US Cyber Trust Mark logo for smart devices is coming
The White House has launched the Cyber Trust Mark to assist consumers in their quest to buy cybersecure internet connected devices.
Read moreThe White House has launched the Cyber Trust Mark to assist consumers in their quest to buy cybersecure internet connected devices.
Read more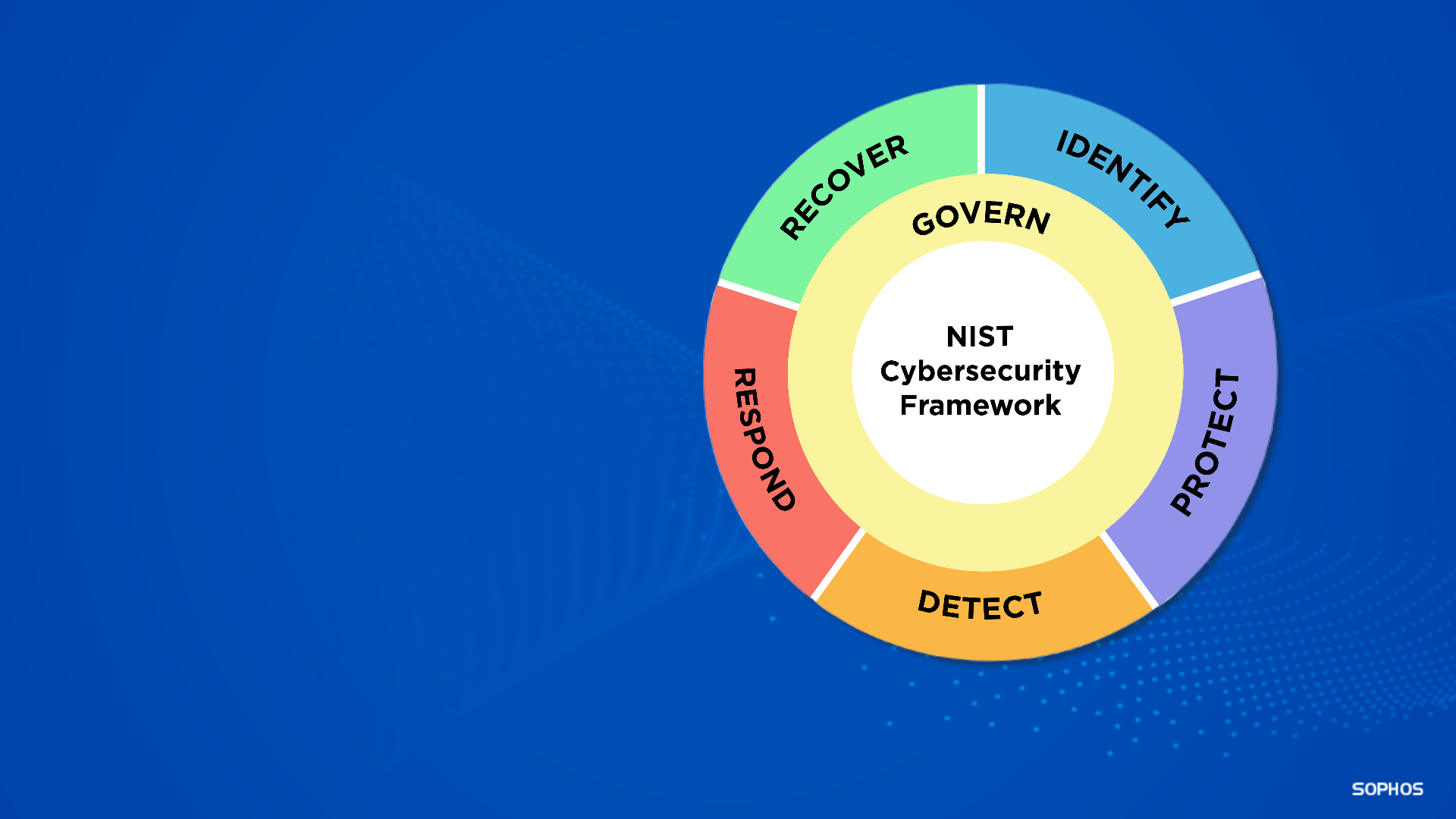
Credit to Author: Doug Aamoth| Date: Wed, 04 Oct 2023 12:18:22 +0000
Sophos can help organizations in their efforts to align with the NIST CSF and other cybersecurity frameworks.
Read moreCategories: Business Categories: News Tags: K-12 Tags: CISA Tags: NIST Tags: CSF Tags: CPG CISA’s released a report with recommendations on how to safeguard K–12 organizations from cybersecurity threats. |
The post CISA releases advice on how to safeguard K–12 organizations appeared first on Malwarebytes Labs.
Read more
Credit to Author: Paul Ducklin| Date: Wed, 03 Aug 2022 16:55:20 +0000
And THIS is why you don’t knit your own home-made encryption algorithms and hope no one looks at them.
Read more
Credit to Author: John E Dunn| Date: Tue, 04 Feb 2020 12:54:30 +0000
Criminals have found to their cost that reducing a device to a pile of rubble means nothing if the internal chips are still in working order.<img src=”http://feeds.feedburner.com/~r/nakedsecurity/~4/DhhD2UVxfZU” height=”1″ width=”1″ alt=””/>
Read more
Credit to Author: Danny Bradbury| Date: Wed, 22 Jan 2020 10:56:40 +0000
How do you ensure you’re compliant with privacy regulations? NIST has released a Privacy Framework to help you get your house in order.<img src=”http://feeds.feedburner.com/~r/nakedsecurity/~4/qZfuL8tJwO4″ height=”1″ width=”1″ alt=””/>
Read more
Credit to Author: Danny Bradbury| Date: Fri, 01 Nov 2019 12:49:16 +0000
The Common Vulnerabilities and Exposures (CVE) system is 20 years old this week.<img src=”http://feeds.feedburner.com/~r/nakedsecurity/~4/vrPGAuEivhc” height=”1″ width=”1″ alt=””/>
Read moreCredit to Author: Kayla Matthews| Date: Fri, 20 Sep 2019 18:18:26 +0000
 | |
| Organizations are keen to protect the personal data of their employees and customers from cyberattack. But what about the data they no longer need? We discuss why data destruction is just as important to cybersecurity as protection. Categories: Tags: datadata breachdata destructionData privacydegaussinggdprNISToverwriteovewritingpersonal informationpersonally identifiable informationPII |
The post What role does data destruction play in cybersecurity? appeared first on Malwarebytes Labs.
Read more