Who’s Behind the Seized Forums ‘Cracked’ & ‘Nulled’?
Credit to Author: BrianKrebs| Date: Tue, 04 Feb 2025 17:09:16 +0000
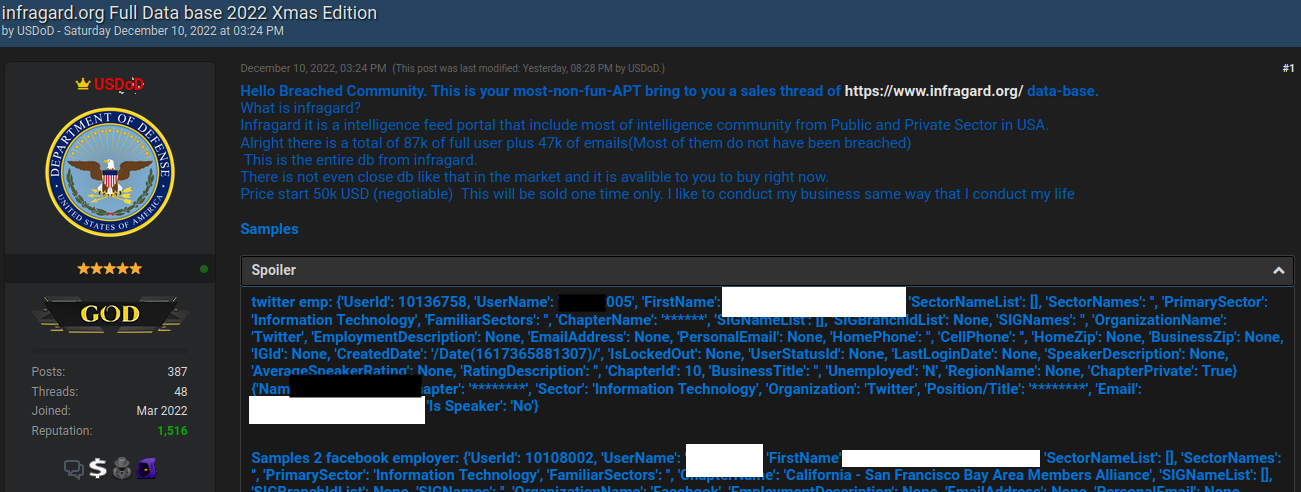
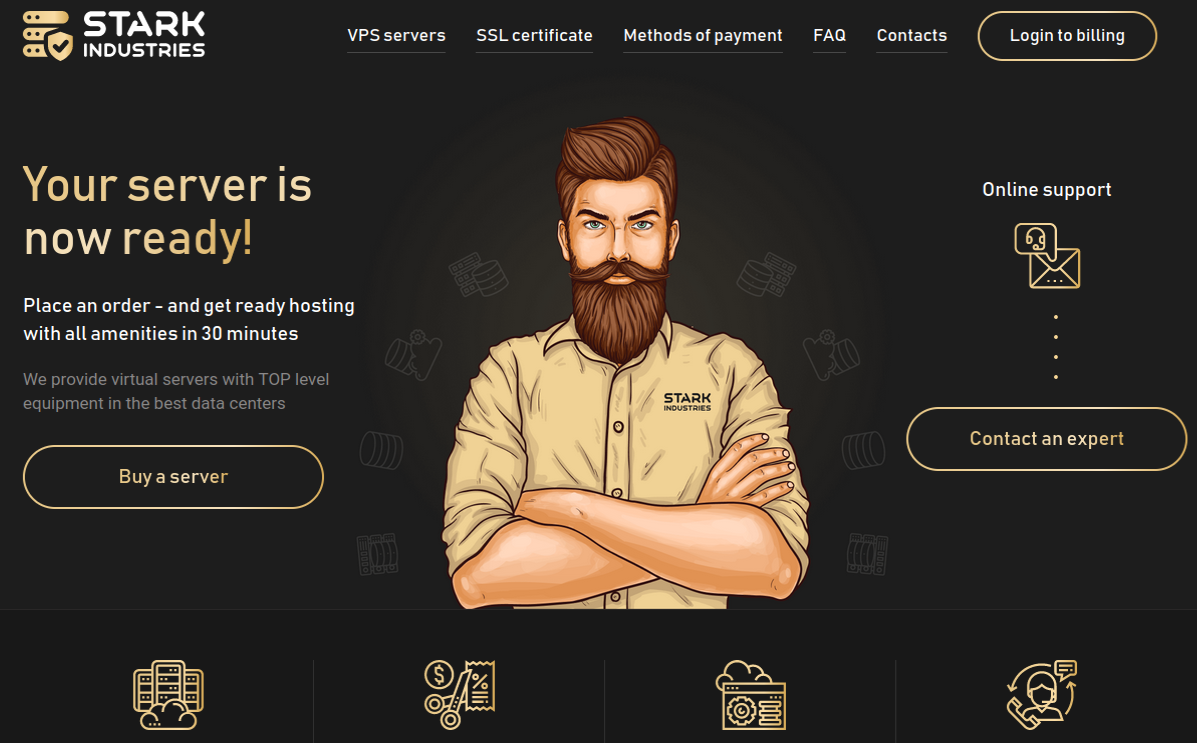
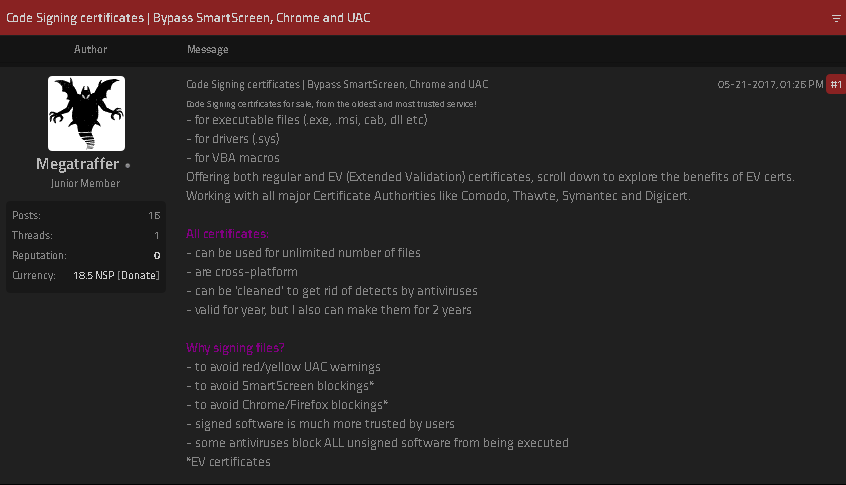
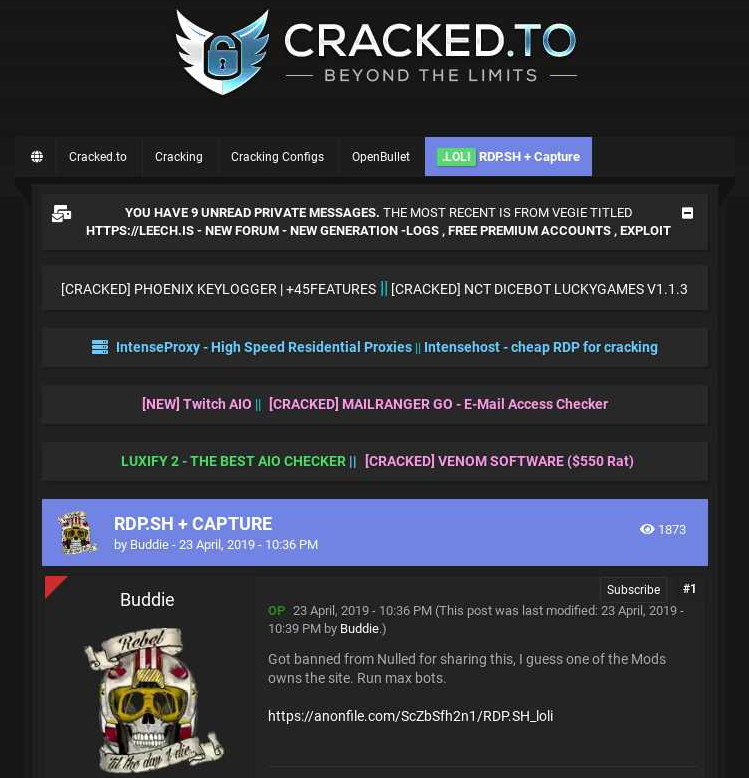
The FBI joined authorities across Europe last week in seizing domain names for Cracked and Nulled, English-language cybercrime forums with millions of users that trafficked in stolen data, hacking tools and malware. An investigation into the history of these communities shows their apparent co-founders quite openly operate an Internet service provider and a pair of e-commerce platforms catering to buyers and sellers on both forums.
Read more