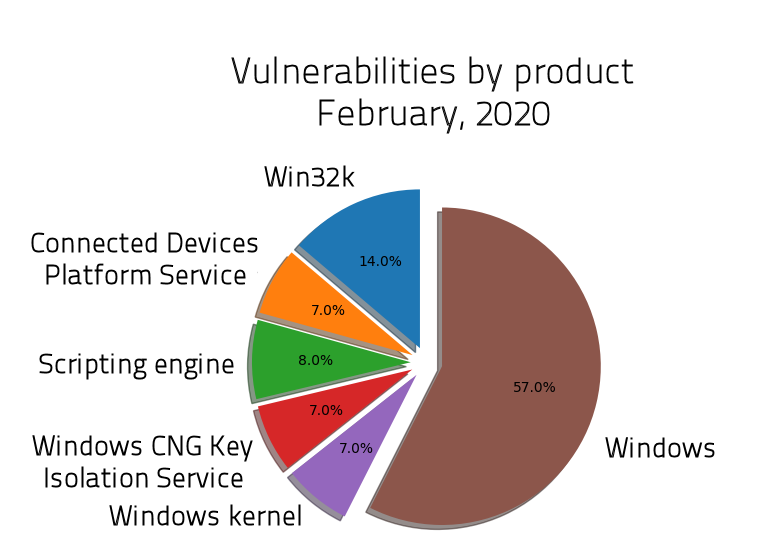
Credit to Author: SophosLabs Offensive Security| Date: Tue, 11 Feb 2020 20:50:22 +0000
For this second Patch Tuesday of 2020, Microsoft has released a hundred patches to Windows and other Microsoft software, including 12 vulnerabilities flagged as Critical, and 87 flagged as Important. In addition, Adobe also published updates for its Flash Player, Acrobat, Framemaker, Experience Manager, and Digital Editions products in notifications timed to coincide with Microsoft’s […]<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/zpsWY9HeJhU” height=”1″ width=”1″ alt=””/>
Read more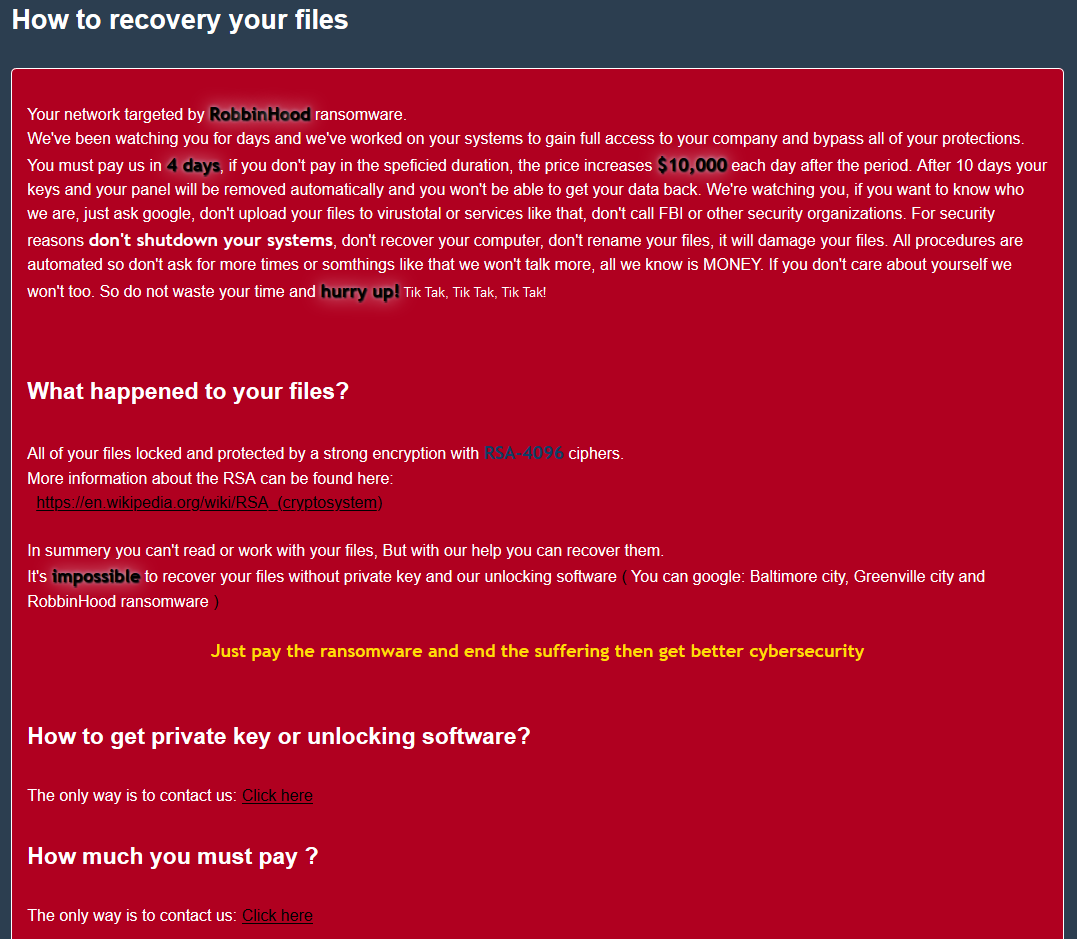
Credit to Author: Andrew Brandt| Date: Thu, 06 Feb 2020 15:22:24 +0000
Sophos has been investigating two different ransomware attacks where the adversaries deployed a legitimate, digitally signed hardware driver in order to delete security products from the targeted computers just prior to performing the destructive file encryption portion of the attack. The signed driver, part of a now-deprecated software package published by Taiwan-based motherboard manufacturer Gigabyte, […]<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/uepwaOU8_Ek” height=”1″ width=”1″ alt=””/>
Read more
Credit to Author: Andrew Brandt| Date: Thu, 23 Jan 2020 00:22:26 +0000
The SophosLabs Offensive Security team answers your questions about the CVE-2020-0601 (aka Chain of Fools and Curveball) vulnerability.<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/682tR8CBAA8″ height=”1″ width=”1″ alt=””/>
Read more