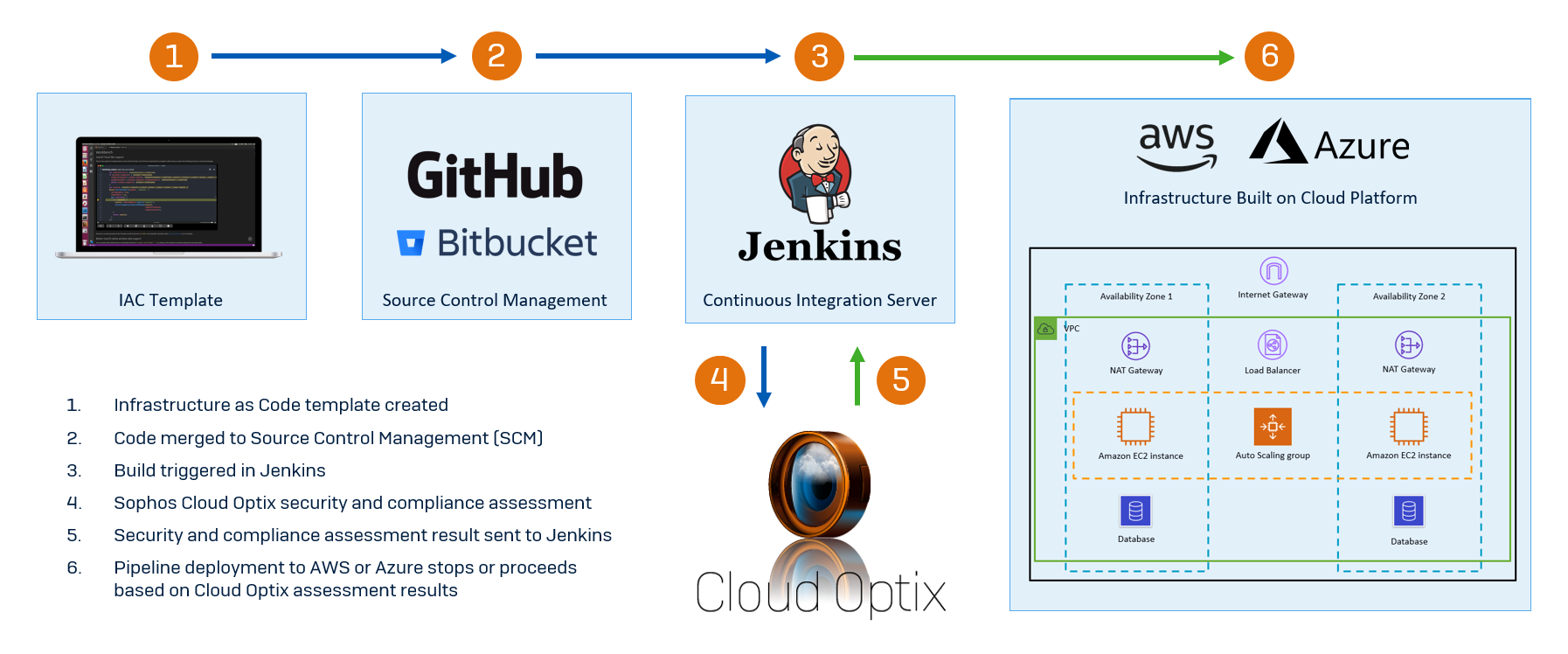
How to secure your AWS EC2 Instance Metadata Service (IMDS)

Credit to Author: Doug Aamoth| Date: Mon, 09 May 2022 15:45:12 +0000
With Sophos Cloud Optix, we make it easy to detect EC2 instances that have version 1 of the Instance Metadata Service (IMDS) enabled and have IAM roles assigned to them.
Read more