A piñata of patches for Microsoft in August
Credit to Author: Angela Gunn| Date: Wed, 09 Aug 2023 18:28:41 +0000
Microsoft on Tuesday released patches for 73 vulnerabilities, including 3 critical-severity issues in Windows, 2 in Teams, and one in Office. As usual, the largest number of addressed vulnerabilities affect Windows, with 35 CVEs. Office is next in line with 9 issues including one shared with Visual Studio, followed by Azure (7); Exchange (6); .NET (6, including three shared with Visual Studio and .ASP); SharePoint (4); Dynamics 365 and Teams (2 each); and Defender, HEVC Video Extensions, and SQL Server (one each). There are three advisories in this month’s release, and it also includes information on 30 patches for Adobe Acrobat Reader, 12 flaws in Edge/Chromium, and one in GitHub. There is, in addition, information on CVE-2023-20569, the side-channel issue announced today by AMD and affecting multiple CPUs from that manufacturer.
At patch time, two issues are known to be under exploit in the wild. The first, CVE-2023-38180, is a denial-of-service vulnerability affecting .NET, Visual Studio, and .ASP; it requires neither privileges nor user interaction. The other is addressed in a Defense in Depth advisory, ADV230003; this update blocks the attack chain leading to the CVE-2023-36884 vulnerability patched last month. An additional 8 vulnerabilities in Windows, .NET, Visual Studio, and Exchange are by the company’s estimation more likely to be exploited in the 30 days following this release. Four of those 8 issues are kernel vulnerabilities.
Microsoft once again this month offered no guidance overview on exploitation likelihood in earlier versions versus latest versions for any of their patches.
The AMD patch is interesting, since though the flaw is in AMD’s hardware, fixing it requires a Windows update. Microsoft includes information on it so sysadmins are aware that the latest builds of Windows enable the mitigation, and also to provide links to Microsoft’s own Knowledge Base articles for client and Server / Azure Stack HCI customers, and to Microsoft information for those running VMs in Azure. Information available so far indicates that the issue is not under active attack and may not be exploitable remotely.
We are including at the end of this post three appendices listing all Microsoft’s patches, sorted by severity, by predicted exploitability, and by product family. As per Microsoft’s guidance we’ll treat the patches and advisories for Adobe Acrobat Reader, AMD, Chromium / Edge, and GitHub as information-only in the following charts and totals, though we’ve added a chart at the end of the post providing basic information on all 44.
By the numbers
- Total Microsoft CVEs: 73
- Total advisories shipping in update: 3
- Publicly disclosed: 2
- Exploited: 2
- Severity
- Critical: 6
- Important: 67
- Impact
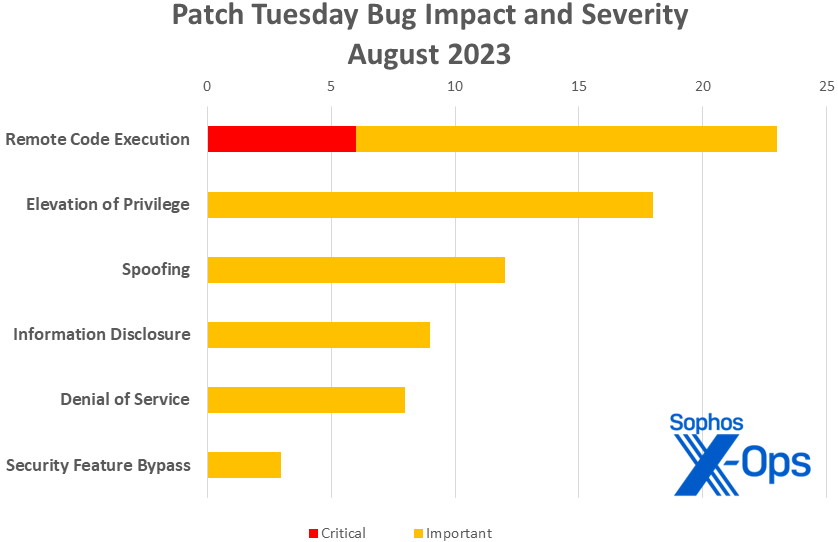
- Remote Code Execution: 23
- Elevation of Privilege: 18
- Spoofing: 12
- Information Disclosure: 9
- Denial of Service: 8
- Security Feature Bypass: 3
Figure 1: Remote code execution issues once again top the charts in August, but spoofing issues in Azure and other products play a big part in the numbers
Products
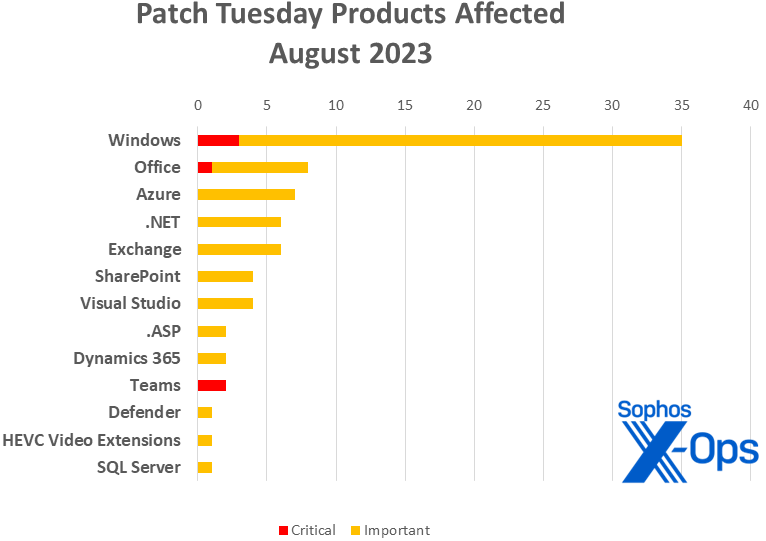
- Windows: 35
- Office: 8 (including one shared with Visual Studio)
- Azure: 7
- .NET: 6 (including two shared with .ASP and three shared with Visual Studio)
- Exchange: 6
- SharePoint: 4
- Visual Studio: 4 (two shared with .NET, one shared with .NET and .ASP, one shared with office)
- .ASP: 2 (shared with .NET)
- Dynamics 365: 2
- Teams: 2
- Defender: 1
- HEVC Video Extensions: 1
- SQL Server: 1
Figure 2: Windows accounts for just under half of this month’s patches, with 13 families represented
Notable August updates
In addition to the AMD patch discussed above, a few interesting items present themselves.
ADV230003 – Microsoft Office Defense in Depth Update
ADV230004 – Memory Integrity System Readiness Scan Tool
ADV990001 – Latest Servicing Stack Updates
There are three advisories this month, and Microsoft describes all three as defense-in-depth issues of moderate severity, as is the custom. However, the first two on the list (ADV230003, ADV230004) both address publicly disclosed issues, with ADV230003 under active exploit in the wild as noted above. The other affects Microsoft’s Memory Integrity System Readiness Scan Tool, which checks compatibility in hypervisor code for ARM64 and AMD64 processors and is also sometimes called HVCI. The third is of course the regularly updated servicing stack, which is always a good choice for prioritized installation.
CVE-2023-38180 – .NET and Visual Studio Denial of Service Vulnerability
More .NET / VS / .ASP excitement, this bug affects versions 17.2, 17.4, and 17.6 of VS 2022 along with versions 6.0 and 7.0 of .NET Core. Despite the CVE’s title, .ASP.NET Core 2 is also affected. As noted above, it was recently found to be under active exploit.
CVE-2023-36895 – Microsoft Outlook Remote Code Execution Vulnerability
CVE-2023-36896 – Microsoft Excel Remote Code Execution Vulnerability
CVE-2023-35371 – Microsoft Office Remote Code Execution Vulnerability
All these issues – the Outlook bug Critical-class, the Office bug Important-class – affect Mac users, but those versions of the patches weren’t made available immediately. Administrators of affected systems are encouraged to monitor Microsoft communications for updates to the individual CVEs (CVE-2023-36895, CVE-2023-36896, CVE-2023-35371).
CVE-2023-36876 – Reliability Analysis Metrics Calculation (RacTask) Elevation of Privilege Vulnerability
CVE-2023-35379 – Reliability Analysis Metrics Calculation Engine (RACEng) Elevation of Privilege Vulnerability
Running Windows Server 2008 R2 x64 pack 1, a package old enough to enter middle school this year? These two updates are specifically for you (and no other version of Windows). Both are marked as Important-class elevation of privilege issues, though the wording of the information on the former (“an attacker who successfully exploits this vulnerability cannot access existing files but can write or overwrite file contents, which potentially may cause the system to become unavailable”) sounds very DoS-like in a way.
CVE-2023-35380 – Windows Kernel Elevation of Privilege Vulnerability
CVE-2023-35382 – Windows Kernel Elevation of Privilege Vulnerability
These two elevation-of-privilege issues share a name and a warning that they’re more likely to be exploited in the 30 days following patch release. However, a reading of the information provided shows a small silver lining: Both require local access to the targeted machine. (Once touching the keyboard, though, the would-be attacker would exploit this by creating folders and performance trace on the box, both of which require privileges users have by default. We said it was a small silver lining.)
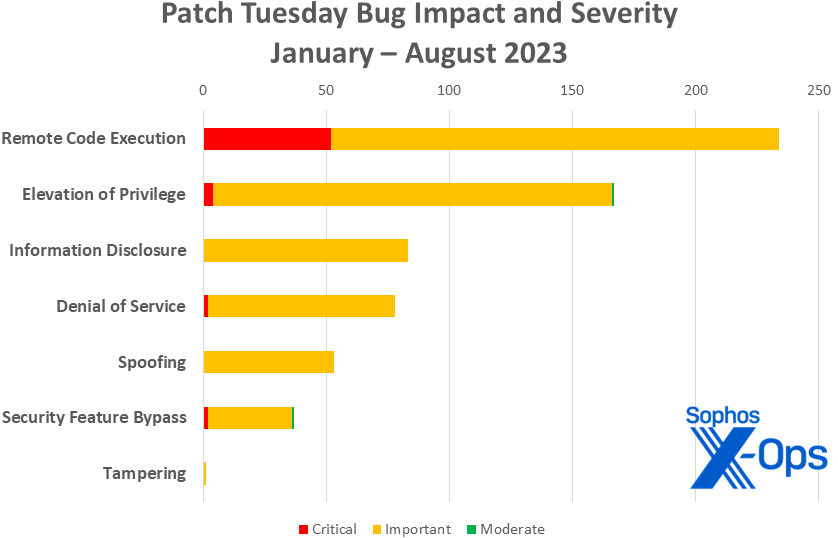
Figure 3: The cumulative 2023 total through August’s Patch Tuesday. It may not feel like it, but 2023 to date is a far lighter year than 2022 according to our numbers. At this point in 2022, Microsoft had released 690 patches, including 52 Critical-class patches. Elevation of Privilege led the list with 274 patches. In contrast, this year’s total patch load has been 491 patches, including 60 Critical-class; Remote Control Execution issues lead the pack with 234
Sophos protections
As you can every month, if you don’t want to wait for your system to pull down Microsoft’s updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your specific system’s architecture and build number.
Appendix A: Vulnerability Impact and Severity
This is a list of August’s patches sorted by impact, then sub-sorted by severity. Each list is further arranged by CVE.
Remote Code Execution (23 CVEs)
| Critical severity | |
| CVE-2023-29328 | Microsoft Teams Remote Code Execution Vulnerability |
| CVE-2023-29330 | Microsoft Teams Remote Code Execution Vulnerability |
| CVE-2023-35385 | Microsoft Message Queuing Remote Code Execution Vulnerability |
| CVE-2023-36895 | Microsoft Outlook Remote Code Execution Vulnerability |
| CVE-2023-36910 | Microsoft Message Queuing Remote Code Execution Vulnerability |
| CVE-2023-36911 | Microsoft Message Queuing Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2023-35368 | Microsoft Exchange Remote Code Execution Vulnerability |
| CVE-2023-35371 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2023-35372 | Microsoft Office Visio Remote Code Execution Vulnerability |
| CVE-2023-35381 | Windows Fax Service Remote Code Execution Vulnerability |
| CVE-2023-35388 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| CVE-2023-35389 | Microsoft Dynamics 365 On-Premises Remote Code Execution Vulnerability |
| CVE-2023-35390 | .NET and Visual Studio Remote Code Execution Vulnerability |
| CVE-2023-36865 | Microsoft Office Visio Remote Code Execution Vulnerability |
| CVE-2023-36866 | Microsoft Office Visio Remote Code Execution Vulnerability |
| CVE-2023-36882 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability |
| CVE-2023-36896 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2023-36898 | Tablet Windows User Interface Application Core Remote Code Execution Vulnerability |
| CVE-2023-38169 | Microsoft OLE DB Remote Code Execution Vulnerability |
| CVE-2023-38170 | HEVC Video Extensions Remote Code Execution Vulnerability |
| CVE-2023-38182 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| CVE-2023-38184 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability |
| CVE-2023-38185 | Microsoft Exchange Server Remote Code Execution Vulnerability |
Elevation of Privilege (18 CVEs)
| Important severity | |
| CVE-2023-21709 | Microsoft Exchange Server Elevation of Privilege Vulnerability |
| CVE-2023-35359 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-35378 | Windows Projected File System Elevation of Privilege Vulnerability |
| CVE-2023-35379 | Reliability Analysis Metrics Calculation Engine (RACEng) Elevation of Privilege Vulnerability |
| CVE-2023-35380 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-35382 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-35386 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-35387 | Windows Bluetooth A2DP driver Elevation of Privilege Vulnerability |
| CVE-2023-36876 | Reliability Analysis Metrics Calculation (RacTask) Elevation of Privilege Vulnerability |
| CVE-2023-36899 | ASP.NET Elevation of Privilege Vulnerability |
| CVE-2023-36900 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2023-36903 | Windows System Assessment Tool Elevation of Privilege Vulnerability |
| CVE-2023-36904 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2023-38154 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-38167 | Microsoft Dynamics Business Central Elevation Of Privilege Vulnerability |
| CVE-2023-38175 | Microsoft Windows Defender Elevation of Privilege Vulnerability |
| CVE-2023-38176 | Azure Arc-Enabled Servers Elevation of Privilege Vulnerability |
| CVE-2023-38186 | Windows Mobile Device Management Elevation of Privilege Vulnerability |
Spoofing (12 CVEs)
| Important severity | |
| CVE-2023-35393 | Azure Apache Hive Spoofing Vulnerability |
| CVE-2023-35394 | Azure HDInsight Jupyter Notebook Spoofing Vulnerability |
| CVE-2023-36869 | Azure DevOps Server Spoofing Vulnerability |
| CVE-2023-36873 | .NET Framework Spoofing Vulnerability |
| CVE-2023-36877 | Azure Apache Oozie Spoofing Vulnerability |
| CVE-2023-36881 | Azure Apache Ambari Spoofing Vulnerability |
| CVE-2023-36891 | Microsoft SharePoint Server Spoofing Vulnerability |
| CVE-2023-36892 | Microsoft SharePoint Server Spoofing Vulnerability |
| CVE-2023-36893 | Microsoft Outlook Spoofing Vulnerability |
| CVE-2023-36897 | Visual Studio Tools for Office Runtime Spoofing Vulnerability |
| CVE-2023-38181 | Microsoft Exchange Server Spoofing Vulnerability |
| CVE-2023-38188 | Azure Apache Hadoop Spoofing Vulnerability |
Information Disclosure (9 CVEs)
| Important severity | |
| CVE-2023-35383 | Microsoft Message Queuing Information Disclosure Vulnerability |
| CVE-2023-35391 | ASP.NET Core SignalR and Visual Studio Information Disclosure Vulnerability |
| CVE-2023-36890 | Microsoft SharePoint Server Information Disclosure Vulnerability |
| CVE-2023-36894 | Microsoft SharePoint Server Information Disclosure Vulnerability |
| CVE-2023-36905 | Windows Wireless Wide Area Network Service (WwanSvc) Information Disclosure Vulnerability |
| CVE-2023-36906 | Windows Cryptographic Services Information Disclosure Vulnerability |
| CVE-2023-36907 | Windows Cryptographic Services Information Disclosure Vulnerability |
| CVE-2023-36908 | Windows Hyper-V Information Disclosure Vulnerability |
| CVE-2023-36913 | Microsoft Message Queuing Information Disclosure Vulnerability |
Denial of Service (8 CVEs)
| Important severity | |
| CVE-2023-35376 | Microsoft Message Queuing Denial of Service Vulnerability |
| CVE-2023-35377 | Microsoft Message Queuing Denial of Service Vulnerability |
| CVE-2023-36909 | Microsoft Message Queuing Denial of Service Vulnerability |
| CVE-2023-36912 | Microsoft Message Queuing Denial of Service Vulnerability |
| CVE-2023-38172 | Microsoft Message Queuing Denial of Service Vulnerability |
| CVE-2023-38178 | .NET Core and Visual Studio Denial of Service Vulnerability |
| CVE-2023-38180 | .NET and Visual Studio Denial of Service Vulnerability |
| CVE-2023-38254 | Microsoft Message Queuing Denial of Service Vulnerability |
Security Feature Bypass (3 CVEs)
| Important severity | |
| CVE-2023-35384 | Windows HTML Platforms Security Feature Bypass Vulnerability |
| CVE-2023-36889 | Windows Group Policy Security Feature Bypass Vulnerability |
| CVE-2023-36914 | Windows Smart Card Resource Management Server Security Feature Bypass Vulnerability |
Appendix B: Exploitability
This is a list of the August CVEs judged by Microsoft to be more likely to be exploited in the wild within the first 30 days post-release, as well as those already known to be under exploit. Each list is further arranged by CVE. (As a reminder, ADV230003, an advisory, is also known to be under active exploit as discussed above.)
| Exploitation detected | |
| CVE-2023-38180 | .NET and Visual Studio Denial of Service Vulnerability |
| Exploitation more likely | |
| CVE-2023-35359 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-35380 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-35382 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-35384 | Windows HTML Platforms Security Feature Bypass Vulnerability |
| CVE-2023-35386 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-35388 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| CVE-2023-36900 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2023-38182 | Microsoft Exchange Server Remote Code Execution Vulnerability |
Appendix C: Products Affected
This is a list of August’s patches sorted by product family, then sub-sorted by severity. Each list is further arranged by CVE.
Windows (35 CVEs)
| Critical severity | |
| CVE-2023-35385 | Microsoft Message Queuing Remote Code Execution Vulnerability |
| CVE-2023-36910 | Microsoft Message Queuing Remote Code Execution Vulnerability |
| CVE-2023-36911 | Microsoft Message Queuing Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2023-35359 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-35376 | Microsoft Message Queuing Denial of Service Vulnerability |
| CVE-2023-35377 | Microsoft Message Queuing Denial of Service Vulnerability |
| CVE-2023-35378 | Windows Projected File System Elevation of Privilege Vulnerability |
| CVE-2023-35379 | Reliability Analysis Metrics Calculation Engine (RACEng) Elevation of Privilege Vulnerability |
| CVE-2023-35380 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-35381 | Windows Fax Service Remote Code Execution Vulnerability |
| CVE-2023-35382 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-35383 | Microsoft Message Queuing Information Disclosure Vulnerability |
| CVE-2023-35384 | Windows HTML Platforms Security Feature Bypass Vulnerability |
| CVE-2023-35386 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-35387 | Windows Bluetooth A2DP driver Elevation of Privilege Vulnerability |
| CVE-2023-36876 | Reliability Analysis Metrics Calculation (RacTask) Elevation of Privilege Vulnerability |
| CVE-2023-36882 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability |
| CVE-2023-36889 | Windows Group Policy Security Feature Bypass Vulnerability |
| CVE-2023-36898 | Tablet Windows User Interface Application Core Remote Code Execution Vulnerability |
| CVE-2023-36900 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2023-36903 | Windows System Assessment Tool Elevation of Privilege Vulnerability |
| CVE-2023-36904 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2023-36905 | Windows Wireless Wide Area Network Service (WwanSvc) Information Disclosure Vulnerability |
| CVE-2023-36906 | Windows Cryptographic Services Information Disclosure Vulnerability |
| CVE-2023-36907 | Windows Cryptographic Services Information Disclosure Vulnerability |
| CVE-2023-36908 | Windows Hyper-V Information Disclosure Vulnerability |
| CVE-2023-36909 | Microsoft Message Queuing Denial of Service Vulnerability |
| CVE-2023-36912 | Microsoft Message Queuing Denial of Service Vulnerability |
| CVE-2023-36913 | Microsoft Message Queuing Information Disclosure Vulnerability |
| CVE-2023-36914 | Windows Smart Card Resource Management Server Security Feature Bypass Vulnerability |
| CVE-2023-38154 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-38172 | Microsoft Message Queuing Denial of Service Vulnerability |
| CVE-2023-38184 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability |
| CVE-2023-38186 | Windows Mobile Device Management Elevation of Privilege Vulnerability |
| CVE-2023-38254 | Microsoft Message Queuing Denial of Service Vulnerability |
Office (8 CVEs)
| Critical severity | |
| CVE-2023-36895 | Microsoft Outlook Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2023-35371 | Microsoft Office Remote Code Execution Vulnerability |
| CVE-2023-35372 | Microsoft Office Visio Remote Code Execution Vulnerability |
| CVE-2023-36865 | Microsoft Office Visio Remote Code Execution Vulnerability |
| CVE-2023-36866 | Microsoft Office Visio Remote Code Execution Vulnerability |
| CVE-2023-36893 | Microsoft Outlook Spoofing Vulnerability |
| CVE-2023-36896 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2023-36897 | Visual Studio Tools for Office Runtime Spoofing Vulnerability |
Azure (7 CVEs)
| Important severity | |
| CVE-2023-38176 | Azure Arc-Enabled Servers Elevation of Privilege Vulnerability |
| CVE-2023-36869 | Azure DevOps Server Spoofing Vulnerability |
| CVE-2023-35393 | Azure Apache Hive Spoofing Vulnerability |
| CVE-2023-35394 | Azure HDInsight Jupyter Notebook Spoofing Vulnerability |
| CVE-2023-36877 | Azure Apache Oozie Spoofing Vulnerability |
| CVE-2023-36881 | Azure Apache Ambari Spoofing Vulnerability |
| CVE-2023-38188 | Azure Apache Hadoop Spoofing Vulnerability |
.NET (6 CVEs)
| Important severity | |
| CVE-2023-35390 | .NET and Visual Studio Remote Code Execution Vulnerability |
| CVE-2023-36873 | .NET Framework Spoofing Vulnerability |
| CVE-2023-36899 | ASP.NET Elevation of Privilege Vulnerability |
| CVE-2023-38178 | .NET Core and Visual Studio Denial of Service Vulnerability |
| CVE-2023-35391 | ASP.NET Core SignalR and Visual Studio Information Disclosure Vulnerability |
| CVE-2023-38180 | .NET and Visual Studio Denial of Service Vulnerability |
Exchange (6 CVEs)
| Important severity | |
| CVE-2023-21709 | Microsoft Exchange Server Elevation of Privilege Vulnerability |
| CVE-2023-35368 | Microsoft Exchange Remote Code Execution Vulnerability |
| CVE-2023-35388 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| CVE-2023-38181 | Microsoft Exchange Server Spoofing Vulnerability |
| CVE-2023-38182 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| CVE-2023-38185 | Microsoft Exchange Server Remote Code Execution Vulnerability |
SharePoint (4 CVEs)
| Important severity | |
| CVE-2023-36890 | Microsoft SharePoint Server Information Disclosure Vulnerability |
| CVE-2023-36891 | Microsoft SharePoint Server Spoofing Vulnerability |
| CVE-2023-36892 | Microsoft SharePoint Server Spoofing Vulnerability |
| CVE-2023-36894 | Microsoft SharePoint Server Information Disclosure Vulnerability |
Visual Studio (4 CVEs)
| Important severity | |
| CVE-2023-35391 | ASP.NET Core SignalR and Visual Studio Information Disclosure Vulnerability |
| CVE-2023-36897 | Visual Studio Tools for Office Runtime Spoofing Vulnerability |
| CVE-2023-38178 | .NET Core and Visual Studio Denial of Service Vulnerability |
| CVE-2023-38180 | .NET and Visual Studio Denial of Service Vulnerability |
.ASP (2 CVEs)
| Important severity | |
| CVE-2023-35391 | ASP.NET Core SignalR and Visual Studio Information Disclosure Vulnerability |
| CVE-2023-38180 | .NET and Visual Studio Denial of Service Vulnerability |
Dynamics 365 (2 CVE)
| Important severity | |
| CVE-2023-35389 | Microsoft Dynamics 365 On-Premises Remote Code Execution Vulnerability |
| CVE-2023-38167 | Microsoft Dynamics Business Central Elevation Of Privilege Vulnerability |
Teams (2 CVE)
| Critical severity | |
| CVE-2023-29328 | Microsoft Teams Remote Code Execution Vulnerability |
| CVE-2023-29330 | Microsoft Teams Remote Code Execution Vulnerability |
Defender (1 CVE)
| Important severity | |
| CVE-2023-38175 | Microsoft Windows Defender Elevation of Privilege Vulnerability |
HEVC Video Extensions (1 CVE)
| Important severity | |
| CVE-2023-38170 | HEVC Video Extensions Remote Code Execution Vulnerability |
SQL Server (1 CVE)
| Important severity | |
| CVE-2023-38169 | Microsoft OLE DB Remote Code Execution Vulnerability |
Appendix D: Other Products
This is a list of advisories and third-party patches covered in the August Microsoft release, sorted by product group.
Adobe Acrobat Reader (30 issues)
| CVE-2023-29303 | Use After Free (CWE-416) |
| CVE-2023-29299 | Improper Input Validation (CWE-20) |
| CVE-2023-29320 | Improper Access Control (CWE-284) |
| CVE-2023-38222 | Use After Free (CWE-416) |
| CVE-2023-38223 | Access of Uninitialized Pointer (CWE-824) |
| CVE-2023-38224 | Use After Free (CWE-416) |
| CVE-2023-38225 | Use After Free (CWE-416) |
| CVE-2023-38226 | Access of Uninitialized Pointer (CWE-824) |
| CVE-2023-38227 | Use After Free (CWE-416) |
| CVE-2023-38228 | Use After Free (CWE-416) |
| CVE-2023-38229 | Out-of-bounds Read (CWE-125) |
| CVE-2023-38230 | Use After Free (CWE-416) |
| CVE-2023-38231 | Out-of-bounds Write (CWE-787) |
| CVE-2023-38232 | Out-of-bounds Read (CWE-125) |
| CVE-2023-38233 | Out-of-bounds Write (CWE-787) |
| CVE-2023-38234 | Access of Uninitialized Pointer (CWE-824) |
| CVE-2023-38235 | Out-of-bounds Read (CWE-125) |
| CVE-2023-38236 | Out-of-bounds Read (CWE-125) |
| CVE-2023-38237 | Out-of-bounds Read (CWE-125) |
| CVE-2023-38238 | Use After Free (CWE-416) |
| CVE-2023-38239 | Out-of-bounds Read (CWE-125) |
| CVE-2023-38240 | Out-of-bounds Read (CWE-125) |
| CVE-2023-38241 | Out-of-bounds Read (CWE-125) |
| CVE-2023-38242 | Out-of-bounds Read (CWE-125) |
| CVE-2023-38243 | Use After Free (CWE-416) |
| CVE-2023-38244 | Out-of-bounds Read (CWE-125) |
| CVE-2023-38245 | Improper Input Validation (CWE-20) |
| CVE-2023-38246 | Access of Uninitialized Pointer (CWE-824) |
| CVE-2023-38247 | Out-of-bounds Read (CWE-125) |
| CVE-2023-38248 | Out-of-bounds Read (CWE-125) |
AMD (one issue)
| CVE-2023-20569 | CVE-2023-20569 Return Address Predictor |
Chromium / Edge (12 issues)
| CVE-2023-4068 | Chromium: CVE-2023-4068 Type Confusion in V8 |
| CVE-2023-4069 | Chromium: CVE-2023-4069 Type Confusion in V8 |
| CVE-2023-4070 | Chromium: CVE-2023-4070 Type Confusion in V8 |
| CVE-2023-4071 | Chromium: CVE-2023-4071 Heap buffer overflow in Visuals |
| CVE-2023-4072 | Chromium: CVE-2023-4072 Out of bounds read and write in WebGL |
| CVE-2023-4073 | Chromium: CVE-2023-4073 Out of bounds memory access in ANGLE |
| CVE-2023-4074 | Chromium: CVE-2023-4074 Use after free in Blink Task Scheduling |
| CVE-2023-4075 | Chromium: CVE-2023-4075 Use after free in Cast |
| CVE-2023-4076 | Chromium: CVE-2023-4076 Use after free in WebRTC |
| CVE-2023-4077 | Chromium: CVE-2023-4077 Insufficient data validation in Extensions |
| CVE-2023-4078 | Chromium: CVE-2023-4078 Inappropriate implementation in Extensions |
| CVE-2023-38157 | Microsoft Edge (Chromium-based) Security Feature Bypass Vulnerability |
GitHub (one issue)
| CVE-2023-35945 | Github: CBL Mariner |