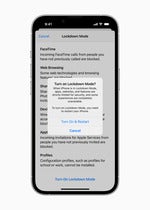
iOS Lockdown Mode effective against NSO zero-click exploit
Categories: Apple Categories: Exploits and vulnerabilities Categories: News Tags: Apple Tags: Lockdown Mode Tags: NSO Tags: PWNYOURHOME Tags: FINDMYPWN Tags: LATENTIMAGE Apple’s Lockdown Mode has shown that it can do what it was designed to do by notifying users about an NSO exploit. |
The post iOS Lockdown Mode effective against NSO zero-click exploit appeared first on Malwarebytes Labs.
Read more