SpaceX, CNN, and The White House internal data allegedly published online. Is it real?
A cybercriminal posted free data sets on the infamous BreachForums, but are these actually worth looking at?
Read moreA cybercriminal posted free data sets on the infamous BreachForums, but are these actually worth looking at?
Read more
Credit to Author: Andy Greenberg, Lily Hay Newman, Dhruv Mehrotra| Date: Sat, 21 Sep 2024 10:30:00 +0000
Plus: The FBI dismantles the largest-ever China-backed botnet, the DOJ charges two men with a $243 million crypto theft, Apple’s MacOS Sequoia breaks cybersecurity tools, and more.
Read moreCredit to Author: Vasu Jakkal| Date: Wed, 18 Sep 2024 16:00:00 +0000
End-to-end security is a modern, comprehensive approach to data protection that aligns data protection and incident response across devices, systems, and users. Read the blog post to explore why it’s an attractive option for organizations committed to strengthening their cybersecurity.
The post How comprehensive security simplifies the defense of your digital estate appeared first on Microsoft Security Blog.
Read moreThe FTC published a report about the ways social media and video streaming services collect and use our data
Read moreThe FTC published a report about the ways social media and video streaming services collect and use our data
Read moreCredit to Author: Kyle Philippe Yu| Date: Fri, 20 Sep 2024 00:00:00 +0000
Trend Micro tracked this group as Water Bakunawa, behind the RansomHub ransomware, employs various anti-EDR techniques to play a high-stakes game of hide and seek with security solutions.
Read moreGerman law enforcement agencies have managed to de-anonymize Tor users after putting surveillance on Tor servers for months.
Read moreCar manufacturer Ford Motor Company has filed a patent application for an in-vehicle advertisement presentation system based on information derived from…
Read more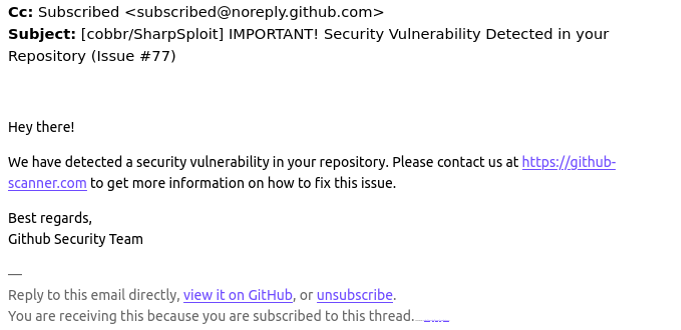
Credit to Author: BrianKrebs| Date: Thu, 19 Sep 2024 19:39:09 +0000
Many GitHub users this week received a novel phishing email warning of critical security holes in their code. Those who clicked the link for details were asked to distinguish themselves from bots by pressing a combination of keyboard keys that causes Microsoft Windows to download password-stealing malware. While it’s unlikely that many programmers fell for this scam, it’s notable because less targeted versions of it are likely to be far more successful against the average Windows user.
Read more