Identifying Rogue AI
Credit to Author: AI Team| Date: Thu, 19 Sep 2024 00:00:00 +0000
This is the third blog in an ongoing series on Rogue AI. Keep following for more technical guidance, case studies, and insights.
Read moreCredit to Author: AI Team| Date: Thu, 19 Sep 2024 00:00:00 +0000
This is the third blog in an ongoing series on Rogue AI. Keep following for more technical guidance, case studies, and insights.
Read more
Credit to Author: Andy Greenberg| Date: Thu, 19 Sep 2024 14:16:21 +0000
The explosion of thousands of rigged pagers and walkie-talkies will likely make Hezbollah operatives fear any means of electronic communication. It’s having the same effect on the Lebanese population.
Read more
Credit to Author: Lily Hay Newman, Matt Burgess| Date: Thu, 19 Sep 2024 13:57:47 +0000
Thousands of beepers and two-way radios exploded in attacks against Hezbollah, but mainstream consumer devices like smartphones aren’t likely to be weaponized the same way.
Read more
Credit to Author: Matt Burgess, Lily Hay Newman| Date: Wed, 18 Sep 2024 16:02:41 +0000
In a second attack on Hezbollah members, two-way radios detonated around Lebanon on Wednesday, causing injuries and multiple deaths.
Read moreCredit to Author: Abdelrahman Esmail| Date: Fri, 30 Aug 2024 00:00:00 +0000
Trend Micro discovered that old Atlassian Confluence versions that were affected by CVE-2023-22527 are being exploited using a new in-memory fileless backdoor.
Read moreCredit to Author: Ted Lee| Date: Thu, 19 Sep 2024 00:00:00 +0000
We observed Earth Baxia carrying out targeted attacks against APAC countries that involved advanced techniques like spear-phishing and customized malware, with data suggesting that the group operates from China.
Read moreScammers are creating fake Walmart virtual shopping lists that look like a contact page for customer service.
Read more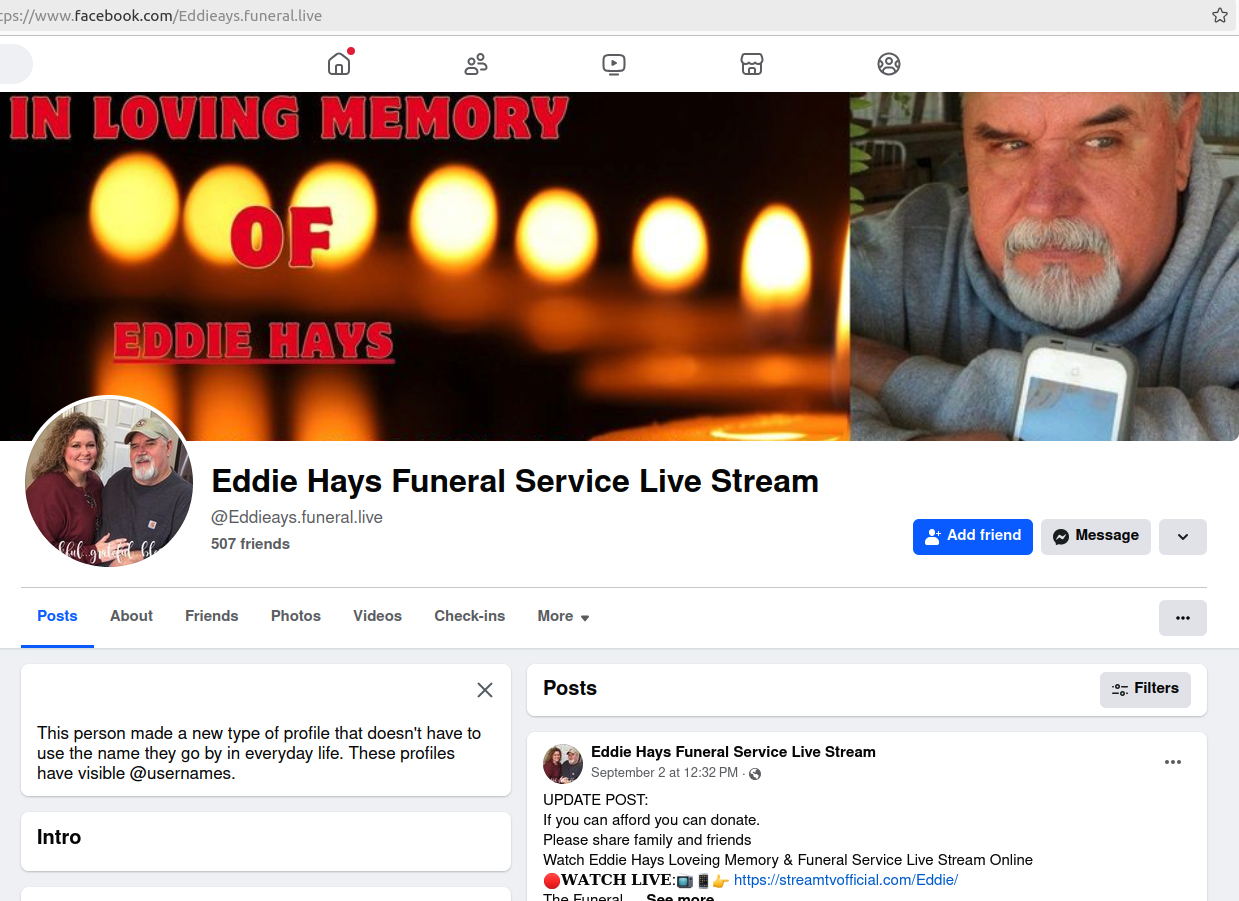
Credit to Author: BrianKrebs| Date: Wed, 18 Sep 2024 13:43:51 +0000
Scammers are flooding Facebook with groups that purport to offer video streaming of funeral services for the recently deceased. Friends and family who follow the links for the streaming services are then asked to cough up their credit card information. Recently, these scammers have branched out into offering fake streaming services for nearly any kind of event advertised on Facebook. Here’s a closer look at the size of this scheme, and some findings about who may be responsible.
Read more
Credit to Author: Kim Zetter| Date: Wed, 18 Sep 2024 08:00:00 +0000
Participants in a hacking competition with ties to China’s military were, unusually, required to keep their activities secret, but security researchers say the mystery only gets stranger from there.
Read more
Credit to Author: Lily Hay Newman, Matt Burgess| Date: Tue, 17 Sep 2024 18:31:41 +0000
At least eight people have been killed and more than 2,700 people have been injured in Lebanon by exploding pagers. Experts say the blasts point toward a supply chain compromise, not a cyberattack.
Read more