S3 Ep77: Bugs, busts and old-school PDP-11 hacking [Podcast]

Credit to Author: Paul Ducklin| Date: Thu, 07 Apr 2022 12:24:59 +0000
Latest episode – listen now! Cybersecurity news and advice in plain English.
Read more
Credit to Author: Paul Ducklin| Date: Thu, 07 Apr 2022 12:24:59 +0000
Latest episode – listen now! Cybersecurity news and advice in plain English.
Read more
Credit to Author: Paul Ducklin| Date: Thu, 24 Mar 2022 13:49:08 +0000
Latest episode – listen now!
Read moreCredit to Author: Pieter Arntz| Date: Wed, 16 Mar 2022 14:57:42 +0000
The FTC has taken action against CafePress for the cover up of a data breach. The company is accused of lax security and deceptive practices.
The post CafePress faces $500,000 fine for data breach cover up appeared first on Malwarebytes Labs.
Read more
Credit to Author: Paul Ducklin| Date: Mon, 07 Mar 2022 12:47:44 +0000
Training data stashed in GitHub by mistake… unfortunately, it was *real* data
Read more
Credit to Author: Paul Ducklin| Date: Wed, 02 Mar 2022 16:33:45 +0000
“Change your code to improve cryptomining”… or we’ll dump 1TB of stolen secrets.
Read more
Credit to Author: Paul Ducklin| Date: Tue, 03 Mar 2020 14:08:13 +0000
A financial proivider that gives loans but locks them down to turn them into savings… didn’t lock down its own network.<img src=”http://feeds.feedburner.com/~r/nakedsecurity/~4/zpLp7E5OQY8″ height=”1″ width=”1″ alt=””/>
Read more
Credit to Author: Lisa Vaas| Date: Thu, 27 Feb 2020 14:47:39 +0000
The breach earned derision from both the hacker and observers after another hacker exploited the company’s vulnerable setup.<img src=”http://feeds.feedburner.com/~r/nakedsecurity/~4/MqNwwvLAhW0″ height=”1″ width=”1″ alt=””/>
Read more
Credit to Author: Lisa Vaas| Date: Mon, 24 Feb 2020 13:28:57 +0000
The company left a server open and unprotected, regurgitating private data slurped from thousands of surveilled people, including children.<img src=”http://feeds.feedburner.com/~r/nakedsecurity/~4/F2UPHduG6YE” height=”1″ width=”1″ alt=””/>
Read more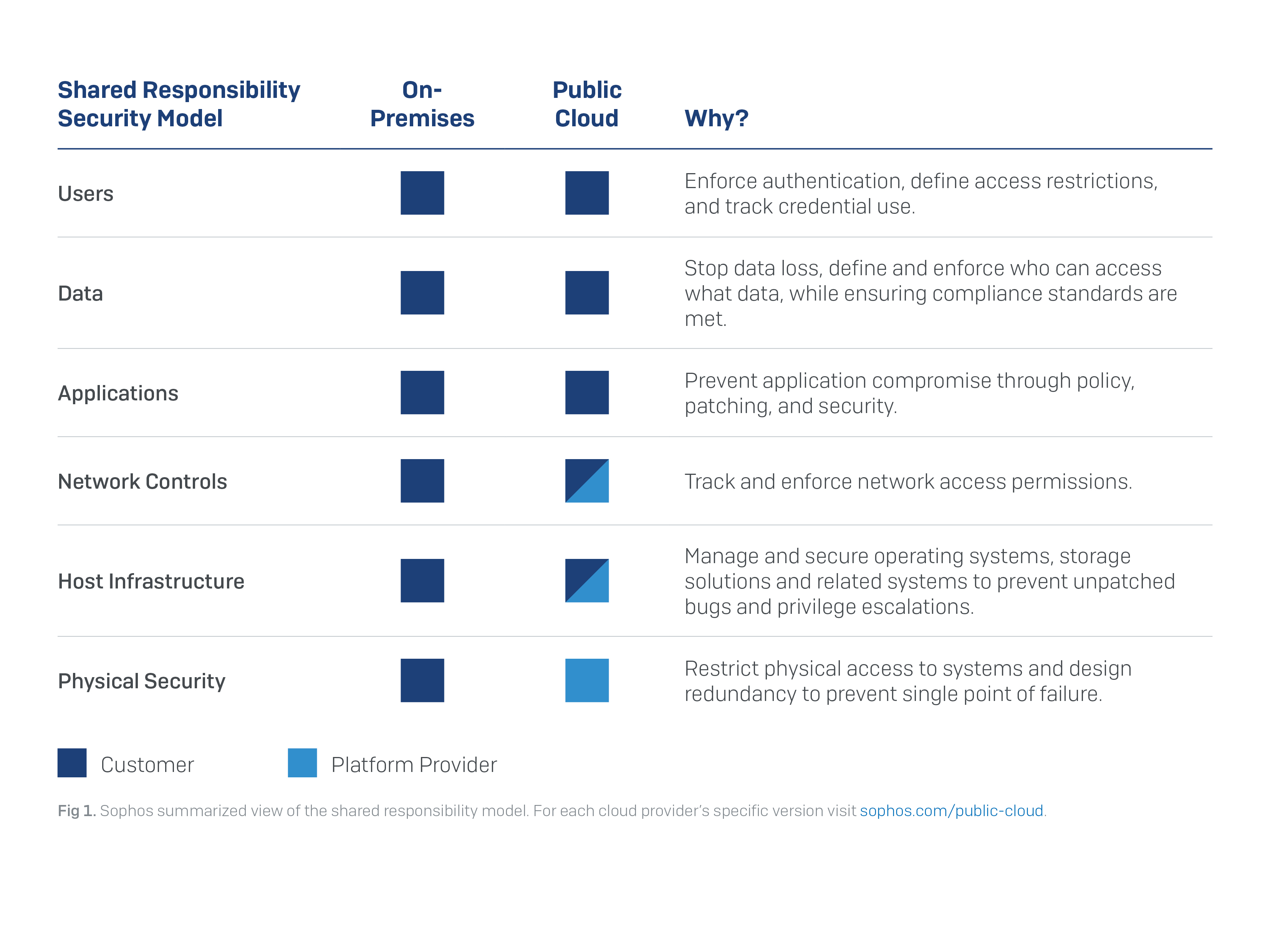
Credit to Author: Sally Adam| Date: Fri, 21 Feb 2020 11:59:35 +0000
The recent MGM Resort hotels cloud server data breach highlights the need to secure sensitive data held in the public cloud.<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/ifst-NkTXmQ” height=”1″ width=”1″ alt=””/>
Read more
Credit to Author: Lisa Vaas| Date: Fri, 21 Feb 2020 11:55:24 +0000
The data dump apparently included PII for Justin Bieber and Jack Dorsey.<img src=”http://feeds.feedburner.com/~r/nakedsecurity/~4/Z2tLH5LX16k” height=”1″ width=”1″ alt=””/>
Read more