Was T-Mobile compromised by a zero-day in Jira?
A moderator of the notorious data breach trading platform BreachForums is offering data for sale they claim comes from a data breach at T-Mobile.
The moderator, going by the name of IntelBroker, describes the data as containing source code, SQL files, images, Terraform data, t-mobile.com certifications, and “Siloprograms.” (We’ve not heard of siloprograms, and can’t find a reference to them anywhere, so perhaps it’s a mistranslation or typo.)
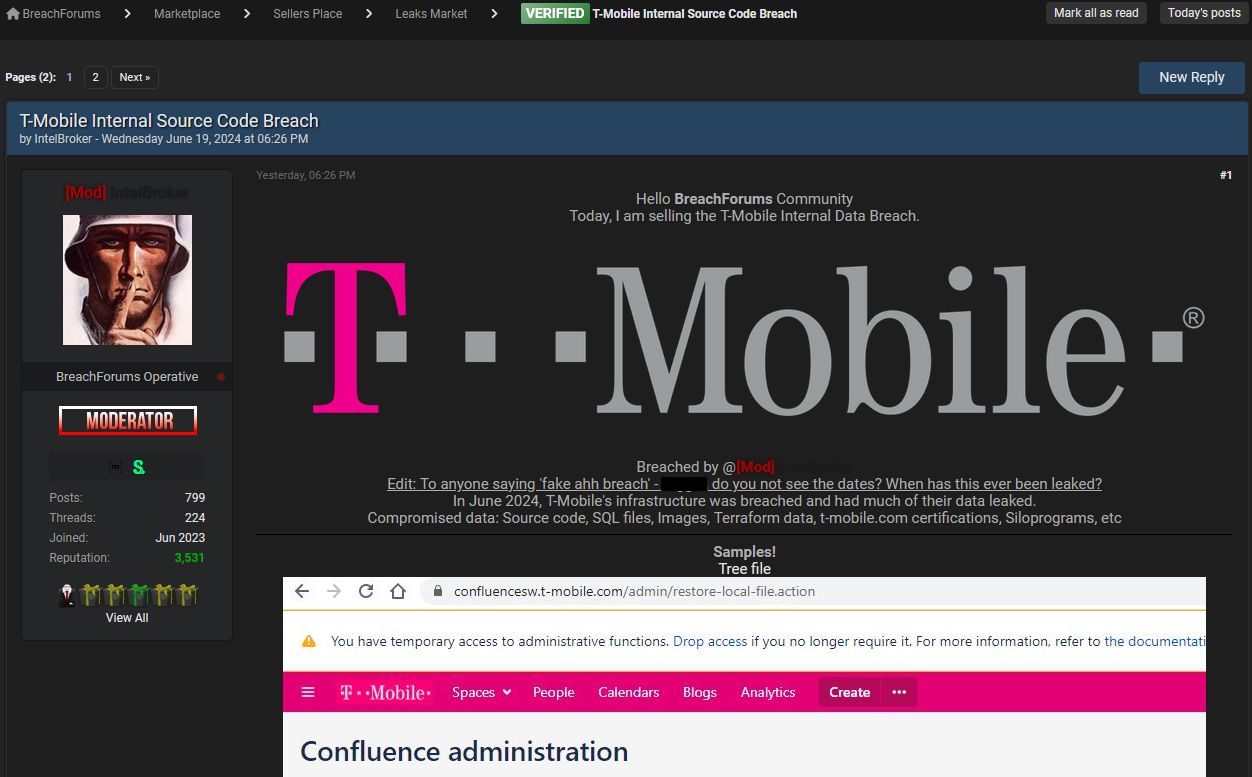
To prove they had the data, IntelBroker posted several screenshots showing access with administrative privileges to a Confluence server and T-Mobile’s internal Slack channels for developers.
But according to sources known to BleepingComputer, the data shared by IntelBroker actually consists of older screenshots. These screenshots show T-Mobile’s infrastructure, posted at a known—yet unnamed—third-party vendor’s servers, from where they were stolen.
When we looked at the screenshots IntelBroker attached to their post, we spotted something interesting in one of them.
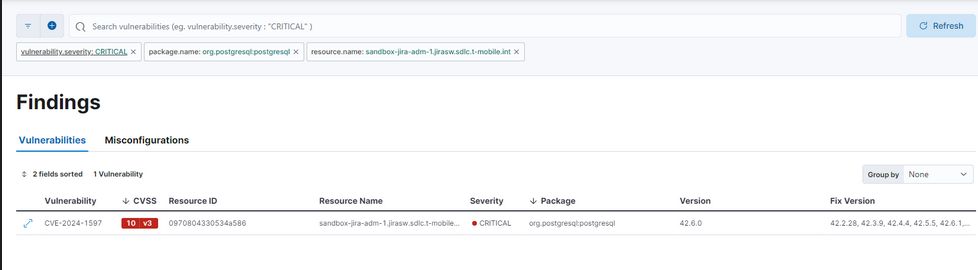
This screenshot shows a search query for a critical vulnerability in Jira, a project management tool used by teams to plan, track, release and support software. It’s typically a place where you could find the source code of works in progress.
The search returns the result CVE-2024-1597, a SQL injection vulnerability. SQL injection happens when a cybercriminal injects malicious SQL code into a form on a website, such as a login page, instead of the data the form is asking for. The vulnerability affects Confluence Data Center and Server according to Atlassian’s May security bulletin.
For a better understanding, it’s important to note that Jira and Confluence are both products created by Atlassian, where Jira is the project management and issue tracking tool and Confluence is the collaboration and documentation tool. They are often used together.
If IntelBroker has a working exploit for the SQL injection vulnerability, this could also explain their claim that they have the source code of three internal tools used at Apple, including a single sign-on authentication system known as AppleConnect.
This theory is supported by the fact that IntelBroker is also offering a Jira zero-day for sale.

“I’m selling a zero-day RCE for Atlassian’s Jira.
Works for the latest version of the desktop app, as well as Jira with confluence.
No login is required for this, and works with Okta SSO.”
If this is true then this exploit, or its fruits, might be used for data breaches that involve personal data.
Meanwhile, T-Mobile has denied it has suffered a breach, saying it is investigating whether there has been a breach at a third-party provider.
“We have no indication that T-Mobile customer data or source code was included and can confirm that the bad actor’s claim that T-Mobile’s infrastructure was accessed is false.”
We don’t just report on threats – we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your—and your family’s—personal information by using identity protection.