Blocking attacks against Windows “CTF” vulnerabilities
Credit to Author: Mark Loman| Date: Thu, 22 Aug 2019 16:53:35 +0000
Operating systems and run-time environments typically provide some form of isolation between applications. For example, Windows runs each application in a separate process. This isolation stops code running in one application from adversely affecting other, unrelated applications.
This means a non-administrative user mode process can’t access or tamper with kernel code and data, and an unauthorized user mode process can’t dig into the code and data of another process.
But it turns out that Windows process isolation is imperfect, thanks to an undocumented and buggy component known only as “CTF”, part of the Windows Text Services Framework (TSF), that is present in all versions right back to Windows XP.
The dated code and insecure design of this subsystem allows a non-administrative, unauthorized attacker to hijack any Windows process – including applications running in a sandbox like AppContainer – and to gain full admin rights.
This design flaw in CTF was discovered and exploited by Google Project Zero researcher Tavis Ormandy, who wrote an in-depth blog article about his findings.
Designated CVE-2019-1162, Ormandy’s attack is what’s known as an Elevation of Privilege (EoP) vulnerability.
That means it doesn’t allow attackers to break into computers in the first place – to exploit this weakness, an attacker must already have got in, perhaps by using credentials stolen from another computer, by exploiting a remote code execution vulnerability, or by tricking the user into opening a booby-trapped document or running malicious software (malware).
Nevertheless – even though Sophos Intercept X already stops attackers getting this initial foothold, and even though the CVE-2019-1162 bug has already been patched by Microsoft – we expect adversaries to try to find additional weakness in CTF, taking advantage of the attack surface that stems from CTF’s old and insecure design.
So, the Sophos Threat Mitigation team has developed a system-level exploit mitigation that prevents abuse of the CTF subsystem.
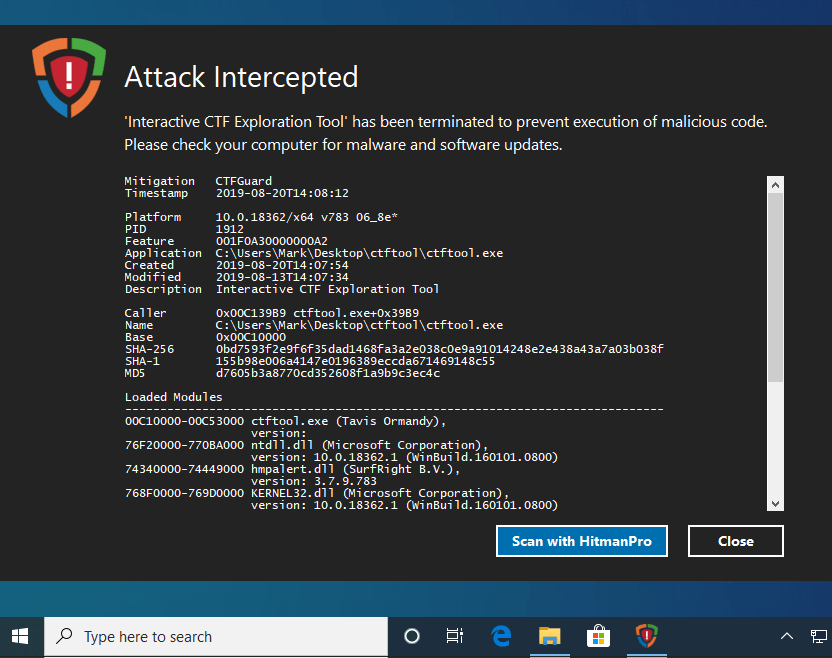
Dubbed CTF Guard, this new component intercepts and blocks applications that attempt to exploit CTF.
For example, Tavis Ormandy’s cfttool.exe, described as an “interactive CTF exploration tool” that lets researchers probe and try to find holes in CTF, will be intercepted and terminated when it attempts to connect and communicate with the CTF subsystem:
CFT Guard is already available in Sophos HitmanPro.Alert, and is coming soon to Sophos Intercept X.