NJ Man Hired Online to Firebomb, Shoot at Homes Gets 13 Years in Prison

Credit to Author: BrianKrebs| Date: Mon, 23 Oct 2023 13:08:27 +0000
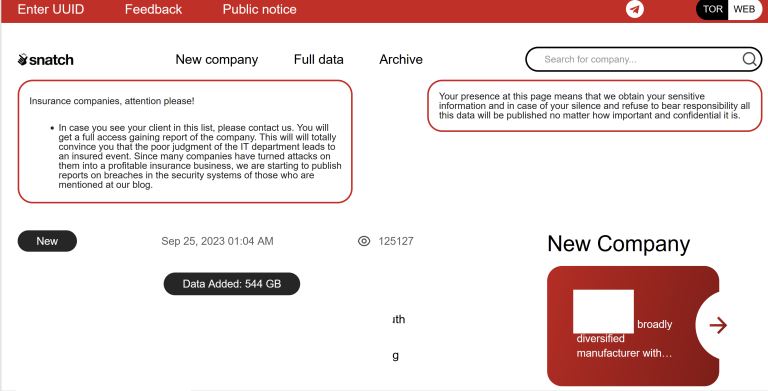
A 22-year-old New Jersey man has been sentenced to more than 13 years in prison for participating in a firebombing and a shooting at homes in Pennsylvania last year. Patrick McGovern-Allen was the subject of a Sept. 4, 2022 story here about the emergence of “violence-as-a-service” offerings, where random people from the Internet hire themselves out to perform a variety of local, physical attacks, including firebombing a home, “bricking” windows, slashing tires, or performing a drive-by shooting at someone’s residence.
Read more