August Patch Tuesday goes big
Credit to Author: Angela Gunn| Date: Thu, 15 Aug 2024 08:10:07 +0000
Microsoft’s August 2024 Patch Tuesday release was, in one sense, a respite from July’s 138-CVE torrent of fixes, with just 85 CVEs addressed in the main release. However, with over two dozen advisories, a number of “informational” notices concerning material released in June and July, two high-profile issues for which the fixes are still a work in progress, and over 85 Linux-related CVEs covered in the release, administrators may find their patch prioritization especially complex this month.
At patch time, five of the issues addressed are known to be under exploit in the wild. Three more are publicly disclosed. Microsoft assesses that 11 CVEs, all in Windows, are by the company’s estimation more likely to be exploited in the next 30 days. Nine of this month’s issues are amenable to detection by Sophos protections, and we include information on those in a table below.
In addition to these patches, the release includes advisory information on 12 patches from Adobe, nine for Edge via Chrome (in addition to three Edge patches from Microsoft), and the regularly released servicing stack update (ADV990001). The company also provided information on five CVEs addressed earlier this summer but not announced in their respective months (one in June, four in July). We will list those in Appendix D below; those who have already applied the patches for those months are already protected and need not apply them again. (It should be noted that one issue patched in June, CVE-2024-38213, is under active attack in the wild – a good argument for applying patches as soon as possible after release.) Microsoft also took pains this month to flag three other CVEs for which fixes have already gone out, but that are included in Patch Tuesday information for transparency’s sake; we list those in Appendix D as well. We are as always including at the end of this post additional appendices listing all Microsoft’s patches, sorted by severity, by predicted exploitability, and by product family.
Finally, this month’s release includes a large cohort of CVEs related to CBL-Mariner, or in some cases to both Mariner and Azure Linux. (Mariner was renamed Azure Linux earlier this year, but the information provided by Microsoft on these CVEs differentiates between the two.) The CVEs come from a timespan from 2007 to 2024; the CVSS base scores range from 3.2 to a “perfect” 10. Those CVEs are not included in the data in the main part of this post, but we have listed all 84 CVEs in Appendix E at the end of this article for reference. Two additional Mariner / Azure Linux CVEs also touch Windows, and those two are included in the statistics in the main article as well as in Appendix E’s list.
The data in the main part of this post reflects only the 85 CVEs in the non-Mariner, non-advisory portion of the release.
By the numbers
- Total CVEs: 85
- Total Edge / Chrome advisory issues covered in update: 9 (plus 3 non-advisory Edge issues)
- Total non-Edge Microsoft advisory issues covered in update: 9
- Total Adobe issues covered in update: 12
- Publicly disclosed: 3
- Exploited: 5
- Severity
- Critical: 6
- Important: 77
- Moderate: 2
- Impact
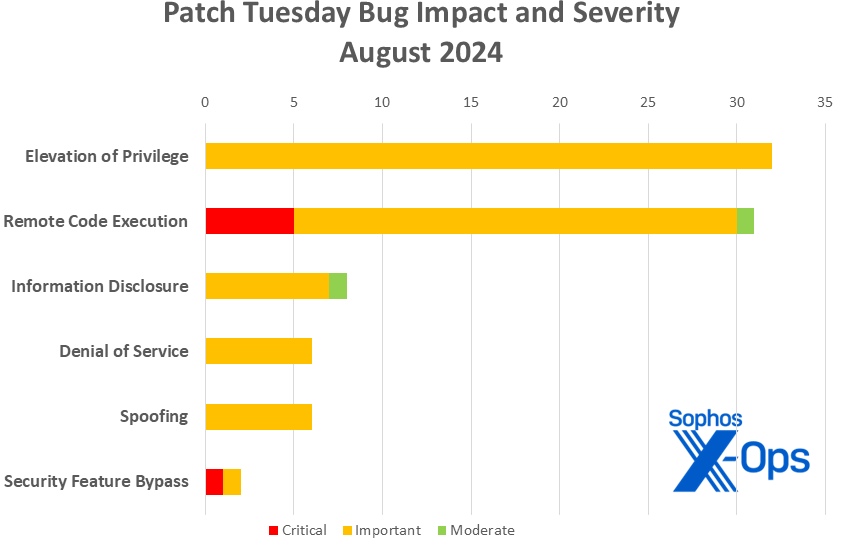
- Elevation of Privilege: 32
- Remote Code Execution: 31
- Information Disclosure: 8
- Denial of Service: 6
- Spoofing: 6
- Security Feature Bypass: 2
Figure 1: The six critical-severity vulnerabilities addressed in August’s Patch Tuesday release include the second this year involving security feature bypass. (This chart does not represent the Mariner-related issues discussed elsewhere in this article)
Products
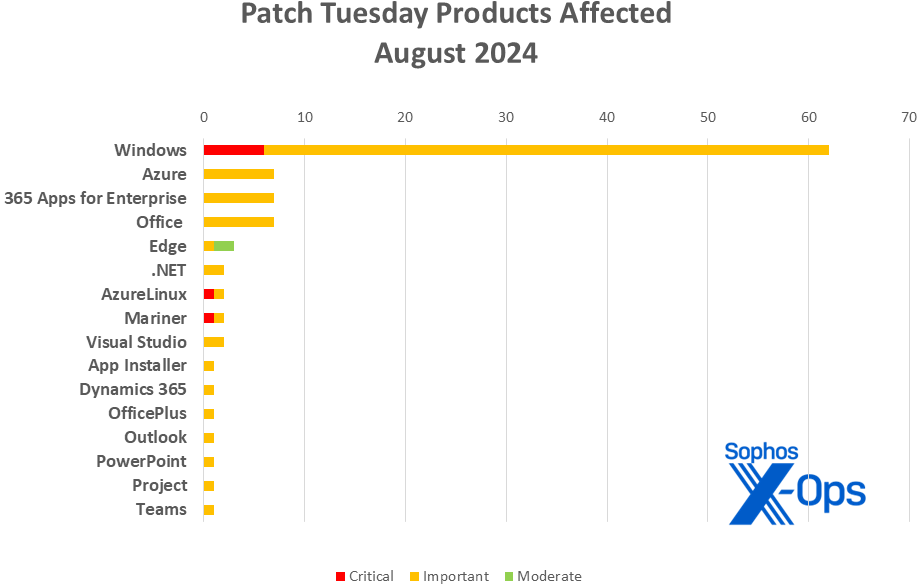
- Windows: 62
- Azure: 7
- 365 Apps for Enterprise: 7
- Office: 7
- Edge: 3 (plus 9 advisories via Chrome)
- .NET: 2
- Azure Linux: 2
- CBL-Mariner: 2
- Visual Studio: 2
- App Installer: 1
- Dynamics 365: 1
- OfficePlus: 1
- Outlook: 1
- PowerPoint: 1
- Project: 1
- Teams: 1
As is our custom for this list, CVEs that apply to more than one product family are counted once for each family they affect.
Figure 2: A wide variety of product families are affected by August’s patches; at least one, App Installer, is so obscure that Microsoft has included a link to information on it in the release itself, including information on updating it via winget. Still, Windows as ever rules the roost
Notable August updates
In addition to the issues discussed above, a number of specific items merit attention.
CVE-2024-21302 – Windows Secure Kernel Mode Elevation of Privilege Vulnerability
CVE-2024-38202 – Windows Update Stack Elevation of Privilege Vulnerability
These two Important-severity issued were debuted by researcher Alon Leviev last week at Black Hat last week after a prolonged responsible-disclosure process. Microsoft has been working on the solution for six months, but it needs a little more time to untangle this complex issue with Virtualization-Based Security (VBS). For now, Microsoft is publishing mitigation information for both CVE-2024-21302 and CVE-2024-38202 on their site.
CVE-2024-38063 – Windows TCP/IP Remote Code Execution Vulnerability
There are three CVEs in this release with a 9.8 CVSS base score, but only this one has the distinction of also being, in Microsoft’s estimation, more likely to be exploited in the next thirty days. That’s unfortunate, because this critical-severity RCE bug requires neither privileges nor user interaction. An attacker could exploit this issue by repeatedly sending IPv6 packets, with specially crafted IPv6 packets mixed in, to a Windows machine with IPv6 enabled. (Machines that have IPv6 disabled would not be affected by this attack.) Sophos has released protections (Exp/2438063-A) for this issue, as noted in the table below.
CVE-2024-38213 – Windows Mark of the Web Security Feature Bypass Vulnerability
This issue is one of the five noted above that was actually patched months ago (in this case, June 2024). Those who have applied the patches released in June are protected; those who have not applied the patches should do so, as the issue is currently under active attack.
[42 CVEs] Windows 11 24H2 patches, already
Even though Windows 11 24H2 is not yet in general release, just under half of the issues addressed this month apply to that operating system. Users of the new Copilot+ PCs who do not ingest their patches automatically should be sure to update their devices; those who do should have taken all the relevant patches with the latest cumulative update, which elevates those devices to Build 26100.1457.
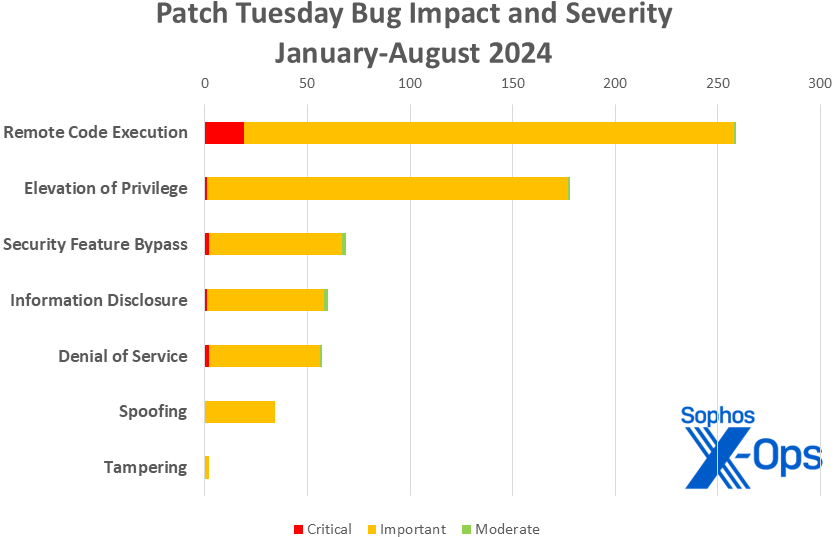
Figure 3: With a total of 659 CVEs addressed in Patch Tuesday releases so far in 2024, Microsoft’s dealing with a far heavier volume than they were at this point in 2023 (491 patches), but a bit less than they handled in 2022 (690 patches). That said, this table does not include the 84 Mariner-released CVEs discussed elsewhere in this post
Sophos protections
As you can every month, if you don’t want to wait for your system to pull down Microsoft’s updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your specific system’s architecture and build number.
Appendix A: Vulnerability Impact and Severity
This is a list of August patches sorted by impact, then sub-sorted by severity. Each list is further arranged by CVE.
Elevation of Privilege (32 CVEs)
| Important severity | |
| CVE-2024-21302 | Windows Secure Kernel Mode Elevation of Privilege Vulnerability |
| CVE-2024-29995 | Windows Kerberos Elevation of Privilege Vulnerability |
| CVE-2024-38084 | Microsoft OfficePlus Elevation of Privilege Vulnerability |
| CVE-2024-38098 | Azure Connected Machine Agent Elevation of Privilege Vulnerability |
| CVE-2024-38106 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-38107 | Windows Power Dependency Coordinator Elevation of Privilege Vulnerability |
| CVE-2024-38117 | Windows Named Pipe Filesystem Elevation of Privilege Vulnerability |
| CVE-2024-38125 | Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability |
| CVE-2024-38127 | Windows Hyper-V Elevation of Privilege Vulnerability |
| CVE-2024-38133 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-38134 | Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability |
| CVE-2024-38135 | Windows Resilient File System (ReFS) Elevation of Privilege Vulnerability |
| CVE-2024-38136 | Windows Resource Manager PSM Service Extension Elevation of Privilege Vulnerability |
| CVE-2024-38137 | Windows Resource Manager PSM Service Extension Elevation of Privilege Vulnerability |
| CVE-2024-38141 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2024-38142 | Windows Secure Kernel Mode Elevation of Privilege Vulnerability |
| CVE-2024-38143 | Windows WLAN AutoConfig Service Elevation of Privilege Vulnerability |
| CVE-2024-38144 | Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability |
| CVE-2024-38147 | Microsoft DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-38150 | Windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-38153 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-38162 | Azure Connected Machine Agent Elevation of Privilege Vulnerability |
| CVE-2024-38163 | Windows Update Stack Elevation of Privilege Vulnerability |
| CVE-2024-38184 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-38191 | Kernel Streaming Service Driver Elevation of Privilege Vulnerability |
| CVE-2024-38193 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2024-38196 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-38198 | Windows Print Spooler Elevation of Privilege Vulnerability |
| CVE-2024-38201 | Azure Stack Hub Elevation of Privilege Vulnerability |
| CVE-2024-38202 | Windows Update Stack Elevation of Privilege Vulnerability |
| CVE-2024-38215 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2024-38223 | Windows Initial Machine Configuration Elevation of Privilege Vulnerability |
Remote Code Execution (31 CVEs)
| Critical severity | |
| CVE-2022-3775 | Redhat: CVE-2022-3775 grub2 – Heap based out-of-bounds write when rendering certain Unicode sequences |
| CVE-2024-38063 | Windows TCP/IP Remote Code Execution Vulnerability |
| CVE-2024-38140 | Windows Reliable Multicast Transport Driver (RMCAST) Remote Code Execution Vulnerability |
| CVE-2024-38159 | Windows Network Virtualization Remote Code Execution Vulnerability |
| CVE-2024-38160 | Windows Network Virtualization Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2024-38114 | Windows IP Routing Management Snapin Remote Code Execution Vulnerability |
| CVE-2024-38115 | Windows IP Routing Management Snapin Remote Code Execution Vulnerability |
| CVE-2024-38116 | Windows IP Routing Management Snapin Remote Code Execution Vulnerability |
| CVE-2024-38120 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-38121 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-38128 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-38130 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-38131 | Clipboard Virtual Channel Extension Remote Code Execution Vulnerability |
| CVE-2024-38138 | Windows Deployment Services Remote Code Execution Vulnerability |
| CVE-2024-38152 | Windows OLE Remote Code Execution Vulnerability |
| CVE-2024-38154 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-38157 | Azure IoT SDK Remote Code Execution Vulnerability |
| CVE-2024-38158 | Azure IoT SDK Remote Code Execution Vulnerability |
| CVE-2024-38161 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-38169 | Microsoft Office Visio Remote Code Execution Vulnerability |
| CVE-2024-38170 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-38171 | Microsoft PowerPoint Remote Code Execution Vulnerability |
| CVE-2024-38172 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-38173 | Microsoft Outlook Remote Code Execution Vulnerability |
| CVE-2024-38178 | Scripting Engine Memory Corruption Vulnerability |
| CVE-2024-38180 | SmartScreen Prompt Remote Code Execution Vulnerability |
| CVE-2024-38189 | Microsoft Project Remote Code Execution Vulnerability |
| CVE-2024-38195 | Azure CycleCloud Remote Code Execution Vulnerability |
| CVE-2024-38199 | Windows Line Printer Daemon (LPD) Service Remote Code Execution Vulnerability |
| CVE-2024-38218 | Microsoft Edge (HTML-based) Memory Corruption Vulnerability |
| Moderate severity | |
| CVE-2024-38219 | Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability |
Information Disclosure (8 CVEs)
| Important severity | |
| CVE-2024-38118 | Microsoft Local Security Authority (LSA) Server Information Disclosure Vulnerability |
| CVE-2024-38122 | Microsoft Local Security Authority (LSA) Server Information Disclosure Vulnerability |
| CVE-2024-38123 | Windows Bluetooth Driver Information Disclosure Vulnerability |
| CVE-2024-38151 | Windows Kernel Information Disclosure Vulnerability |
| CVE-2024-38155 | Security Center Broker Information Disclosure Vulnerability |
| CVE-2024-38167 | .NET and Visual Studio Information Disclosure Vulnerability |
| CVE-2024-38214 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability |
| Moderate severity | |
| CVE-2024-38222 | Microsoft Edge (Chromium-based) Information Disclosure Vulnerability |
Denial of Service (6 CVEs)
| Important severity | |
| CVE-2024-38126 | Windows Network Address Translation (NAT) Denial of Service Vulnerability |
| CVE-2024-38132 | Windows Network Address Translation (NAT) Denial of Service Vulnerability |
| CVE-2024-38145 | Windows Layer-2 Bridge Network Driver Denial of Service Vulnerability |
| CVE-2024-38146 | Windows Layer-2 Bridge Network Driver Denial of Service Vulnerability |
| CVE-2024-38148 | Windows Secure Channel Denial of Service Vulnerability |
| CVE-2024-38168 | .NET and Visual Studio Denial of Service Vulnerability |
Spoofing (6 CVEs)
| Important severity | |
| CVE-2024-37968 | Windows DNS Spoofing Vulnerability |
| CVE-2024-38108 | Azure Stack Spoofing Vulnerability |
| CVE-2024-38177 | Windows App Installer Spoofing Vulnerability |
| CVE-2024-38197 | Microsoft Teams for iOS Spoofing Vulnerability |
| CVE-2024-38200 | Microsoft Office Spoofing Vulnerability |
| CVE-2024-38211 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability |
Security Feature Bypass (2 CVEs)
| Critical severity | |
| CVE-2023-40547 | Redhat: CVE-2023-40547 Shim – RCE in HTTP boot support may lead to secure boot bypass |
| Important severity | |
| CVE-2022-2601 | Redhat: CVE-2022-2601 grub2 – Buffer overflow in grub_font_construct_glyph() can lead to out-of-bound write and possible secure boot bypass |
Appendix B: Exploitability
This is a list of the August CVEs judged by Microsoft to be either under exploitation in the wild or more likely to be exploited in the wild within the first 30 days post-release. The list is arranged by CVE. This table does not include CVE-2024-38213, which was released in June.
| Exploitation detected | |
| CVE-2024-38106 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-38107 | Windows Power Dependency Coordinator Elevation of Privilege Vulnerability |
| CVE-2024-38178 | Scripting Engine Memory Corruption Vulnerability |
| CVE-2024-38189 | Microsoft Project Remote Code Execution Vulnerability |
| CVE-2024-38193 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
| Exploitation more likely within the next 30 days | |
| CVE-2024-38063 | Windows TCP/IP Remote Code Execution Vulnerability |
| CVE-2024-38125 | Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability |
| CVE-2024-38133 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-38141 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2024-38144 | Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability |
| CVE-2024-38147 | Microsoft DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-38148 | Windows Secure Channel Denial of Service Vulnerability |
| CVE-2024-38150 | Windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-38163 | Windows Update Stack Elevation of Privilege Vulnerability |
| CVE-2024-38196 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-38198 | Windows Print Spooler Elevation of Privilege Vulnerability |
Appendix C: Products Affected
This is a list of August’s patches sorted by product family, then sub-sorted by severity. Each list is further arranged by CVE. Patches that are shared among multiple product families are listed multiple times, once for each product family.
Windows (62 CVEs)
| Critical severity | |
| CVE-2022-3775 | Redhat: CVE-2022-3775 grub2 – Heap based out-of-bounds write when rendering certain Unicode sequences |
| CVE-2023-40547 | Redhat: CVE-2023-40547 Shim – RCE in HTTP boot support may lead to secure boot bypass |
| CVE-2024-38063 | Windows TCP/IP Remote Code Execution Vulnerability |
| CVE-2024-38140 | Windows Reliable Multicast Transport Driver (RMCAST) Remote Code Execution Vulnerability |
| CVE-2024-38159 | Windows Network Virtualization Remote Code Execution Vulnerability |
| CVE-2024-38160 | Windows Network Virtualization Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2022-2601 | Redhat: CVE-2022-2601 grub2 – Buffer overflow in grub_font_construct_glyph() can lead to out-of-bound write and possible secure boot bypass |
| CVE-2024-21302 | Windows Secure Kernel Mode Elevation of Privilege Vulnerability |
| CVE-2024-29995 | Windows Kerberos Elevation of Privilege Vulnerability |
| CVE-2024-37968 | Windows DNS Spoofing Vulnerability |
| CVE-2024-38106 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-38107 | Windows Power Dependency Coordinator Elevation of Privilege Vulnerability |
| CVE-2024-38114 | Windows IP Routing Management Snapin Remote Code Execution Vulnerability |
| CVE-2024-38115 | Windows IP Routing Management Snapin Remote Code Execution Vulnerability |
| CVE-2024-38116 | Windows IP Routing Management Snapin Remote Code Execution Vulnerability |
| CVE-2024-38117 | Windows Named Pipe Filesystem Elevation of Privilege Vulnerability |
| CVE-2024-38118 | Microsoft Local Security Authority (LSA) Server Information Disclosure Vulnerability |
| CVE-2024-38120 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-38121 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-38122 | Microsoft Local Security Authority (LSA) Server Information Disclosure Vulnerability |
| CVE-2024-38123 | Windows Bluetooth Driver Information Disclosure Vulnerability |
| CVE-2024-38125 | Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability |
| CVE-2024-38126 | Windows Network Address Translation (NAT) Denial of Service Vulnerability |
| CVE-2024-38127 | Windows Hyper-V Elevation of Privilege Vulnerability |
| CVE-2024-38128 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-38130 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-38131 | Clipboard Virtual Channel Extension Remote Code Execution Vulnerability |
| CVE-2024-38132 | Windows Network Address Translation (NAT) Denial of Service Vulnerability |
| CVE-2024-38133 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-38134 | Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability |
| CVE-2024-38135 | Windows Resilient File System (ReFS) Elevation of Privilege Vulnerability |
| CVE-2024-38136 | Windows Resource Manager PSM Service Extension Elevation of Privilege Vulnerability |
| CVE-2024-38137 | Windows Resource Manager PSM Service Extension Elevation of Privilege Vulnerability |
| CVE-2024-38138 | Windows Deployment Services Remote Code Execution Vulnerability |
| CVE-2024-38141 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2024-38142 | Windows Secure Kernel Mode Elevation of Privilege Vulnerability |
| CVE-2024-38143 | Windows WLAN AutoConfig Service Elevation of Privilege Vulnerability |
| CVE-2024-38144 | Kernel Streaming WOW Thunk Service Driver Elevation of Privilege Vulnerability |
| CVE-2024-38145 | Windows Layer-2 Bridge Network Driver Denial of Service Vulnerability |
| CVE-2024-38146 | Windows Layer-2 Bridge Network Driver Denial of Service Vulnerability |
| CVE-2024-38147 | Microsoft DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-38148 | Windows Secure Channel Denial of Service Vulnerability |
| CVE-2024-38150 | Windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-38151 | Windows Kernel Information Disclosure Vulnerability |
| CVE-2024-38152 | Windows OLE Remote Code Execution Vulnerability |
| CVE-2024-38153 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-38154 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-38155 | Security Center Broker Information Disclosure Vulnerability |
| CVE-2024-38161 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-38163 | Windows Update Stack Elevation of Privilege Vulnerability |
| CVE-2024-38178 | Scripting Engine Memory Corruption Vulnerability |
| CVE-2024-38180 | SmartScreen Prompt Remote Code Execution Vulnerability |
| CVE-2024-38184 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-38191 | Kernel Streaming Service Driver Elevation of Privilege Vulnerability |
| CVE-2024-38193 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability |
| CVE-2024-38196 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-38198 | Windows Print Spooler Elevation of Privilege Vulnerability |
| CVE-2024-38199 | Windows Line Printer Daemon (LPD) Service Remote Code Execution Vulnerability |
| CVE-2024-38202 | Windows Update Stack Elevation of Privilege Vulnerability |
| CVE-2024-38214 | Windows Routing and Remote Access Service (RRAS) Information Disclosure Vulnerability |
| CVE-2024-38215 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2024-38223 | Windows Initial Machine Configuration Elevation of Privilege Vulnerability |
Azure (7 CVEs)
| Important severity | |
| CVE-2024-38098 | Azure Connected Machine Agent Elevation of Privilege Vulnerability |
| CVE-2024-38108 | Azure Stack Spoofing Vulnerability |
| CVE-2024-38157 | Azure IoT SDK Remote Code Execution Vulnerability |
| CVE-2024-38158 | Azure IoT SDK Remote Code Execution Vulnerability |
| CVE-2024-38162 | Azure Connected Machine Agent Elevation of Privilege Vulnerability |
| CVE-2024-38195 | Azure CycleCloud Remote Code Execution Vulnerability |
| CVE-2024-38201 | Azure Stack Hub Elevation of Privilege Vulnerability |
365 Apps for Enterprise (7 CVEs)
| Important severity | |
| CVE-2024-38169 | Microsoft Office Visio Remote Code Execution Vulnerability |
| CVE-2024-38170 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-38171 | Microsoft PowerPoint Remote Code Execution Vulnerability |
| CVE-2024-38172 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-38173 | Microsoft Outlook Remote Code Execution Vulnerability |
| CVE-2024-38189 | Microsoft Project Remote Code Execution Vulnerability |
| CVE-2024-38200 | Microsoft Office Spoofing Vulnerability |
Office (7 CVEs)
| Important severity | |
| CVE-2024-38169 | Microsoft Office Visio Remote Code Execution Vulnerability |
| CVE-2024-38170 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-38171 | Microsoft PowerPoint Remote Code Execution Vulnerability |
| CVE-2024-38172 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-38173 | Microsoft Outlook Remote Code Execution Vulnerability |
| CVE-2024-38189 | Microsoft Project Remote Code Execution Vulnerability |
| CVE-2024-38200 | Microsoft Office Spoofing Vulnerability |
Edge (3 CVE)
| Important severity | |
| CVE-2024-38218 | Microsoft Edge (HTML-based) Memory Corruption Vulnerability |
| Moderate severity | |
| CVE-2024-38219 | Microsoft Edge (Chromium-based) Remote Code Execution Vulnerability |
| CVE-2024-38222 | Microsoft Edge (Chromium-based) Information Disclosure Vulnerability |
.NET (2 CVE)
| Important severity | |
| CVE-2024-38167 | .NET and Visual Studio Information Disclosure Vulnerability |
| CVE-2024-38168 | .NET and Visual Studio Denial of Service Vulnerability |
Azure Linux (2 CVE)
| Critical severity | |
| CVE-2022-3775 | Redhat: CVE-2022-3775 grub2 – Heap based out-of-bounds write when rendering certain Unicode sequences |
| Important severity | |
| CVE-2022-2601 | Redhat: CVE-2022-2601 grub2 – Buffer overflow in grub_font_construct_glyph() can lead to out-of-bound write and possible secure boot bypass |
CBL-Mariner (2 CVE)
| Critical severity | |
| CVE-2022-3775 | Redhat: CVE-2022-3775 grub2 – Heap based out-of-bounds write when rendering certain Unicode sequences |
| Important severity | |
| CVE-2022-2601 | Redhat: CVE-2022-2601 grub2 – Buffer overflow in grub_font_construct_glyph() can lead to out-of-bound write and possible secure boot bypass |
Visual Studio (2 CVE)
| Important severity | |
| CVE-2024-38167 | .NET and Visual Studio Information Disclosure Vulnerability |
| CVE-2024-38168 | .NET and Visual Studio Denial of Service Vulnerability |
App Installer (1 CVE)
| Important severity | |
| CVE-2024-38177 | Windows App Installer Spoofing Vulnerability |
Dynamics 365 (1 CVE)
| Important severity | |
| CVE-2024-38211 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability |
OfficePlus (1 CVE)
| Important severity | |
| CVE-2024-38084 | Microsoft OfficePlus Elevation of Privilege Vulnerability |
Outlook (1 CVE)
| Important severity | |
| CVE-2024-38173 | Microsoft Outlook Remote Code Execution Vulnerability |
PowerPoint (1 CVE)
| Important severity | |
| CVE-2024-38171 | Microsoft PowerPoint Remote Code Execution Vulnerability |
Project (1 CVE)
| Important severity | |
| CVE-2024-38189 | Microsoft Project Remote Code Execution Vulnerability |
Teams (1 CVE)
| Important severity | |
| CVE-2024-38197 | Microsoft Teams for iOS Spoofing Vulnerability |
Appendix D: Advisories and Other Products
This is a list of advisories and information on other relevant CVEs in the August Microsoft release, sorted by product.
Relevant to Edge / Chromium (9 CVEs)
| CVE-2024-6990 | Chromium: CVE-2024-6990 Uninitialized Use in Dawn |
| CVE-2024-7255 | Chromium: CVE-2024-7255 Out of bounds read in WebTransport |
| CVE-2024-7256 | Chromium: CVE-2024-7256 Insufficient data validation in Dawn |
| CVE-2024-7532 | Chromium: CVE-2024-7532 Out of bounds memory access in ANGLE |
| CVE-2024-7533 | Chromium: CVE-2024-7533 Use after free in Sharing |
| CVE-2024-7534 | Chromium: CVE-2024-7534 Heap buffer overflow in Layout |
| CVE-2024-7535 | Chromium: CVE-2024-7535 Inappropriate implementation in V8 |
| CVE-2024-7536 | Chromium: CVE-2024-7536 Use after free in WebAudio |
| CVE-2024-7550 | Chromium: CVE-2024-7550 Type Confusion in V8 |
Servicing Stack Updates (1 item)
| ADV990001 | Latest Servicing Stack Updates |
Previously Released; Information Missing from Previous Patch Tuesday Data (5 CVEs)
| Released June 2024 | |
| CVE-2024-38213 | Windows Mark of the Web Security Feature Bypass Vulnerability |
| Released July 2024 | |
| CVE-2024-38165 | Windows Compressed Folder Tampering Vulnerability |
| CVE-2024-38185 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-38186 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
| CVE-2024-38187 | Windows Kernel-Mode Driver Elevation of Privilege Vulnerability |
Previously Released (Cloud); Information Provided as Advisory Only (3 items)
| CVE-2024-38109 | Azure Health Bot Elevation of Privilege Vulnerability |
| CVE-2024-38166 | Microsoft Dynamics 365 Cross-site Scripting Vulnerability |
| CVE-2024-38206 | Microsoft Copilot Studio Information Disclosure Vulnerability |
Relevant to Adobe (non-Microsoft release) (12 CVEs)
| APSB24-57 | CVE-2024-39383 | Use After Free (CWE-416) |
| APSB24-57 | CVE-2024-39422 | Use After Free (CWE-416) |
| APSB24-57 | CVE-2024-39423 | Out-of-bounds Write (CWE-787) |
| APSB24-57 | CVE-2024-39424 | Use After Free (CWE-416) |
| APSB24-57 | CVE-2024-39425 | Time-of-check Time-of-use (TOCTOU) Race Condition (CWE-367) |
| APSB24-57 | CVE-2024-39426 | Access of Memory Location After End of Buffer (CWE-788) |
| APSB24-57 | CVE-2024-41830 | Use After Free (CWE-416) |
| APSB24-57 | CVE-2024-41831 | Use After Free (CWE-416) |
| APSB24-57 | CVE-2024-41832 | Out-of-bounds Read (CWE-125) |
| APSB24-57 | CVE-2024-41833 | Out-of-bounds Read (CWE-125) |
| APSB24-57 | CVE-2024-41834 | Out-of-bounds Read (CWE-125) |
| APSB24-57 | CVE-2024-41835 | Out-of-bounds Read (CWE-125) |
Appendix E: CVEs Relevant to CBL-Mariner / Azure Linux
The information on these CVEs, which originated with an assortment of CNAs, is often rather different in nature from that provided for CVEs addressed in Microsoft’s Patch Tuesday process. Often such CVEs have no title, or no available CVSS scoring. For this table, we have chosen to simply list the CVEs as noted in Microsoft’s own summary information.
| CVE-2007-4559 | CVE-2022-36648 | CVE-2024-37370 | CVE-2024-40898 |
| CVE-2017-17522 | CVE-2022-3775 | CVE-2024-37371 | CVE-2024-40902 |
| CVE-2017-18207 | CVE-2022-3872 | CVE-2024-38428 | CVE-2024-41110 |
| CVE-2019-20907 | CVE-2022-4144 | CVE-2024-38571 | CVE-2024-42068 |
| CVE-2019-3816 | CVE-2022-41722 | CVE-2024-38583 | CVE-2024-42070 |
| CVE-2019-3833 | CVE-2022-48788 | CVE-2024-38662 | CVE-2024-42071 |
| CVE-2019-9674 | CVE-2022-48841 | CVE-2024-38780 | CVE-2024-42072 |
| CVE-2021-23336 | CVE-2023-29402 | CVE-2024-39277 | CVE-2024-42073 |
| CVE-2021-3750 | CVE-2023-29404 | CVE-2024-39292 | CVE-2024-42074 |
| CVE-2021-3929 | CVE-2023-3354 | CVE-2024-39331 | CVE-2024-42075 |
| CVE-2021-4158 | CVE-2023-45288 | CVE-2024-39473 | CVE-2024-42076 |
| CVE-2021-4206 | CVE-2023-52340 | CVE-2024-39474 | CVE-2024-42077 |
| CVE-2021-4207 | CVE-2024-0397 | CVE-2024-39475 | CVE-2024-42078 |
| CVE-2021-43565 | CVE-2024-0853 | CVE-2024-39476 | CVE-2024-42080 |
| CVE-2022-0358 | CVE-2024-2004 | CVE-2024-39480 | CVE-2024-42082 |
| CVE-2022-2601 | CVE-2024-23722 | CVE-2024-39482 | CVE-2024-42083 |
| CVE-2022-26353 | CVE-2024-2398 | CVE-2024-39483 | CVE-2024-42237 |
| CVE-2022-26354 | CVE-2024-2466 | CVE-2024-39484 | CVE-2024-6104 |
| CVE-2022-29526 | CVE-2024-26461 | CVE-2024-39485 | CVE-2024-6257 |
| CVE-2022-2962 | CVE-2024-26900 | CVE-2024-39489 | CVE-2024-6655 |
| CVE-2022-3165 | CVE-2024-36288 | CVE-2024-39493 | |
| CVE-2022-35414 | CVE-2024-37298 | CVE-2024-39495 |