New Leak Shows Business Side of China’s APT Menace
Credit to Author: BrianKrebs| Date: Thu, 22 Feb 2024 13:27:47 +0000
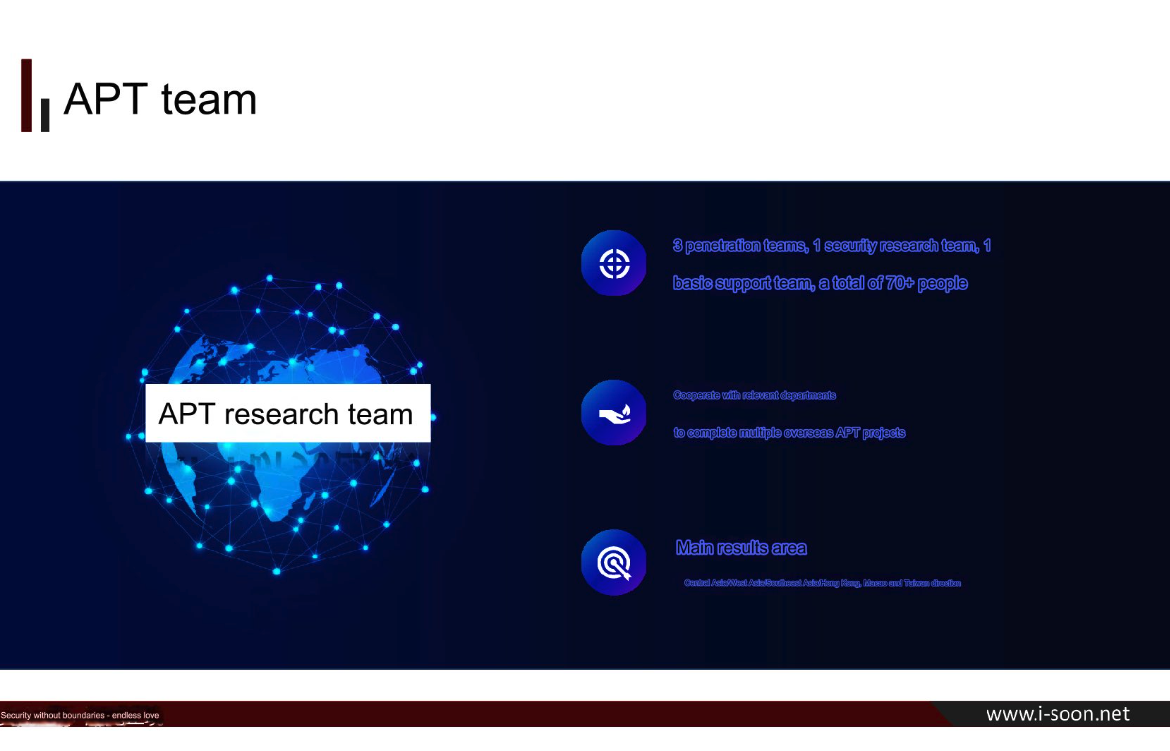
A new data leak that appears to have come from one of China’s top private cybersecurity firms provides a rare glimpse into the commercial side of China’s many state-sponsored hacking groups. Experts say the leak illustrates how Chinese government agencies increasingly are contracting out foreign espionage campaigns to the nation’s burgeoning and highly competitive cybersecurity industry.
Read more