Attacker combines phone, email lures into believable, complex attack chain
Credit to Author: Andrew Brandt| Date: Thu, 10 Aug 2023 10:00:10 +0000
[Editor’s note: The details of this investigation will be presented live at Defcon on Friday, August 11 at noon in the War Stories track, in the Las Vegas Harrah’s conference center]
In the course of performing a postmortem investigation of an infected computer, Sophos X-Ops discovered that the attack began with an innocent-sounding phone call. The caller prompted an employee of a Switzerland-based organization to initiate a complex attack chain that compromised the employee’s computer.
Sophos Incident Response analysts found that the attackers may have targeted the call recipient personally, and crafted an elaborate social engineering attack chain that resulted in the attackers taking control of the target’s computer, briefly, before the target literally pulled the (ethernet) plug on the compromised computer. The alert employee sensed something was wrong, and disconnected the infected computer from the network, but not before the malicious payload was already at work.
The caller, whose voice sounded like a middle-aged man, told the employee that he was a delivery driver with an urgent package destined for one of the company locations, but that nobody was there to receive the package, and he asked for a new delivery address at the employee’s office location. In order to redeliver the package, he continued, the employee would have to read aloud a code the shipping company would email.
While the caller was still on the phone with the employee, the employee received an email message, purportedly from the caller’s shipping company. The email message shown below (written in French) said that a PDF file attached to the message contained the code the delivery driver was waiting to hear before they could bring the package to the employee’s location.
Phishing message embeds graphical elements
The message body says that “your documents had been sent by a delivery service that hasn’t had contact with” the destination. It goes on to say that, for reasons of security, delivery isn’t possible unless the target provides the correct code to the shipper, and that the target can only get the code from the attached PDF.

The email also indicates the “shipment” is something that weighs about what a letter would weigh, and that it has “elevated (government agency)” priority.
Despite the fact that the email message was written in the French language, technical clues left behind indicate the attackers knew the Swiss target might be a German speaker. Both are considered “official” Swiss languages. There are German-language comments embedded in the HTML (“Inhalt mit Bild links,” which translates either to “content with picture links” or “content with picture left”) that made up the email message body, which was sent to someone who used Outlook as their mail client.
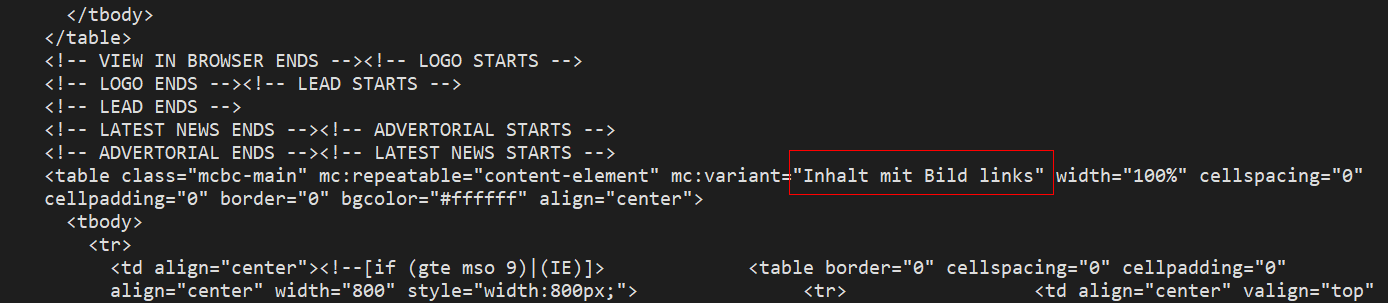
The curious email message triggered the attack chain that followed, but not in the way you might guess. There was no PDF attachment to the message, even though it appeared there was. Below is what the target saw in Outlook.

The employee saw what looked like an Outlook message with a PDF attachment, but it was actually a graphic embedded in the message body, designed to look just like an Outlook message with an email attachment: Both the “attachment” and the accompanying email message were just static images embedded in the message body.
Instead, when the employee clicked where they thought an attachment appeared in the email (or if they clicked anywhere else), they triggered Outlook to visit a website.
This attack mechanism struck our analysts as unusually complex – the phone call urging the target to click the email; the specially crafted email with no text in the body; the attacker-registered website with a customized “delivery” themed domain name used to host a file to download – but the complexity seemed to have purpose.
For one thing, the fact there was no PDF attachment gives the attacker an advantage, since many email systems treat messages carrying such attachments with (appropriate) suspicion when they originate from unusual sources and would either delay the delivery of, or automatically filter, emails with PDF or other office-format attachments.
For another, the attackers also didn’t link directly to the website they controlled hosting malicious code. Instead, they found a webpage redirection script, hosted on a benign website — one that was unlikely to raise suspicion — and linked to that, using the redirection script to navigate the employee’s browser to the malicious website.
The following screenshot shows the HTML source code of the email message, including the link to the benign website (highlighted in green) and how its redirect sent users to the malicious website (highlighted in red).
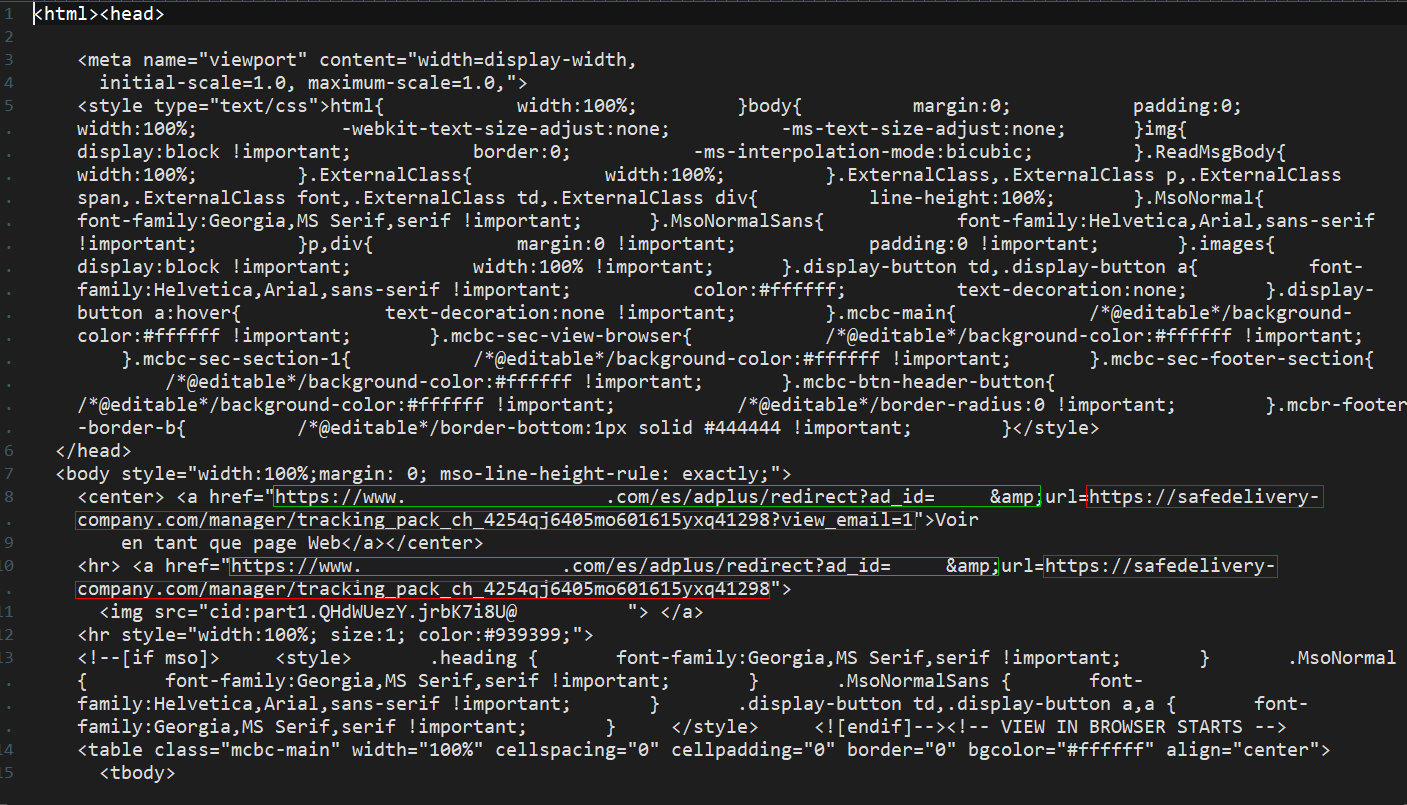
This redirection technique seems to be designed as a method of bypassing URL checking features. Some spam filters or firewalls that block malicious websites might query the URL reputation of the benign site hosting the redirection script — instead of the destination domain, safedelivery-company.com, registered and operated by the attackers and used to host malware. (This same attacker also appears to have used the domain aircourier-company.com at some point in the past.)
Missing information leave intriguing clues to attack
As we were brought in after the attack had taken place, and the attackers in this incident quickly cleaned up their mess, we only had limited information about what happened next.
We know, for instance, that the attackers were successful at convincing the employee to click the “attachment” that opened a link in their browser. The link appears to have delivered malware that ran on the computer, because within a minute of the employee looking at the email, the attackers had begun executing commands on the employee’s computer.
Logs retrieved from the compromised machine indicate, for instance, that an employee clicked the malicious link in the email at 11:16 in the morning, local time. They downloaded an executable file named sendung_N03012_16092022.com and apparently double-clicked it. As a result of that action, another program named SECURE DELIVERY SERVICE.EXE ran on the computer.
At the time we performed the analysis, neither file remained on the infected computer’s storage, and the websites where the files were hosted no longer produced the files when requested. In fact, the websites were hosting a page with some “coming soon” language and a countdown timer that took up most of the page’s real estate.
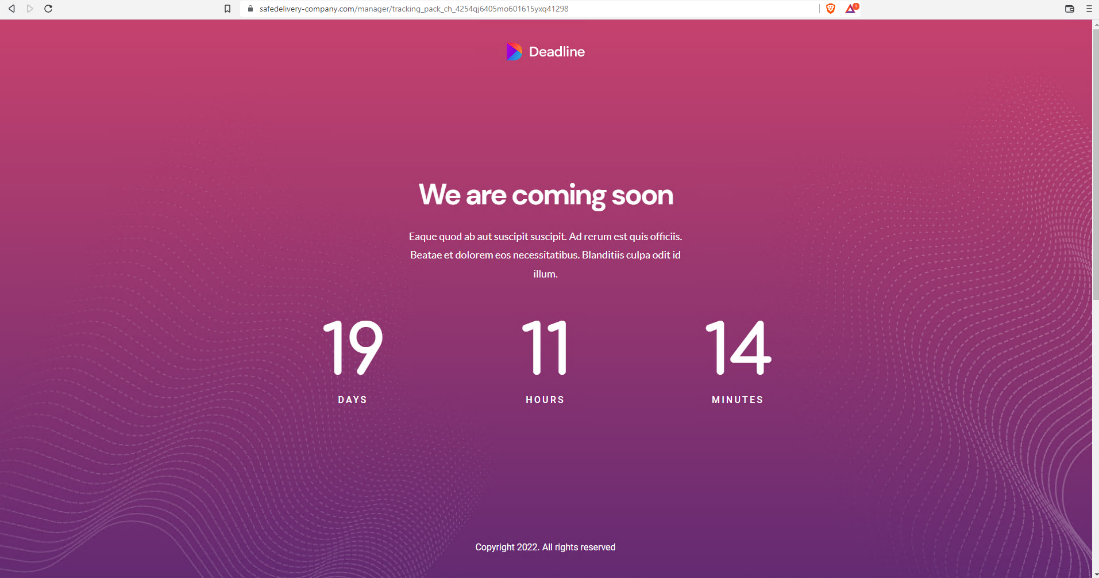
In fact, this is a behavior observed in other malware incidents. The countdown timer resets itself with a random days/hours/minutes value every time you reload the page. The code that runs this page is a ReactJS template called Deadline. The people using this haven’t even bothered to modify the template’s boilerplate lorem ipsum text block.
Recovered malicious scripts hidden in software license file
Over the next 15 minutes of the attack, the attacker downloaded and ran multiple PowerShell scripts, but they had deleted them by the time our analysts were able to look at the affected machines days later.
In the course of looking for data the attackers may have modified or touched, we found traces of the scripts, but also discovered they had employed an unusual method to conceal them in plain sight.
Among the files the attackers did not delete was a folder that contains the text editor Notepad++. The Notepad++ open-source project gives users the choice to download either an installer executable, or a “portable” version in a zip archive that contains all the files necessary to run the program. We found what appears to be a modified “portable” installation in the affected computer. The employee and the organization’s IT team confirmed that they neither use nor installed this software. Its appearance coincided with the attack.
The folder contains everything that normally is included with the official “portable” download, but with a few notable changes: The Notepad++ executable and other executable components (notably, the program’s self-update utility) had been cryptographically signed using a now-revoked signing certificate originally issued to an organization called Cloud Accountants Limited, instead of the still-valid certificate issued to the Notepad++ organization.
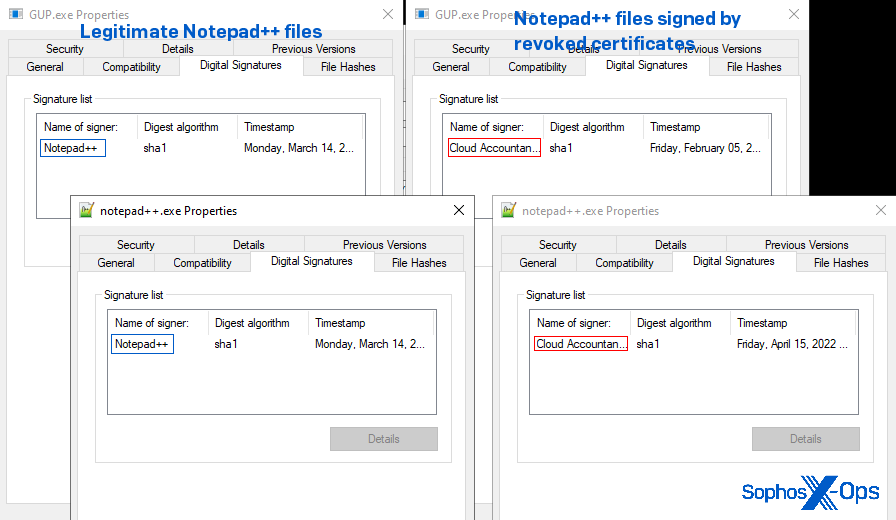
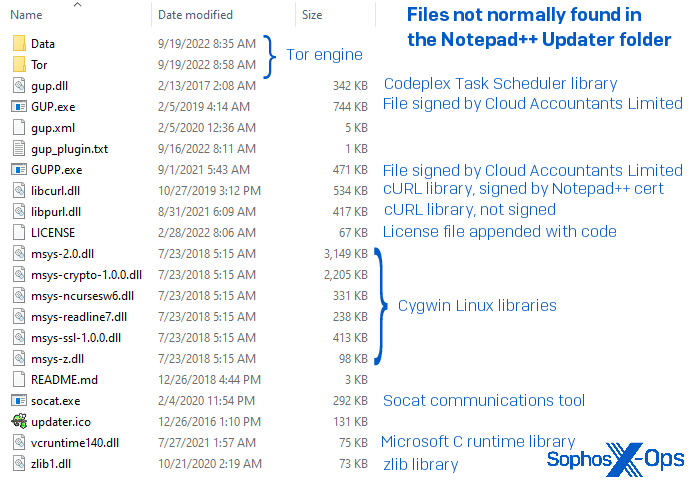
We also found that the folder containing the self-updater in the malicious “portable Notepad++” folder contained 15 additional files not included with the legitimate portable installation zip.
These additional files included a renamed copy of the legitimate DLL Windows uses to create Scheduled Tasks; an unsigned copy of the cURL library named libpurl.dll; a Windows executable version of the (at least, in this case) potentially unwanted Linux app, Socat, whose developers describe it as “a relay for bidirectional data transfers between two independent data channels;” and the minimally required files necessary to open a connection to the Tor network, aka, the “dark web.”
Like many open-source projects, Notepad++ is released under the GNU public software licensing scheme, which requires that developers include a plain text file with the terms of the license agreement. Notepad++ usually includes a plain text file named LICENSE. We also found a LICENSE file on this installation, but someone had appended a blob of base64-encoded data to the document. The normal copy of LICENSE is only 8kb in size; this LICENSE was 59kb larger than the original.
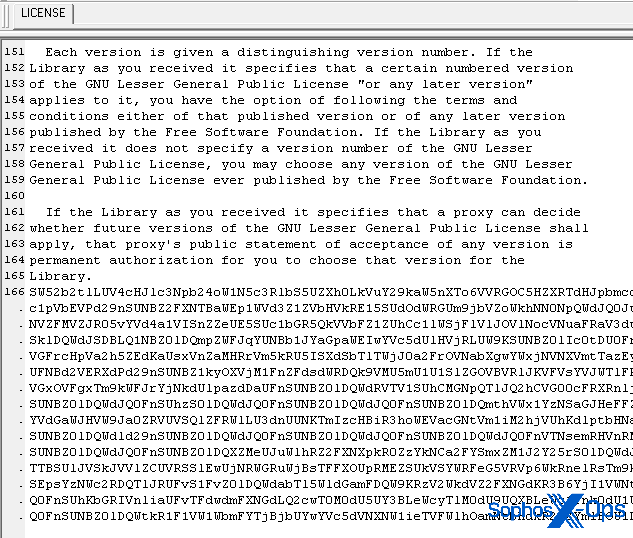
When decoded, this base64 data blob outputs a PowerShell script that consists of three commands. Each command decodes another blob of base64-encoded data and uses the Invoke-Expression command to execute it.
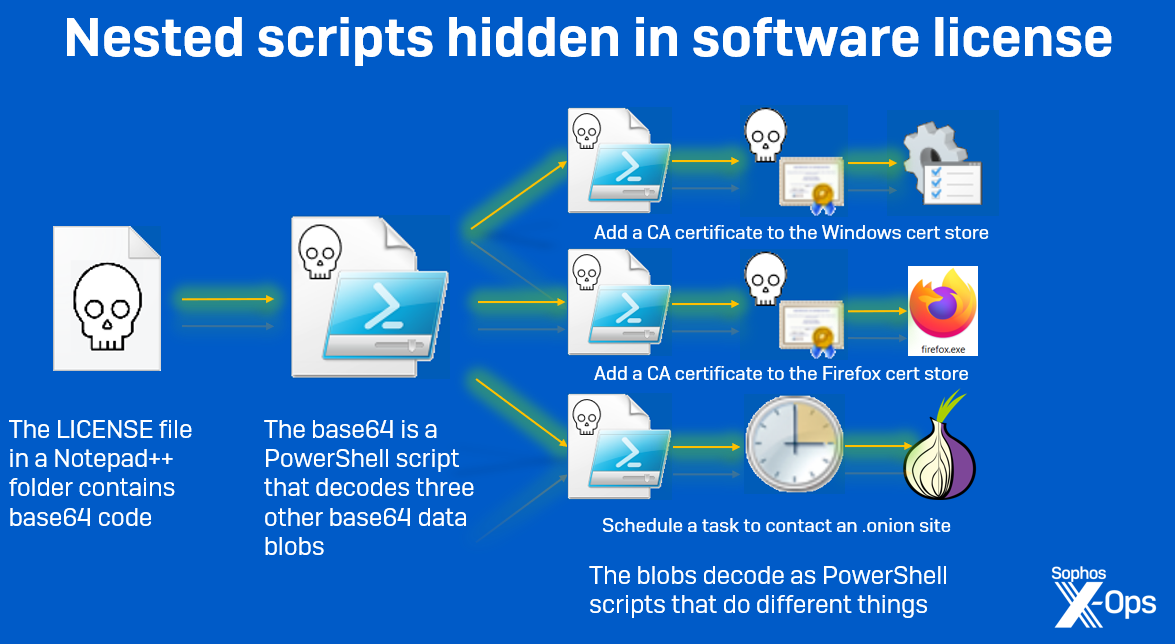
When decoded, the three base64 blobs were three more PowerShell scripts. The first and second script are designed to install an untrusted Certificate Authority Root certificate into the certificate store in Windows, and in Firefox (if it is installed), respectively. (Firefox does not use the Windows certificate storage, but has its own.)
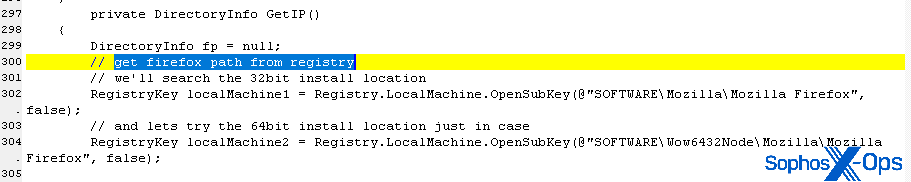
The certificate appears to be crafted to mimic one issued by the legitimate certificate authority Comodo, but was not issued by them.
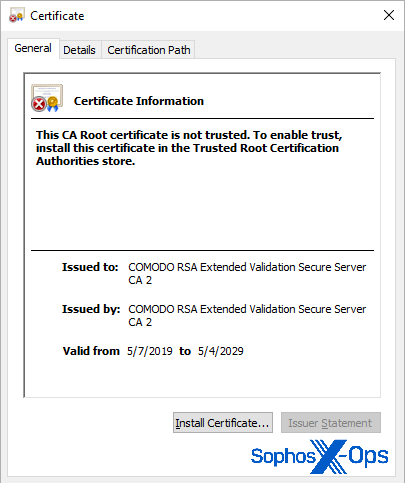
The third script sets up a scheduled task that leverages two programs from the Notepad++ updater folder – GUP.exe and GUPP.exe – to phone home, once a day at midnight (local time), to one of five .onion addresses, randomly chosen from a hardcoded list also embedded in the script.
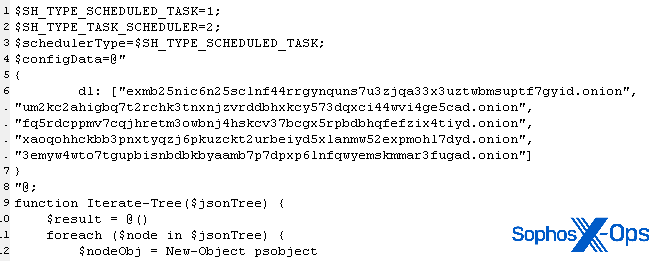
While examining the logs for evidence, we found a fourth PowerShell script left behind (named ms.ps1) where the attackers failed to delete it. This script is a very generalized data collection tool designed to scrape the locations of sensitive data and, optionally, store it to C:ProgramFilesmatches.txt .
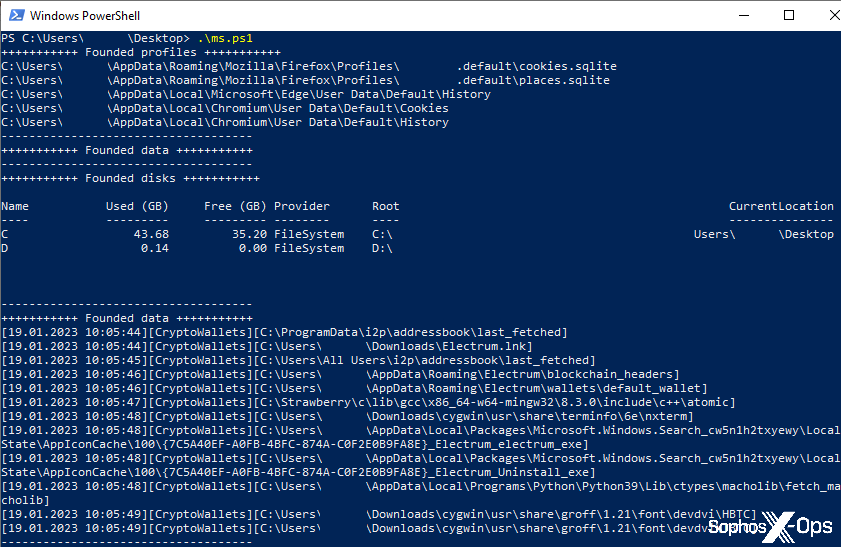
The script looks for system configuration information; accounting software data (such as QuickBooks files); password and cryptocurrency wallets; and the cookies, browsing history, and the list of installed browser plugins from every major web browser platform — Firefox, Opera, Edge, Brave, Chrome, Chromium, Vivaldi, and Tencent’s QQ Browser (mostly used in China).
The script also contains an embedded list of 53 websites. It uses this list to hunt through the scraped browser history and cookie data and add information about which of those websites the browser had visited in the past to the matches.txt file. The target is based in Switzerland, which might explain why the website list included the Swiss-based online retailer Tutti, and 24 websites associated with cryptocurrency companies.
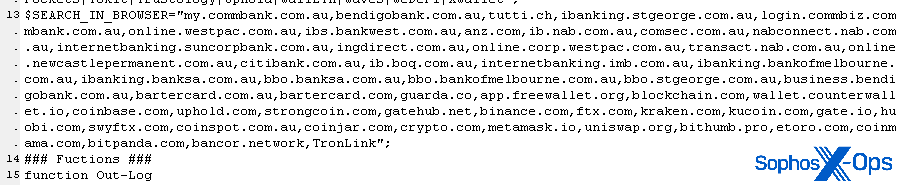
Cookie theft is a growing trend with information stealing malware, since some browser cookies can be as useful for logging in to a secure website as a password.
What’s less clear is why this script includes 25 domains used by banks in the Australia and New Zealand region. But while researching this incident, analysts on the Managed Detection and Response team pointed me to incident notes about an attack against an Australian customer that they investigated in June, 2022.
In the earlier incident, the target of the attack also recorded that a computer had visited URLs on two of the same malicious domains used in this incident – aircourier-company.com and carpoollk.com – and responders found several similar PowerShell scripts, including one that extracted information from the computer, and another that set up a scheduled task to invoke the same, revoked-certificate version of the Notepad++ updater utility discovered in this incident.
Installers found in public repositories
While searching open-source intelligence tools for files related to the collection of malicious files in the Notepad++ directory, we found several files – either zip archives, or installer applications – that contained a virtually identical Notepad++ program directory with the same modified, malicious updater and LICENSE file.
One of the files that had been uploaded to VirusTotal was an Electron app – basically, a set of JavaScript instructions designed to run inside a stripped-down version of the Chromium browser. Not only was this app’s filename (delivery_N03041_07042022.exe) very similar to the one recorded in the logs in this incident(sendung_N03012_16092022.com) and one we serendipitously discovered from a third incident (envoi_N01670_24022022.exe), but the temporary directory it creates to store its running files includes the entire, identical Notepad++ program directory we discovered on the target’s computer.
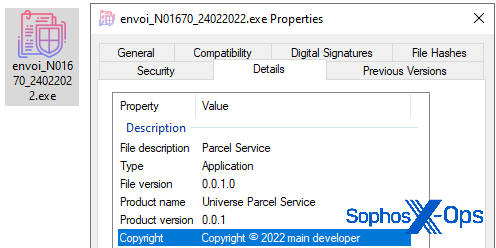
Thematically, the names are close enough to start to see a pattern. The Australian target received one with a name that begins with the word “delivery,” the target in a German-speaking part of the world received one named “sendung” (“shipment”) and a French speaking target received one named “envoi” (“dispatch”). The filenames also include a date that follows the same paradigm of DDMMYYYY.
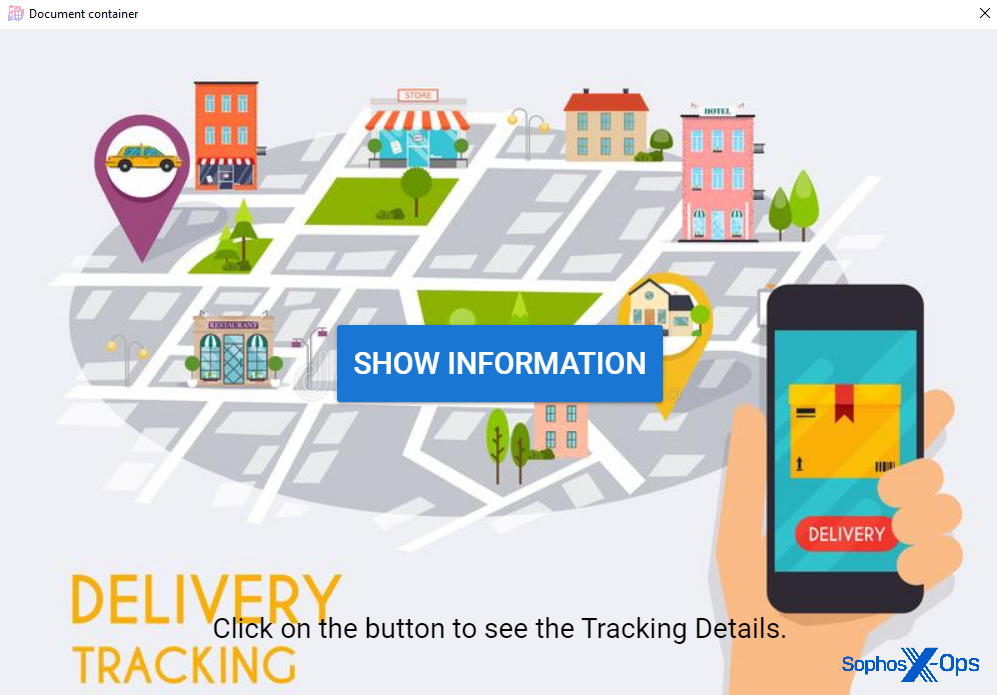
When executed, the Electron app unpacks the Chromium browser files into a temporary directory and launches a program called Universe Parcel Service.exe, which is just a renamed Chromium executable. The app displays a full-screen window centered around a button labeled “Show Information” with the text “Click on the button to see the Tracking Details” at the bottom of the page.
When first executed, the app connects (in the background) to a web service that reports back the public IP address of the computer running the app, and then attempts to connect to a URL of a file hosted in Google Drive. While we captured the connection taking place, the code hosted on Google’s cloud apparently has been disabled and is not functional.
Clicking the “Show Information” button on the app causes the app to pause a few seconds, then display something that is supposed to look like a package tracking number on the screen. The number randomly generates every time you push the button.
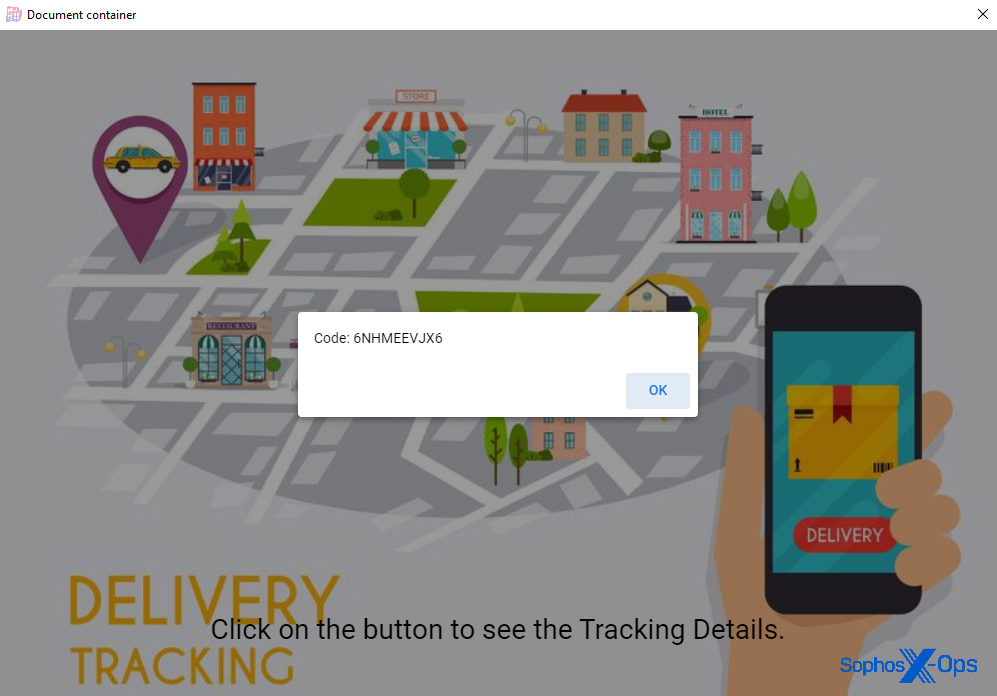
Meanwhile, in the background, the scripts embedded in the Notepad++ LICENSE file begin to run, and the script invokes the Socat utility to open multiple connections to Tor, listening on a variety of high port numbers for inbound traffic.
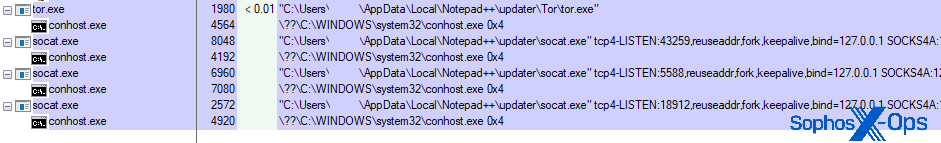
The Notepad++ executables in the archive on VirusTotal were signed with the same revoked certificate used to sign the executables we recovered during the postmortem investigation. Upon closer examination, the content of the decoded scripts originating with the modified LICENSE file found in the VirusTotal sample closely resembled those we recovered from the infected computer. Only the variable names and .onion dark web addresses were changed; the scripts otherwise contained identical instructions.
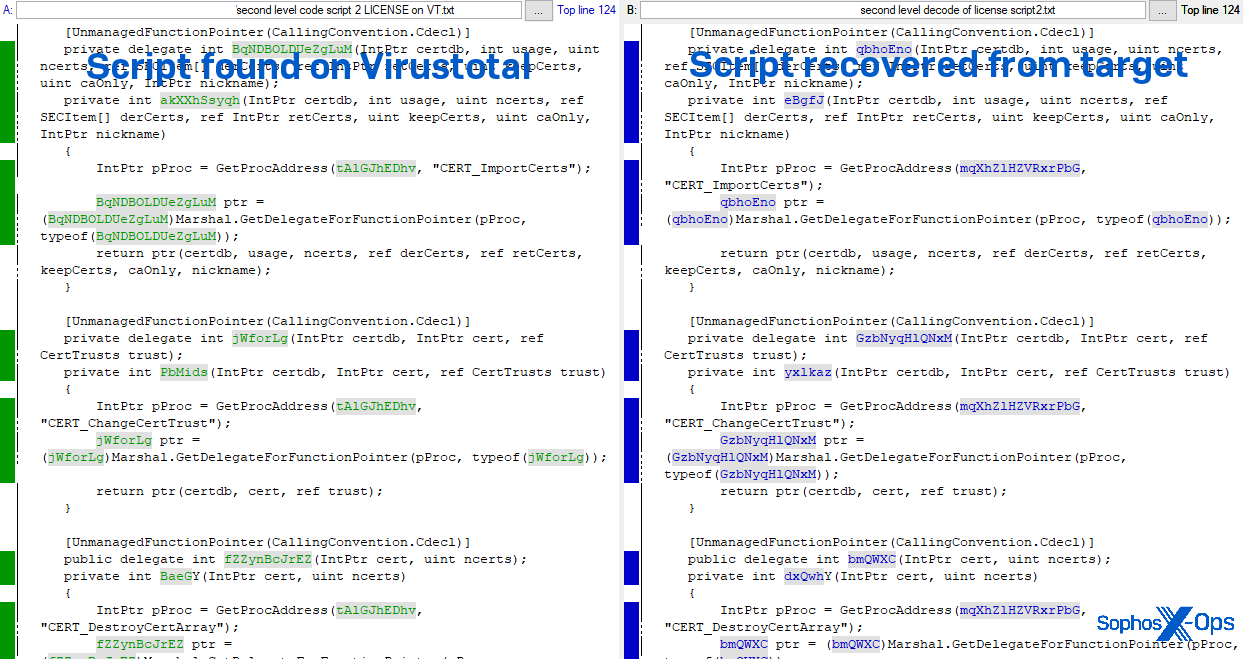
Notably, these scripts from outside sources contained the same, fake Comodo CA certificate found embedded in the scripts on the machine we examined.
Surveillance may be one reason why an attacker would want to install a CA certificate into the system certificate storage: Doing so makes it possible for an attacker to perform a machine-in-the-middle attack and capture the decrypted content of an HTTPS browsing session.
Guidance for anyone who still answers their phone
The employee, watching what was happening on their computer in real time, took the initiative and physically disconnected the affected machine from the network by pulling out the network cable. This left the machine infected but unable to contact or be reached by the attackers, which proved to be potentially an enterprise-saving move, halting the progress of the attack mid-stream. The employee who did this deserves a commendation for their quick thinking, because the attack could have been a lot worse.
The elements of this attack were well-planned and coordinated in advance, involving a human who made a voice telephone call and possibly one or more other people who had built out a variety of malicious Windows Scripting Host and PowerShell scripts, plus the Electron app that delivered and ran them. It’s worth noting that actual voice telephone calls can be part of the social engineering aspect of an attack and, in this case, was used to good effect by the threat actors.
We often give advice about not opening links or attachments sent over email from unfamiliar persons; we don’t usually caution people to be suspicious about those same emails when someone calls you on the phone to tell you to expect the email’s arrival. But if you don’t know the person who’s calling, it’s fair to say that treating such calls with suspicion is a good defensive measure.
Detections and acknowledgments
Sophos X-Ops wishes to thank Incident Response analysts Aaron Short, Bill Kearney, and Ollie Jones for their work on the incident. PowerShell scripts like the ones found in this incident will trigger a detection of Troj/PSDL-OM or Troj/PS-KH in Sophos endpoint products. Indicators of compromise for files in this investigation are listed on the SophosLabs GitHub.