S3 Ep71: VMware escapes, PHP holes, WP plugin woes, and scary scams [Podcast]

Credit to Author: Paul Ducklin| Date: Thu, 24 Feb 2022 16:51:41 +0000
Latest episode – listen now!
Read more
Credit to Author: Paul Ducklin| Date: Thu, 24 Feb 2022 16:51:41 +0000
Latest episode – listen now!
Read more
Credit to Author: Paul Ducklin| Date: Mon, 14 Feb 2022 22:38:58 +0000
There’s a remote code execution hole in Adobe e-commerce products – and cybercrooks are already exploiting it.
Read moreCredit to Author: Malwarebytes Labs| Date: Tue, 01 Feb 2022 11:07:29 +0000
 | |
| A CVE bypass offers up the possibility of admin privileges on Windows 10 machines. Find out what’s happened, and how you can avoid it. Categories: Malwarebytes news Tags: CVECVE-2022-21882exploithackmicrosoftpatchphishupdatewindows 10 |
The post Apply those updates now: CVE bypass offers up admin privileges for Windows 10 appeared first on Malwarebytes Labs.
Read more
Credit to Author: Chester Wisniewski| Date: Wed, 02 Feb 2022 09:34:16 +0000
Following an article on January 24, 2022 of Log4Shell scanning and attack detections since the bug was reported, Sophos addresses reader questions about who’s behind it all
Read more
Credit to Author: Chester Wisniewski| Date: Mon, 24 Jan 2022 17:52:07 +0000
Sophos reviews the scanning and attack detections for Log4Shell to see what’s really going on
Read more
Credit to Author: Paul Ducklin| Date: Thu, 27 Jan 2022 21:09:53 +0000
That infamous “supercookie” bug in Safari has now been fixed. Oh, and there was a zero-day kernel hole as well.
Read more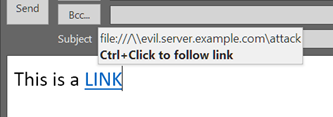
Credit to Author: alexandrebecholey| Date: Thu, 12 Mar 2020 15:34:59 +0000
Microsoft issues its latest set of cumulative updates for Windows and other Microsoft products this week, but the March, 2020 Patch Tuesday is notable not only because of the sheer volume of fixes, but because it will prevent one very serious bug in its Server Message Block (SMB) technology (download the patch right now) that […]<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/d5Hn2Ie7ee4″ height=”1″ width=”1″ alt=””/>
Read moreCredit to Author: Threat Intelligence Team| Date: Mon, 16 Mar 2020 15:00:00 +0000
 | |
| We look at a spear phishing attack from APT36, an Advanced Persistent Threat group posing as the government of India and offering guidance on coronavirus. Instead, users are infected with a Crimson RAT that steals data. Categories: Tags: APTAPT36coronaviruscoronavirus malwarecovid-19credential stealercrimson ratexploitexploitsinfo-stealermacromalicious macromalwarenation-state attackratremote administration toolSocial Engineeringspear phishingspear phishing attacktransparent tribe |
The post APT36 jumps on the coronavirus bandwagon, delivers Crimson RAT appeared first on Malwarebytes Labs.
Read moreCredit to Author: Malwarebytes Labs| Date: Mon, 09 Mar 2020 20:07:46 +0000
 | |
| A roundup of the previous week’s security headlines, including the introduction of a new series on child identity theft, an examination of law enforcement’s cybersecurity woes, a progress check on our stalkerware initiative, and more coronavirus scammers on the prowl. Categories: Tags: a week in securityawiscathay pacificcoronavirusexploitgdprmalwaremicrosoftMobilephishinground upsecurityTESCOweek in securityzynga |
The post A week in security (March 2 – 8) appeared first on Malwarebytes Labs.
Read more
Credit to Author: Paul Ducklin| Date: Tue, 25 Feb 2020 20:55:03 +0000
When a bug’s a zero-day that means it’s being actively exploited. So don’t delay, just patch today!<img src=”http://feeds.feedburner.com/~r/nakedsecurity/~4/xrcwT2eXQRY” height=”1″ width=”1″ alt=””/>
Read more