An Investigation of Cryptocurrency Scams and Schemes

Credit to Author: Cifer Fang| Date: Thu, 24 Mar 2022 00:00:00 +0000
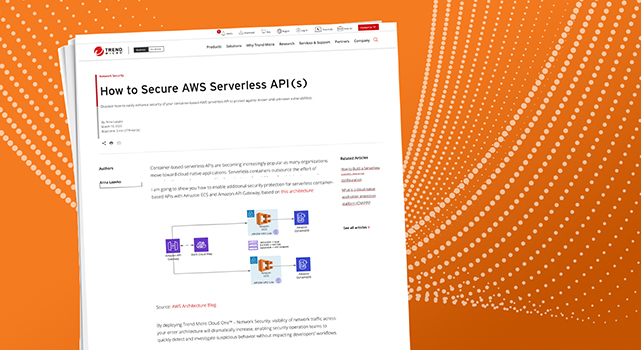
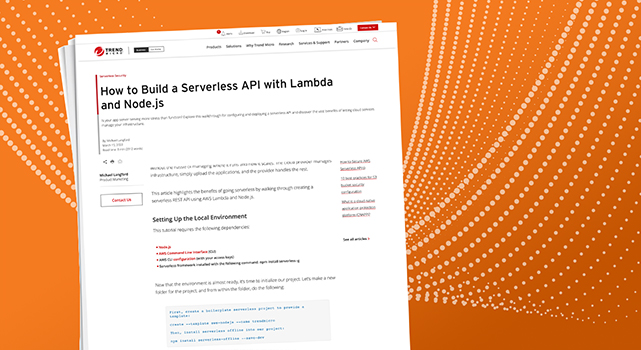
We provide an overview of the diverse range of NFT- and cryptocurrency-related scams that malicious actors use to steal assets worldwide.
Read more