Sophos ZTNA now supports on-premise Microsoft AD
Credit to Author: Chris McCormack| Date: Wed, 10 Jul 2024 15:16:31 +0000
 We are pleased to announce the availability of Sophos ZTNA 2.1, which brings support for on-premise Microsoft Active Directory for identity, zero downtime, seamless failover between cloud points-of-presence, and important security enhancements.
We are pleased to announce the availability of Sophos ZTNA 2.1, which brings support for on-premise Microsoft Active Directory for identity, zero downtime, seamless failover between cloud points-of-presence, and important security enhancements.
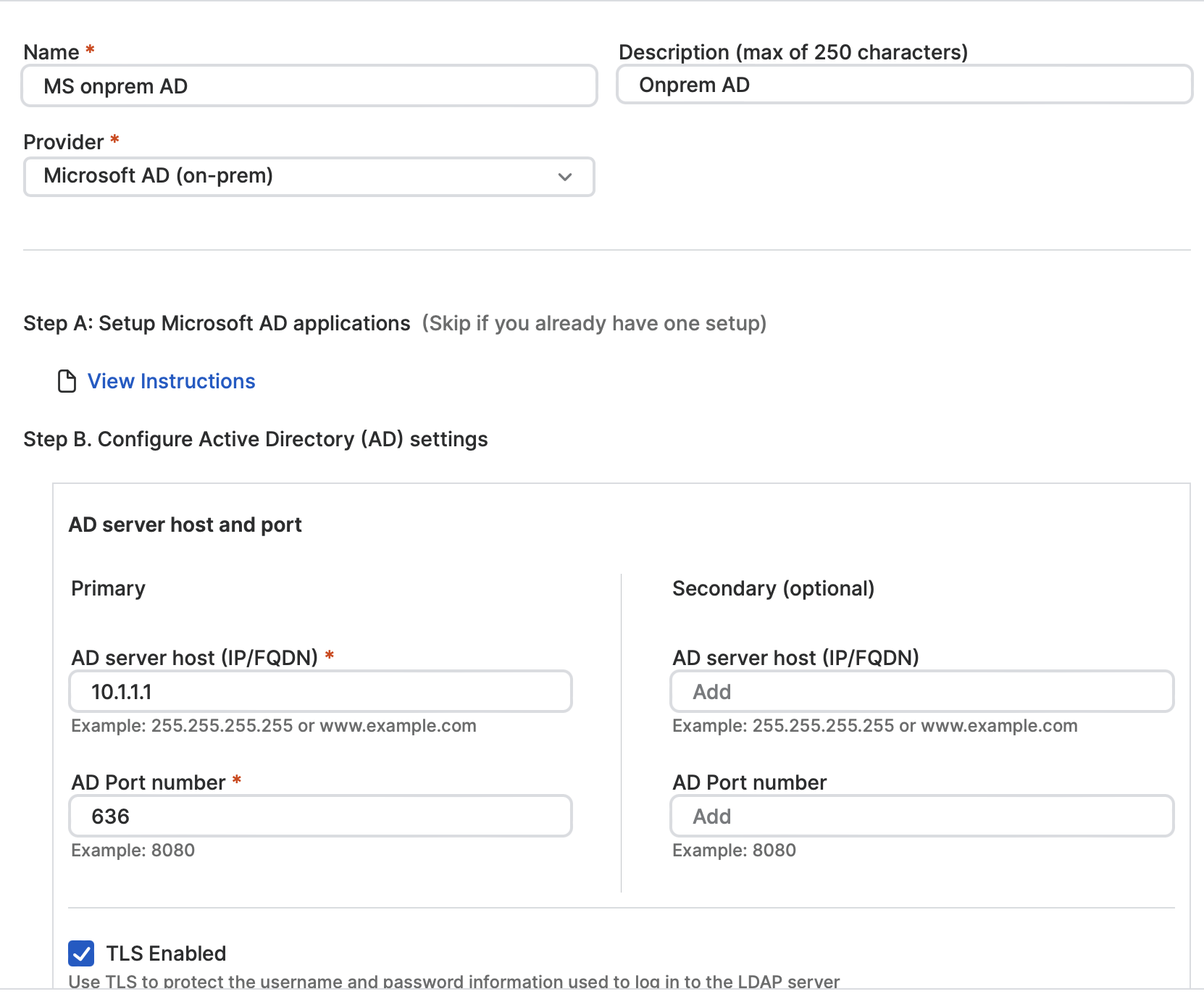
This release offers a new identity provider solution in addition to the existing cloud-based Microsoft Entra ID and Okta solutions already supported by Sophos ZTNA. It enables organizations without cloud infrastructure or a cloud-based identity platform to easily adopt Sophos ZTNA by leveraging their in-house Microsoft AD system for authentication with support for MFA through captchas or email OTPs.
In addition, cloud gateways running on virtual platforms (ESXi or Hyper-V) now support zero downtime and seamless failover between cloud points of presence. This capability will also be available for Sophos Firewall-integrated ZTNA Gateways with the release of v20 MR2, which is scheduled for later this month. This new capability allows for seamless transitions to the next closest regional gateway in the event of an outage in your preferred gateway region, ensuring uninterrupted ZTNA access during the outage.
An additional update with security enhancements is also available as ZTNA 2.1.1. You will need to first update your gateways to 2.1 and then apply the 2.1.1 update after that.
How to get the updates
The gateway image updates are available from Sophos Central. There is no need to update your ZTNA agents.
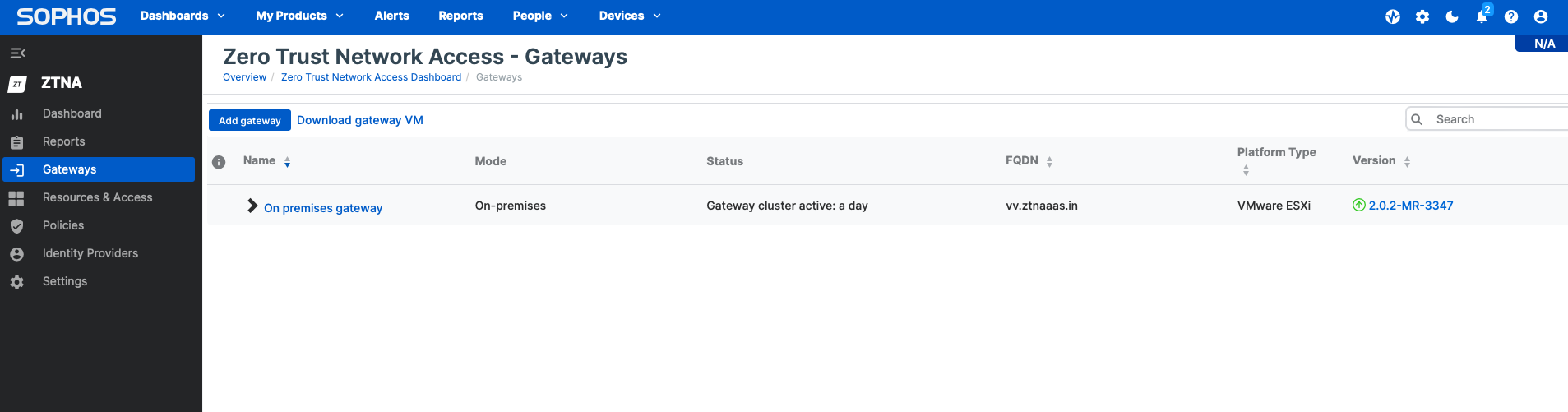
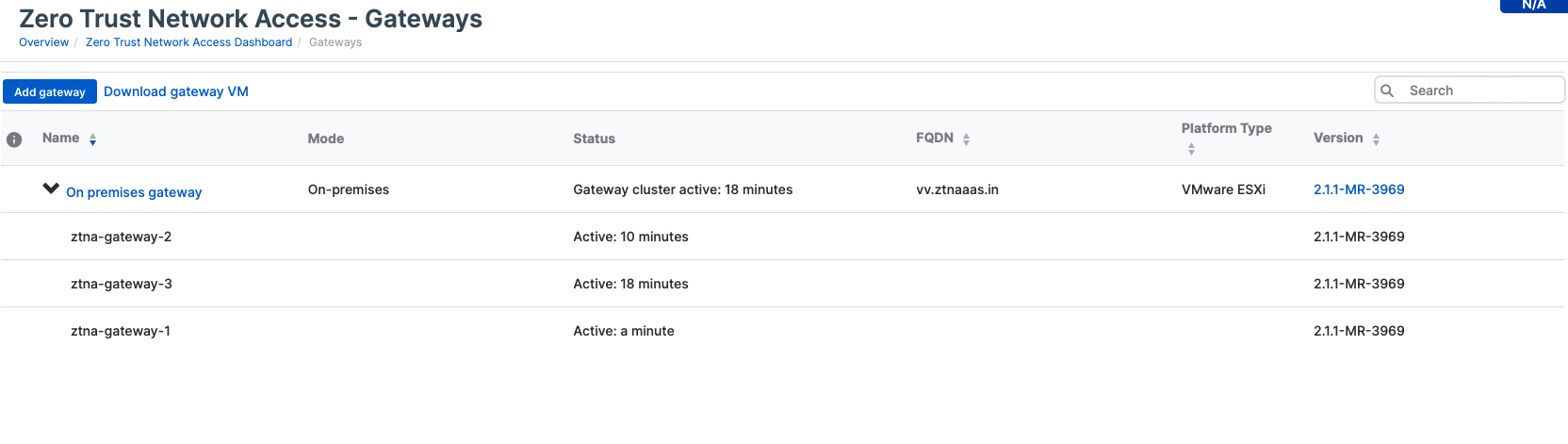
1. In Sophos Central, navigate to the Gateways page and notice an indication that an image update is available. This notification is only seen on gateways hosted on ESXi and Hyper-V platforms. For gateways hosted on Sophos Firewall, they will be updated when applying firmware update v20 MR2 (available later this month).
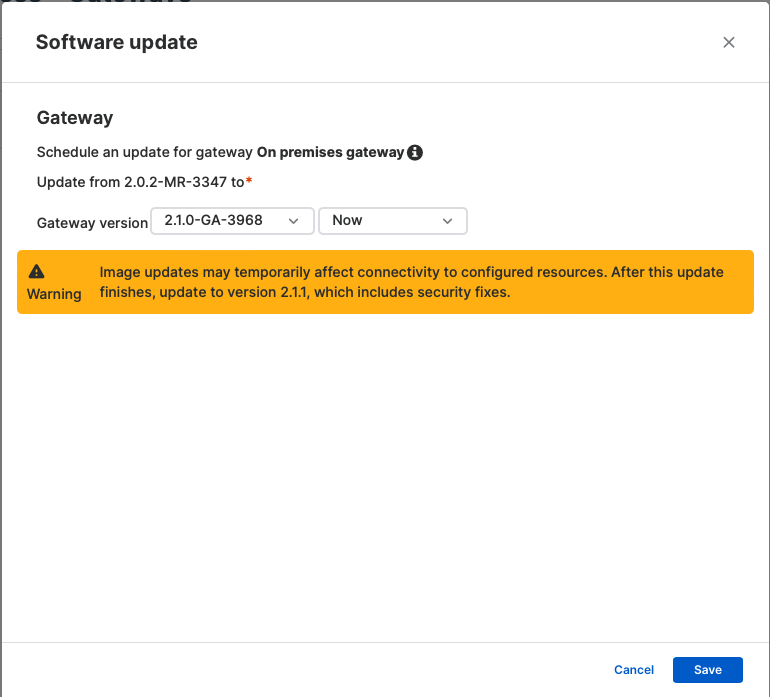
2. You can either initiate the upgrade immediately or schedule the upgrade for later. The update may take up to 30 minutes.
3. After the upgrade is completed and the gateway is back to “Active,” verify on the gateway’s diagnostics console that all the tests pass before initiating the next update to ZTNA 2.1.1.
Version 2.1.1 includes important security and vulnerability fixes, and we highly recommend that customers begin the upgrade process immediately. Upgrading to version 2.1.1 should also take approximately 30 minutes for a single node. The time required will be proportional if the deployment involves a multi-node cluster.
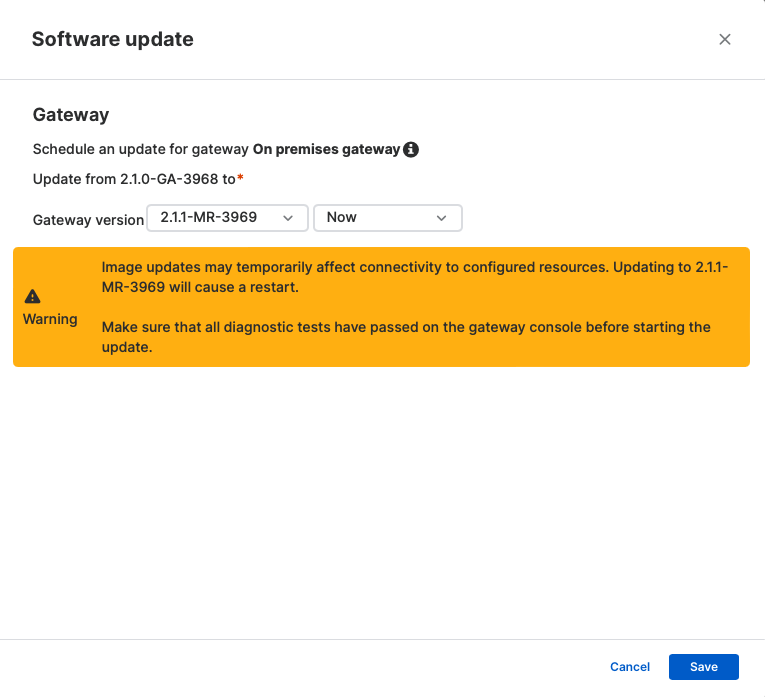
4. Check the gateway console diagnostics once the update is complete and the gateway returns to the “Active” state. If all diagnostics checks pass, resource access can be resumed.
Documentation
The latest online documentation is here.
The troubleshooting guide has also been updated in case you encounter any issues during configuration.