U.S. Soldier Charged in AT&T Hack Searched “Can Hacking Be Treason”

Credit to Author: BrianKrebs| Date: Thu, 27 Feb 2025 03:39:25 +0000
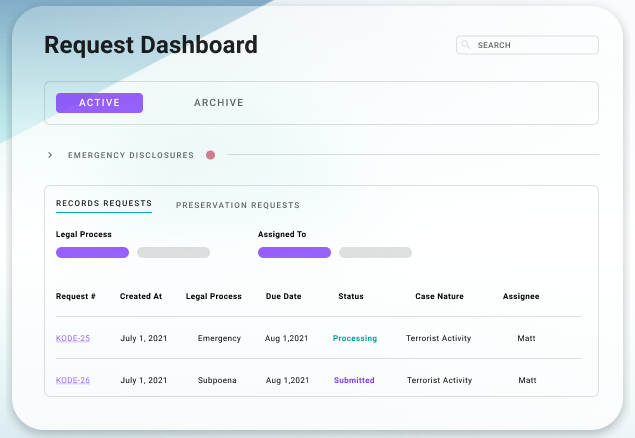
A U.S. Army soldier who pleaded guilty last week to leaking phone records for high-ranking U.S. government officials searched online for non-extradition countries and for an answer to the question “can hacking be treason?” prosecutors in the case said Wednesday. The government disclosed the details in a court motion to keep the defendant in custody until he is discharged from the military.
Read more