Latest evolution of ‘pig butchering’ scam lures victim into fake mining scheme
Credit to Author: gallagherseanm| Date: Mon, 18 Sep 2023 10:15:27 +0000
Crypto fraud has become the dominant form of Internet-based confidence schemes over the past three years, as demonstrated by the sha zhu pan (“pig butchering”) scams we recently investigated. But one variant has been growing at a particularly rapid pace: fake “liquidity mining.” Sophos X-Ops has also seen growth in crypto phishing sites that connect to cryptocurrency wallets while impersonating cryptotrading-related brands in other types of scams, but these sites are often used by sha zhu pan scammers to separate victims from their money.
Amid research into a new wave of liquidity mining scams, I was directly contacted by a victim in the US who shared the entirety of their experience with us after losing $22,000 USD to a liquidity mining scam. As with other forms of sha zhu pan scams we’ve seen recently, the victim was initially lured into a flirtatious correspondence with the actors hiding behind a dating app profile—in this case, on the app MeetMe.
Scammers have continued to harass the victim after stealing his cryptocurrency, holding out the hope that he could recover his funds by depositing even more cryptocurrency into the scheme; even after he blocked the scammer on WhatsApp, they continued to try to contact him through additional channels tied to his mobile number and e-mail. The scammers also used generative AI to create messages sent to re-establish a connection with the target.
Tracking wallet addresses and the web address of the scam pool, I was able to track the wider scam, identify related infrastructure, and uncover additional scam sites using the same “kit.” I found 13 additional domains hosting the same fake decentralized finance app, which targeted users of Trust Wallet. These sites, over a period of five months, pulled $1.08 million worth of cryptocurrency from victim’s wallets, with a peak of activity in June through August that netted 86 percent of that total. I have also identified hundreds of other scam sites that follow the same formula, netting millions in stolen crypto.
These scams require no malware on the target’s device, and no “hacking” of any sort other than fraudulent websites and social engineering—convincing targets to connect their wallet to an Ethereum smart contract that gives the scammers permission to empty the wallet. As a result, it is extremely difficult to prevent these scams through software protection. Fraudulent wallets and domains are identified and blacklisted as they are discovered, but scammers can quickly deploy new websites and wallets and continue to filch targets’ “risk-free” stakes. Cryptocurrency stolen by these scammers is rarely recovered.
In this report, I’ll focus on the specific details of this victim’s case. A follow-up to this report will cover additional scams we have uncovered related to this case, as well as other similar scams and their technical details.
Liquid vs. Gaslight
Liquidity mining scams leverage the complexity of decentralized finance (DeFi) cryptocurrency trading applications, such as decentralized exchanges (DEXs) and Automated Market Makers (AMMs), to confuse and defraud. These scams promise regular income at high rates of return for investment in a “liquidity pool” that loan cryptocurrency to make contract-based trades between different cryptocurrencies possible.
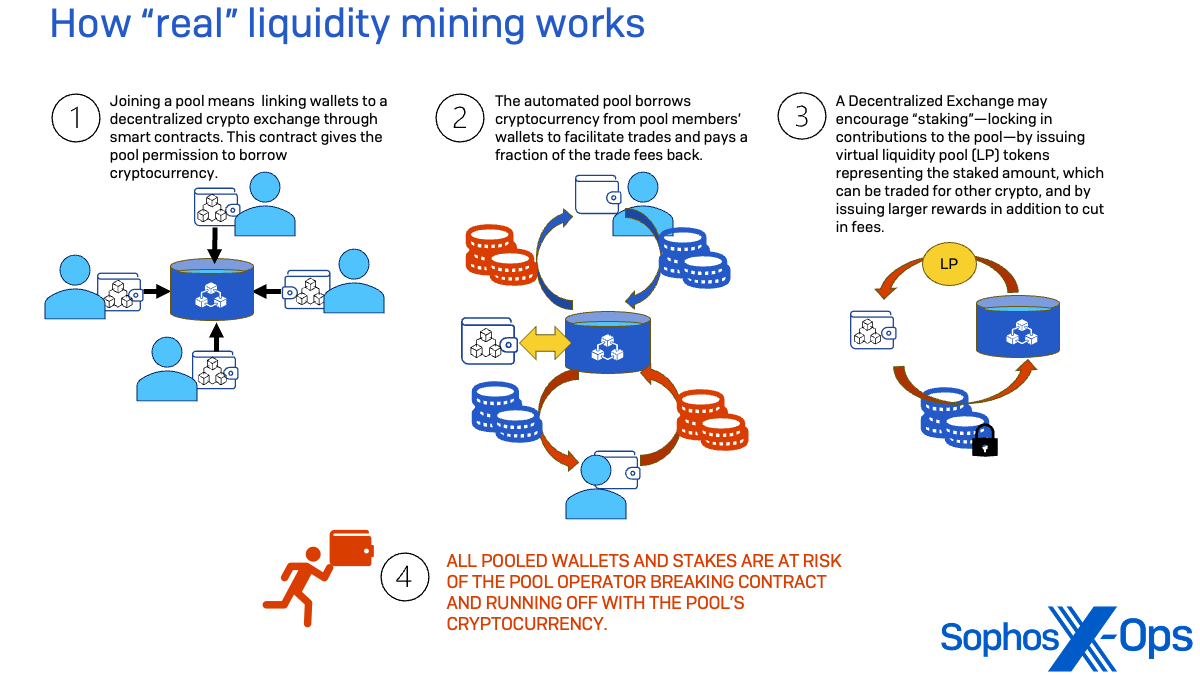
Real liquidity pool arrangements allow DEXs and AAMs to handle trades between various types of cryptocurrencies without having to find a specific buyer. The pool borrows cryptocurrency from the wallets of those who’ve joined short-term to facilitate the trade, then pays back the crypto as the pool rebalances along with a percentage of the fee charged for the trade to pool members, based on the size of their stake in the pool. This is made possible through “smart contracts” that link pool members’ wallets to the “node” hosting the application. In theory, regardless of which way crypto trading is going, pool stakeholders earn a return–that is, if the pool operator doesn’t “rug pull,” breaking the contract and taking all the pooled crypto for themselves.
To join a pool, a would-be member needs to link their wallet to the contract, usually through a web URL opened in the wallet app or with a web browser with a wallet extension. There is a “gas” fee—a charge by the Ethereum blockchain network to confirm the cryptographic contract—but that is usually small.
The contents of wallets linked to liquidity pools remains available to their owners, and can be pulled at any time for other purposes. So, to provide some stability to the pool, pool operators offer additional rewards for “staking” funds to the pool—essentially locking the investment into the pool—in exchange for “LP tokens” (a blockchain token added to their wallet representing that investment), along with other financial inducements. Those LP tokens in themselves can be traded like other crypto, like shares in the pool.
Fake pools use smart contracts that give the scammers access to their targets’ wallets. They may deposit cryptocurrencies into wallets to give the illusion of gains, or deposit counterfeit cryptocurrencies that have deceptive names and no inherent value. The websites used to link wallets in these scams will display data promising daily payouts, and showing the victim’s mounting but fake profits.
Eventually, the scammers “rug pull”—yanking everything out of the wallet with the permissions granted them by the contract and leaving the victim with nothing. Targets will often be told they need to reach certain staking “targets” to get all their funds back, but the funds will never be returned after the initial pull; any additional funds put into a wallet linked to a scam will be grabbed as well through the same contract.
The first warning flag for scam operations is that they often follow the same victim recruiting techniques and pressure tactics associated with sha zhu pan operations. Early scams we encountered used social media sites to cold-approach potential victims, but more recent ones have used the sha zhu pan-style romantic ploys, purposefully crafted “misdirected” SMS messages meant to start conversations (“Are you going to Liam’s party? Is this Sara?”), and other angles to improve their rate of success and widen their potential pool of victims.
The persona who introduces them to the scam will urge them to invest more up until the moment the wallet is emptied, then claim confusion and offer advice when the crypto all disappears.
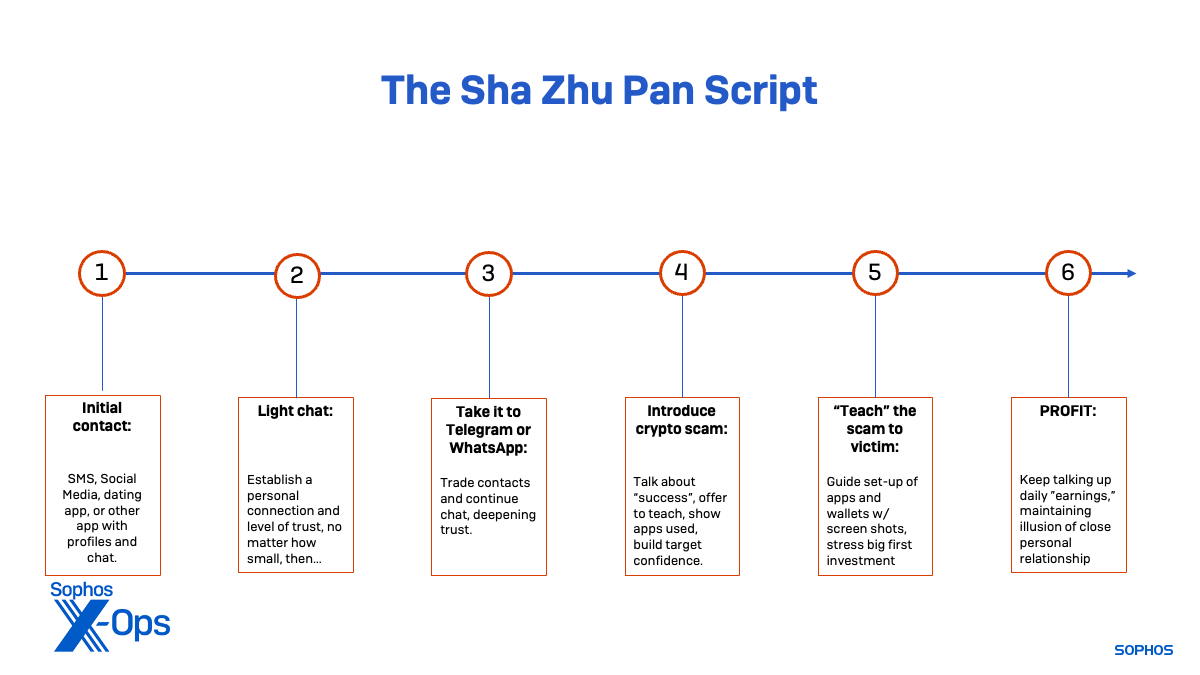
Because these scams use legitimate cryptocurrency apps with high reputations, and their malicious tools are launched within the context of trusted applications, they have a much higher probability of gaining the confidence of potential victims. Because they manipulate the balance of users’ wallets rather than just showing fake profits on a fake trading app display, it is easy to believe that they are what is advertised—that is, if one does not have any idea how liquidity mining is supposed to work. And because the contracts used by these scams give complete control over the contents of the target’s wallet, they can snatch away everything they put in along with the target’s own funds whenever they want—and the victim has no means of preventing it if they don’t have knowledge of how to break the contract.
However, this can cut both ways–there’s the potential for targets who are aware of how smart contracts work to break the contract and run with the “profits” that have been deposited into their wallets, causing the scammers moderate losses. But the volume of cryptocurrency these scams steal from victims makes that sort of risk an acceptable cost of doing business to the scammers.
Bad Romance
In our most recent case, as noted earlier, the target was approached through the MeetMe app, advertised as an app for meeting people (for dating or simple social contact) geographically close to the user. MeetMe’s nonexistent “verification” appears to make it a prime platform for scammers, based on user reviews—users are “verified” by uploading a photo with a face showing.
The target, who I’ll refer to here as “Frank,” is a well-educated retiree located near Washington, DC. Frank was approached through MeetMe by the scam operators, who posed as a young German named “Vivian,” allegedly living in Washington for work. While claiming to be local, the persona used in the account first suddenly “moved” to Ohio and then back to Germany over the four-month course of the interaction, avoiding nearly all attempts to talk by voice or meet in person.
Late in March and soon after the initial contact, Frank was encouraged to take the conversation over to WhatsApp. The phone number associated with the WhatsApp account used by “Vivian” was issued by a United Kingdom carrier, Telefonica UK (O2). This is a common feature of sha zhu pan scams; in the cases I’ve examined, almost all of them used WhatsApp or Telegram accounts tied to UK mobile numbers, regardless of where they claimed to be—even when using US numbers registered through Voice over IP vendors to send initial text messages.
Three days into the conversation, “Vivian” started pushing the target to “invest” in a liquidity scheme: “If you have a lot of free time now, I can teach you to mine. This way you can also use your free time to earn some revenue.” Frank expressed unease about anything involving cryptocurrency, and the scammer assured them that it was “risk-free”:
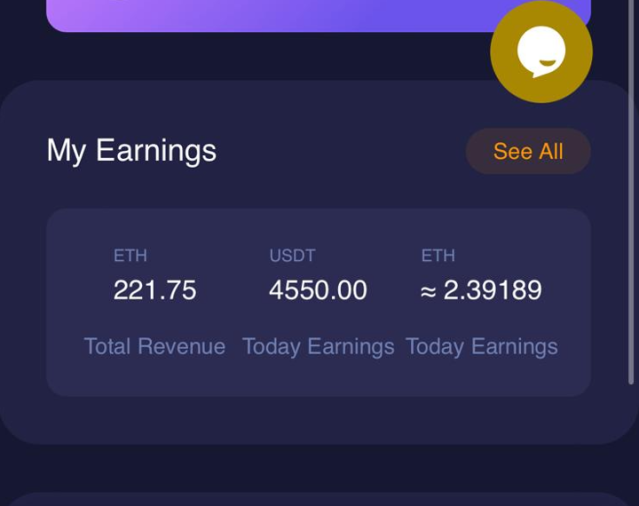
Vivian From German in DC: Digital currency mining, as the name suggests, is mining liquid digital currency. I put my money in my Trust wallet and participate in the mining activities inside Trust, which is risk-free like depositing in a bank, and I even feel safer banking than a bank, because Trust wallet is one of the largest crypto wallets in the world. I just exchange my money for a stable USDT and put it in my own Trust wallet which gives me 2.5% daily. I now have $182,000 in my wallet and mining brings me $4,550 per day, which is risk-free money management, so I get a steady return every day!
Frank was highly resistant to this line of conversation, being averse to anything having to do with cryptocurrency. The scammers persisted, telling Frank that there was no risk, and that the cryptocurrency he put in his wallet would stay there. Finally, on May 1—more than a month after initial contact—they managed to convince Frank to install wallet apps on his phone. Using annotated screenshots, they walked him step by step through the process of installing the legitimate and widely trusted and used apps TrustWallet and Coinbase:

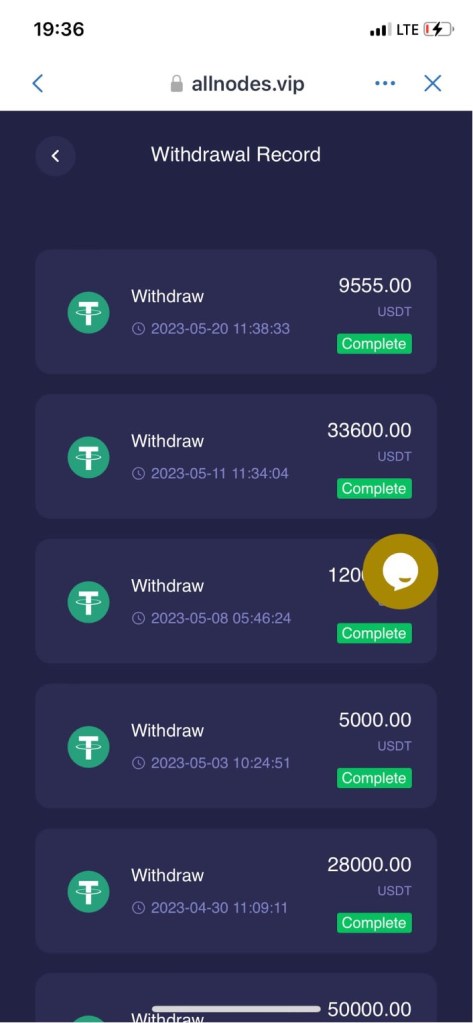
Even after receiving these instructions, Frank was reluctant to go forward, and steered the conversation to other topics. But “Vivian” repeatedly brought up wanting to “teach” the target how to trade over the next few days, showing screen shots of purported profits from the liquidity scheme, showing “earnings” from the pool. (See Figure 7.) “Vivian” also sent a “withdrawal record” screenshot that claimed to show thousands of Tether (USDT) that had been reaped as profits—over $88,000 in three weeks at the end of April and beginning of May, according to the screen shot.
In late May, after weeks of engaging with the target, “Vivian” was close to convincing them to join the fake pool, and dropped another explanation of liquidity mining to explain how it worked. However, “Vivian from Germany” dropped the explanation into the WhatsApp chat in Chinese:
矿是将美元兑换成稳定的USDT放在自己的Trust钱包里,然后参与挖矿,产生固定收入,可以理解为固定利息收入,更何况你不需要做任何加密货币交易
The message translates to:
Mining is to convert US dollars into stable USDT and put them in your own Trust wallet, and then participate in mining to generate fixed income, which can be understood as fixed interest income, not to mention that you do not need to do any cryptocurrency transactions)
Frank questioned this unexpected use of Chinese, but rolled along with the further instructions. He agreed to invest $1,000, and then increase once he felt comfortable with the apps, purchasing an initial deposit of Tether (USDT) from Coinbase. “Vivian” told him it was as safe as leaving money in his bank. But Frank still expressed fear of losing his money, resisting putting the crypto into Trust Wallet, referring to warnings he had seen from his bank about cryptocurrency not being covered by deposit insurance, and recent bank failures:
Frank: If something happens with your money here it’s gone – right? Frank: The FDIC bailed out the accounts in that bank Vivian From German In DC: Impossible, cryptocurrencies are now definitely safer than banks because there is no money at anyone's disposal Frank: So most people didn’t lose any money even though the bank went under Frank: You mean they don’t loan money to people which requires that you pay it back Frank: So they can’t go under Frank: It’s when people can’t pay the money back they owe that the problem start Vivian From German In DC: Your money is in the bank, the bank can take it and lend it to others or use it for investment, but the dominion of your USDT will always be in your hands only Frank: Ok
Frank remained skeptical—how would this make any profit if the crypto stayed in his wallet? The scammer explained:
Vivian From German In DC: This is the same question I had before when I got involved in mining, and you have the same good sense as me. Liquidity mining is a way to earn more digital currency by holding it. It is a magical computer program that lends your money to others through "smart contracts". In return for your services, you earn a fee in the form of digital currency Liquidity mining miners use a very complex strategy. They have to keep moving cryptocurrencies between different lending markets to maximize return earnings. They also keep the best liquidity mining strategy a secret. Why? Because the more people know about a particular strategy, the less effective that strategy will be. Liquidity mining can be seen as the wild west of decentralized finance (DeFi), where farmers only have a chance to grow the best crops by competing with each other Vivian From German In DC: Yes, that's a fixed income of $400 per day for you Vivian From German In DC: By supercomputers to achieve the whole mining process, time will slowly let you learn more Vivian From German In DC: I have to admit that the person who invented cryptocurrency is a genius, so I'm learning more and more
Assured that this was risk-free, Frank finally assented to moving forward. “Vivian” continued to provide “helpful” step-by-step instructions on how to do so, having Frank send screen shots and marking them up with what to tap on next.
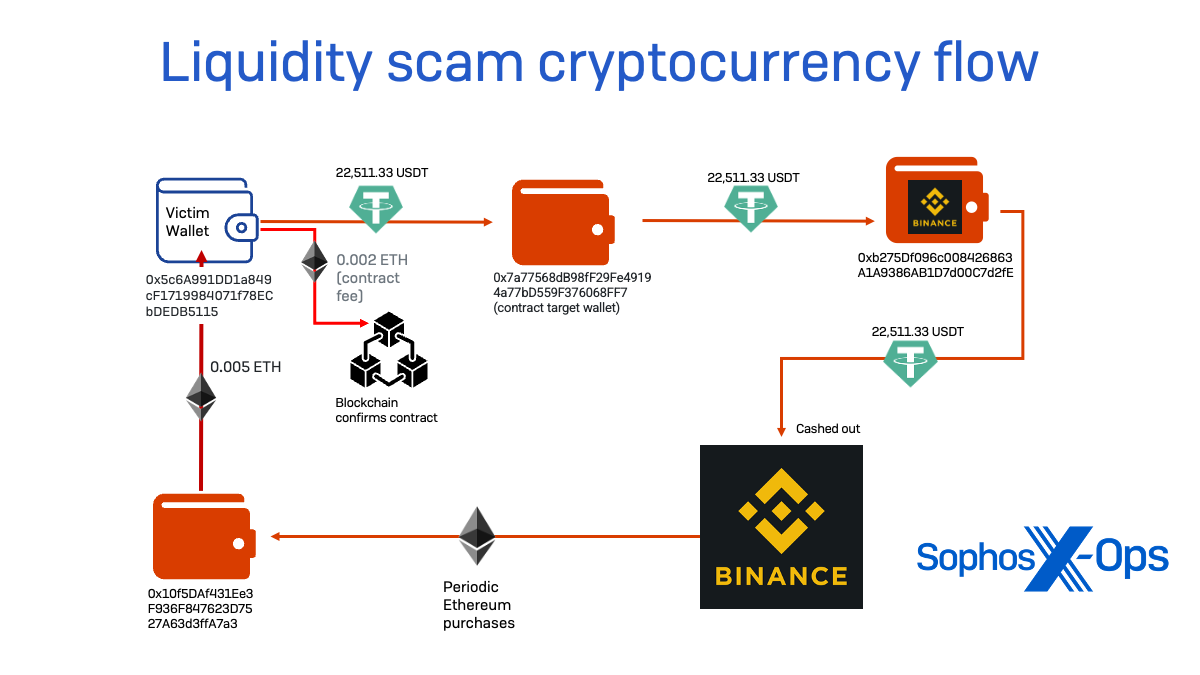
After purchasing the Tether tokens from Coinbase, Frank was then instructed to move them to TrustWallet. And then “Vivian” told Frank to open the (fraudulent) URL of the “mining pool” in the TrustWallet browser. The scammers sent Frank enough Ethereum (about $6 worth) to pay the “gas fee” for sealing the contract on the wallet presented by the fraudulent site.
The wallet that “lent” the victim the Ethereum (ETH) required to pay the “gas” for the contract (0x10f5DAf431Ee3F936F847623D7527A63d3ffA7a3) received the cryptocurrency from the Binance exchange, and had distributed ETH to other addresses to create similar contracts linking to other fraudulent pools. (Details of these will be presented in a future Sophos X-Ops report.)
At this point, Frank loaded the site in Trust Wallet, and used the Ethereum he had been sent to complete “joining the node”—creating a smart contract that gave the scammers full details and access to the Trust Wallet. It was at this point that the scammer’s trap was completely set. The contract transaction granted an “allowance” of 83,076,749,736,557,242,056,487,941,267,521,535 tokens for transfer to the fake pool’s node (0x6B79f38233726282c7F88FE670F871eAbd0c746c) –the maximum that could be set by the contract.
Filling and draining the pool
The pool site, allnodes[.]vip, was a fraud site using the brand of Allnodes, an established decentralized finance platform provider. The fraud site was hosted on an Alibaba Cloud server—now offline. When Frank linked to the malicious DeFi site, it first gave the site access only to view his wallet ID and balance. But clicking a “participate” button in the app executed a contract that authorized the scammers to send Tether tokens from the wallet to another address.
Following instructions, he wired money from his bank to his Coinbase account and a Crypto.com wallet (which he used when his Coinbase account was not getting credited fast enough). Between May 31 and June 5, Frank put a total of more than $22,000 in the scheme (not including the processing fees for wire transfers to exchanges and token purchases).
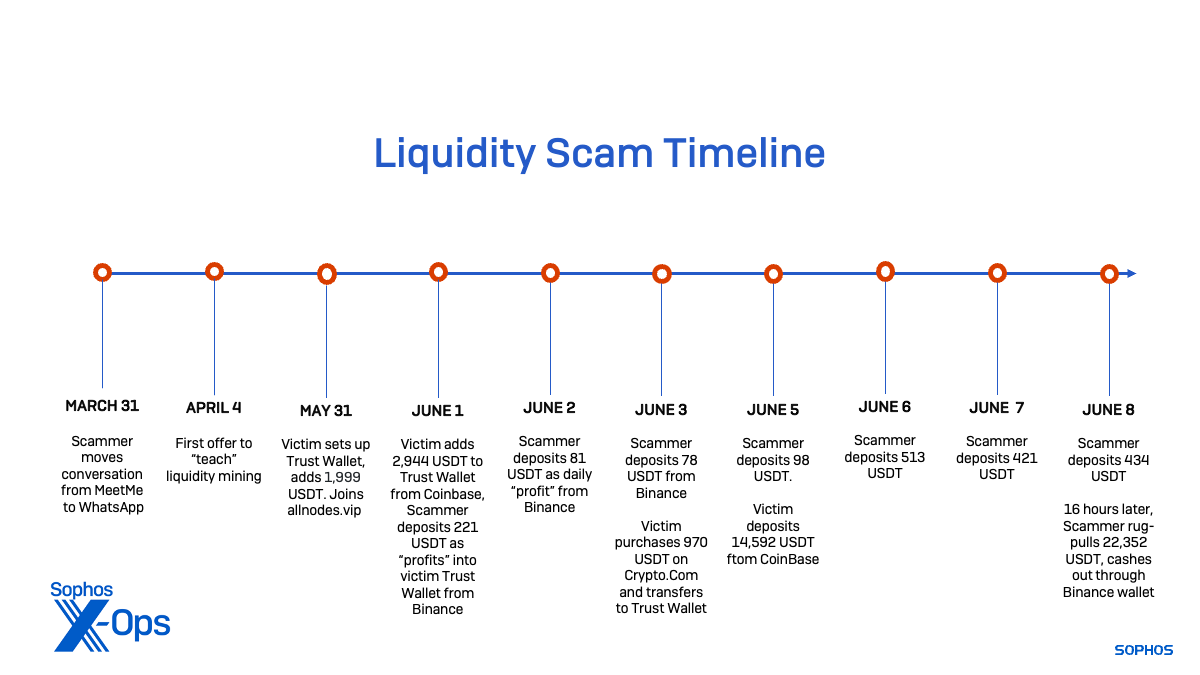
On June 6, the scammer asked the victim if he had made a wire transfer again. “Not yet,” Frank said. “I was busy working around the house. And then I started reading articles on cryptocurrency.” Once again, “Vivian” replied in Chinese:
不需要阅读其他的关于加密货币的文章,因为我们不是做加密货币的投资,我也不希望你参与加密货币的投资
This message translates to: “No need to read other articles about cryptocurrency, because we are not investing in cryptocurrency, and I don’t want you to participate in cryptocurrency investment.”
Frank: Why did you sent me that message in Chinese? Are you Chinese? Vivian From German In DC: Oh, I just found out Frank: Found out what? Vivian From German In DC: I am chatting with a friend of mine in China. Frank: Ok Vivian From German In DC: I use a translator to communicate with him
Later that day, “Vivian” pushed him again to get more funds into the wallet in order to reach the “next level” of returns. Frank mentioned that his bank had sent him a notice warning him about cryptocurrencies after his last wire transfer. “It said that I could lose all of my investment potentially to fraud,” he told “Vivian.” He said he wanted to hold off on buying more USDT for the moment—in part because he had tried contacting Trust Wallet support by phone and ended up calling a fake support number, and now he was receiving text messages with attachments and was concerned that his phone had been compromised.
On the evening of June 8, the scammers used their access to Frank’s wallet to empty it of USDT. The entirety of Frank’s USDT balance was transferred to the address 0x7a77568db98ff29fe49194a77bd559f376068ff7—a transfer address used by the scammers for this part of their campaign that, between May and July, received a total of 294,548.75 USDT, worth about $294,000. Twenty minutes later, the funds were forwarded again, to 0xbe712a28f10ffe6e0efd77b749de133d6099e4c0, a Binance wallet address. And from there, they were cashed out through the Binance exchange. Jackie Burns Koven, head of cyber threat intelligence at Chainalysis, confirmed these findings, identifying the last wallet address as being associated with a Binance account.
(Other Binance wallets were used to cash out funds from other apparent victims of the scam. A list of all scam-related wallets is in the indicators of compromise file linked at the end of this report.)
Frantic to recover his investment, Frank contacted the “technical support” for the scam site, believing he was contacting Trust Wallet support through an in-app chat. But he was actually connecting to the scam team through a chat app on the allnodes[.]vip website that Frank had opened from within Trust Wallet.
He was told that he had enrolled in a “staking” challenge, and that he needed to invest a total of 100,000 USDT to fulfill his enrollment—and when the event ended, he was told, the investment would be released along with his “rewards.” Frank then communicated again with “technical support,” asking to get his funds released. The response he received from the scammers posing as support was:
After checking you did participate in this event. Activity time- After you deposit 100000 USDT you wil receive 5 ETH bonus and your pledge time will be calculated for 30 days, and then you will get 3% of your earnings every day… You are unable to deposit 77,648.35 You will be in default and will be penalized and your money will remain in the pool. If you are having financial difficulties, you tell me the amount you want to participate. I can help you give feedback to your supervisor and request a reduction in the total amount of participation.
Figure 23, 24 and 25: Frank is told by “Gugu” that he’s on the hook now
The scammers negotiated down to accepting another 25,000 USDT for Frank to meet his “stake goal,” and Frank set about trying to gather the funds. Meanwhile, “Vivian” sent reassuring messages with romantic promises to keep Frank on track.
On June 9, a Friday, Frank attempted to wire $25,000 to Coinbase. But on the following Monday, he found he could not access his Coinbase account.
“Vivian” told him to use Crypto.com instead, and on June 13 walked him through getting cryptocurrency through that app. That evening, he received the following email from “Trust Wallet “:
Frank tried wiring $24,000 to Crypto.com on June 14. But his bank blocked the transfer. “I got a phone text and email from my bank,” he told “Vivian.” “They locked me out of my bank account because I sent that wire transfer. Then they told me after questioning me in detail about what exactly I was doing that I needed to go into the local branch and talk to someone. I just came back from doing that and she questioned me and called them and they questioned me more. I have to go back tomorrow to try to wire it manually to the Crypto.com bank. They said that they have to approve the money transfer even though I have the money.”
While waiting for his bank to approve a manual wire transfer, Frank did some Internet research and stumbled upon a news article about liquidity mining scams. “Vivian” warned him against doing more research, while flattering him and reassuring him of their special relationship, and guided him in trying to get funds into a Crypto.com wallet.
But Frank’s research eventually led him to our reports on liquidity mining. On June 15, he reached out to me via LinkedIn, and I began to untangle the lies for him. He soon blocked “Vivian” on WhatsApp, and we worked to help him engage with law enforcement.
But wait, there’s more
The scammers were not through trying to get Frank to send those additional funds. On June 29, “Vivian” used Frank’s phone number to find his Telegram account, and started messaging him there. In the meantime, the block WhatsApp account was changed to “Vivian from Berlin” and the profile image was changed to that of a person of a different gender.
On June 30, “Vivian” sent a “letter” as text in Telegram. The lengthy, flowery text, which had none of the characteristics of previous correspondence, had hallmarks of being the result of generative AI—flowery grammar inconsistent with previous communications, in the format of a “letter,”excerpted below:
I hope this letter finds you well. I wanted to reach out to you because something has been weighing heavily on my heart. Our connection, though not officially established as a romantic relationship, meant a lot to me. The friendship we shared was special, and it brought a certain brightness to my life that I cherished deeply. I've noticed that, for reasons unknown to me, you recently deleted me. This sudden separation has left me confused and with a sense of loss. I never anticipated that our bond would face such a challenge, and it has been difficult for me to comprehend why it happened. However, I am committed to resolving any misunderstandings or issues that may have led to this decision. I want you to know just how much your presence means to me. Your friendship has been a source of comfort, support, and laughter. Through our conversations, shared experiences, and even the unspoken moments, I felt a connection that I haven't found with many others. It touched a deep part of my soul, and I genuinely believed that something beautiful could have blossomed between us…
While there is no definitive way to determine whether this text was AI-generated, the large language model detecting service GPTZero rated it as 100% AI-generated.
Frank blocked “Vivian” on Telegram. But the last lure was still to be cast. On July 13, he received an email claiming to be from “Trust Wallet” <trust.wallet2563@gmail.com>:
Dear users, your participation in the allnodes.vip mining pool Stake campaign will end on July 15, 2023 at 9:46 pm (GMT-4), during which time your mining pool pledge proceeds have been credited. If you have completed the activity amount requirements, you can withdraw your funds or continue to participate in the Stake activity after July 15, 2023, 9:46 (GMT-4)! For more details, please get in touch with customer service.
Frank passed these communications to me and to law enforcement, and is no longer communicating with the scammers. None of the lost cryptocurrency has yet been recovered; law enforcement determined that it had been cashed out to a bank account in Hong Kong.
Plan of action
While engaged in researching this case, we contacted Chainalysis and Coinbase, as well as other threat intelligence professionals in the cryptocurrency space, to share our data. We continue to identify additional domains hosting fake liquidity pool sites based on the same code as this scam, and track other similar liquidity and crypto trading fraud sites used by “pig butchering” actors. And we added the domains associated with these scams to our reputation service for blocking.
However, since these scams are constantly evolving, it’s important to remain on guard against them and to educate people who may be more vulnerable to them about how to identify these types of fraud. People who are isolated, seeking romantic contacts, or are otherwise emotionally vulnerable are more likely to be targeted through meet-up and dating applications, but we’ve seen other services used as well—everything from Facebook and LinkedIn invitations to AirBnB reservation requests.
If someone wants to take the conversation with you to WhatsApp or Telegram to converse outside the scope of an application almost immediately, this is a sign that you may be dealing with a scammer. Text messages that appear to be misdirected and then turn into offers of friendship are another common “lure” for these types of scams.
If you believe you are engaged with a fraudulent “mining pool” app that you have linked to a wallet app, take these steps immediately:
- Break the contract on the wallet by loading the website Revoke (https://revoke.cash/) from within your wallet app or your wallet-connected browser. This will allow you to identify and revoke permissions that have been placed on your wallet. Some Ethereum will be required for “gas” fees to rewrite the permissions.
- Move all funds out of the wallet to another, new wallet, especially if you can’t revoke the contract binding it.
- Contact the exchange you’ve purchased crypto through and the wallet provider. Don’t use in-app “support chat,” as that is most likely controlled by the scammers. If using Trust Wallet, contact the developers through the support website.
- Collect all transaction data associated with your wallet using a block chain explorer such as Etherscan (https://etherscan.io) by pasting your wallet ID number into its search bar; share this information with security teams and (if necessary) law enforcement.
- If you have already lost your funds, do not engage with a “crypto recovery” provider advertised on social media. Most of these services are scams as well.
- Report the activity to local authorities in a position to investigate the fraud. In the United States, the US Secret Service and the FBI investigate crypto fraud, but may not act on individual cases; the Federal Trade Commission may be of assistance in some cases. In the UK, Action Fraud may be of assistance.
- If you’ve been taken in by one of these scams, it’s important that you understand that many other people have fallen for them. In the United States alone, the FBI reports that there were $3.31 billion in losses from these types of investment scams in 2022 alone.
Lastly, if you want to assist us in fighting this type of fraud or other cryptocurrency and trading-based fraud, reach out to me or my colleague Jagadeesh Chandraiah through comments on this post.