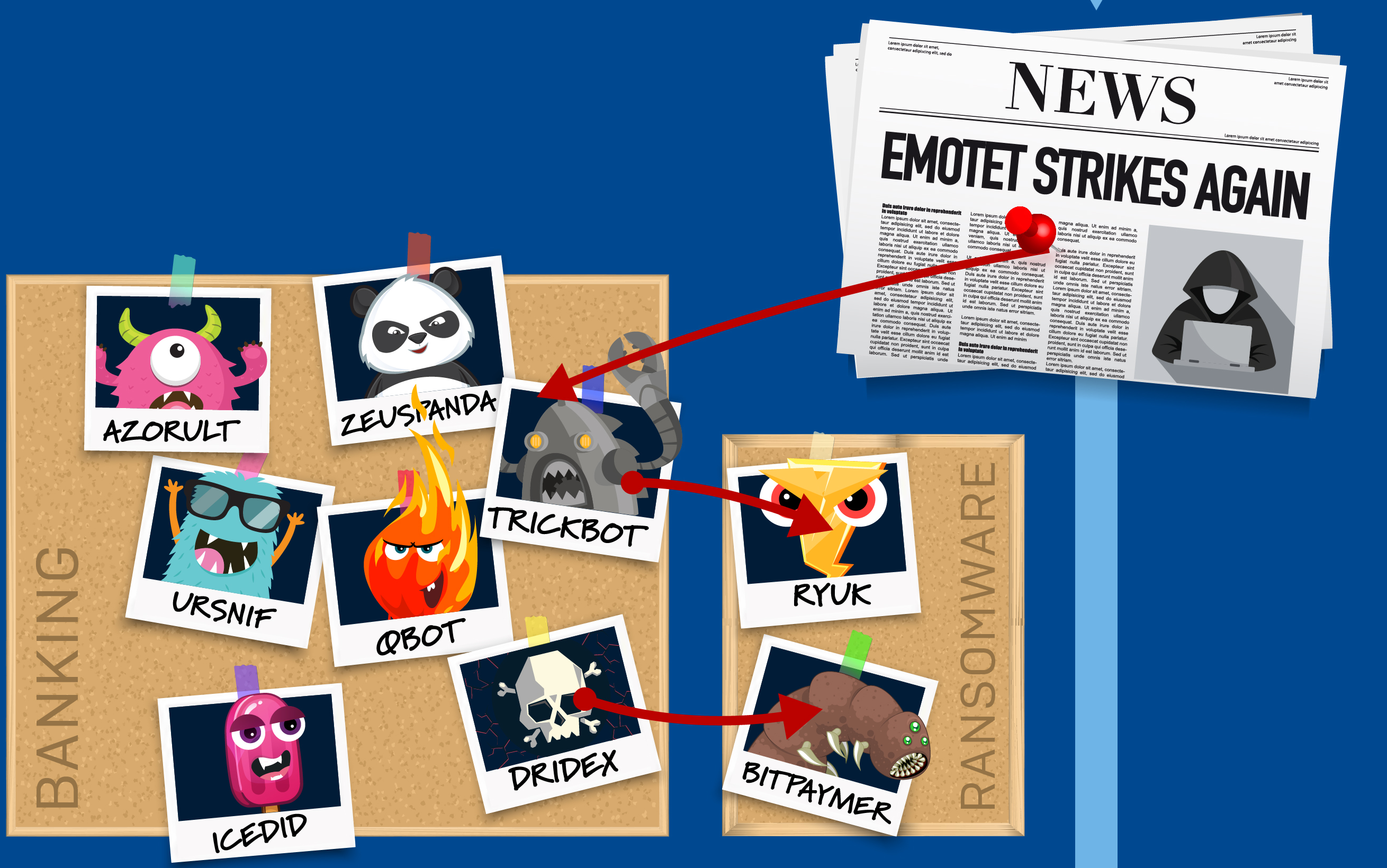
Threat spotlight: The curious case of Ryuk ransomware
Credit to Author: Jovi Umawing| Date: Thu, 12 Dec 2019 22:33:53 +0000
 | |
| From comic book death god to ransomware baddie, Ryuk ransomware remains a mainstay when organizations find themselves in a crippling malware pinch. We look at Ryuk’s origins, attack methods, and how to protect against this ever-present threat. Categories: Tags: AESaverage ransom amountBitPaymerBitPaymer ransomwareCryptoTechDeath NoteemotetFar Eastern International BankFEIBGabriela NicolaogandcrabHermesHermes 2.1Luciano Martinspseudo-ransomwareRansom.Ryukrdpremote desktop protocolRSARussian threat actorsryukRyuk ransomwareShinigami’s revenge: the long tail of the Ryuk ransomwaretribune publishingtrickbotWake-on-LANWizard SpiderWoL |
The post Threat spotlight: The curious case of Ryuk ransomware appeared first on Malwarebytes Labs.
Read more