Bing ad for NordVPN leads to SecTopRAT
Most of the malicious search ads we have seen have originated from Google, but threat actors are also abusing other search engines. Microsoft Bing is probably the second best target due to its close ties to the Windows ecosystem and Edge browser.
In this blog post, we look at a very recent malvertising campaign impersonating the popular VPN software NordVPN. A malicious advertiser is capturing traffic from Bing searches and redirecting users to a decoy site that looks almost identical to the real one.
The threat actors went ever further by trying to digitally sign a malicious installer as if they were the official vendor. Victims will have the impression they are getting NordVPN as it is part of the package, but will also inadvertently install a Remote Access Trojan known as SecTopRAT on their computer.
We have reported the malicious Bing ad to Microsoft, and other parts of the distribution infrastructure to their respective provider. We want to reiterate that NordVPN is a legitimate VPN provider and they are being impersonated by threat actors.
Fraudulent Bing ad
When searching for “nord vpn” via the Bing search engine, we identified a malicious ad that impersonates NordVPN. The ad itself looks suspicious because of the URL in the ad snippet. The domain name nordivpn[.]xyz was created one day ago (April 3, 2024). It was probably chosen as it looks quite similar to the official name and can deceive users who aren’t looking too closely.
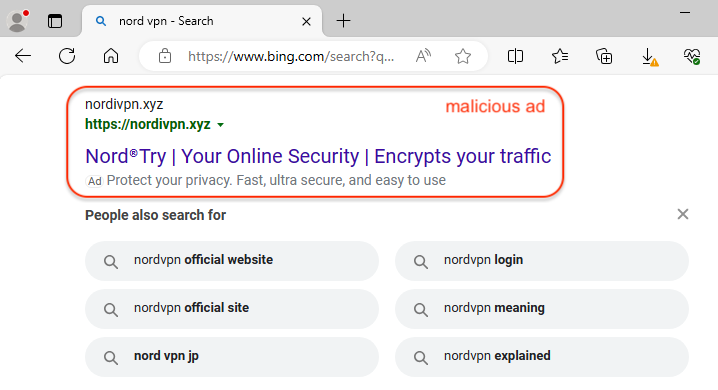
As we often see, the ad URL is simply used as a redirection mechanism to a fake website that is meant to look identical to the one being impersonated. This is true here as well, where we have a redirect to besthord-vpn[.]com (note again the spelling chosen with the ‘h‘ looking like an ‘n‘) which was created today, only a few hours ago.
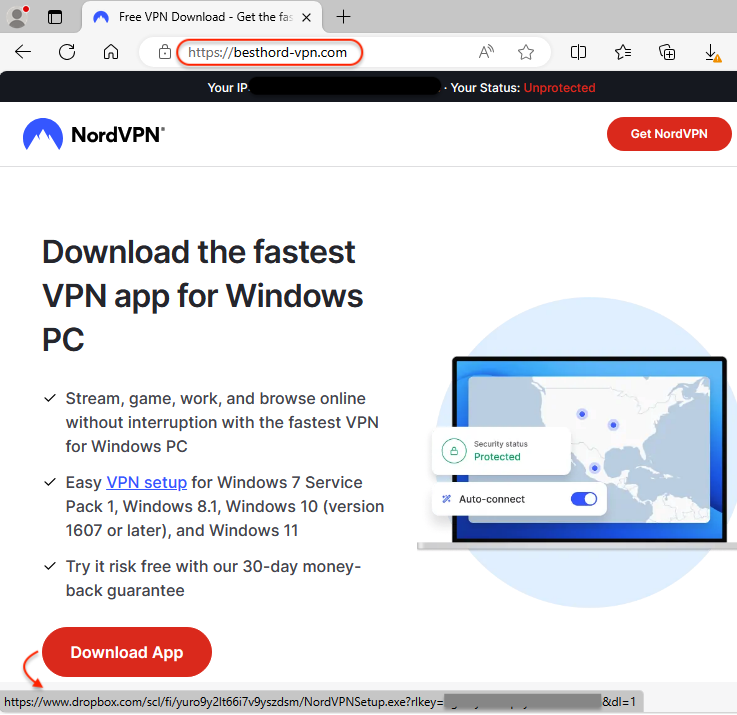
The website looks incredibly convincing, and victims will be tricked into downloading the app from there. Unlike the legitimate NordVPN that goes through a sign up process, here you can directly download the installer from Dropbox.
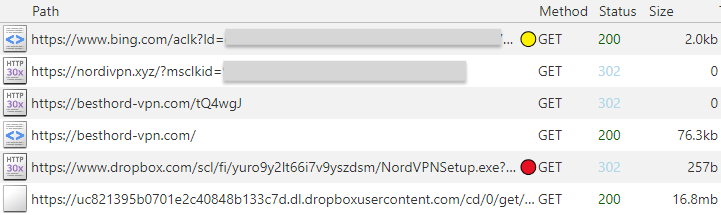
Here’s a summary of the traffic flow from the malicious ad to the download link:
Malware payload
The downloaded file is called NordVPNSetup.exe and is digitally signed, as if it was from its official vendor; however, the signature is not valid.
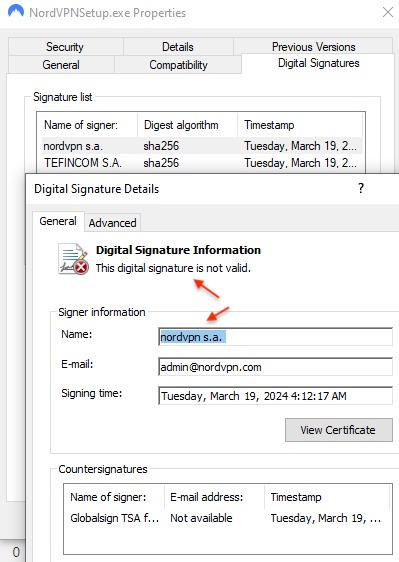
The file contains both an installer for NordVPN and a malware payload. The installer for NordVPN is meant to give victims the illusion that they are actually installing a real file.
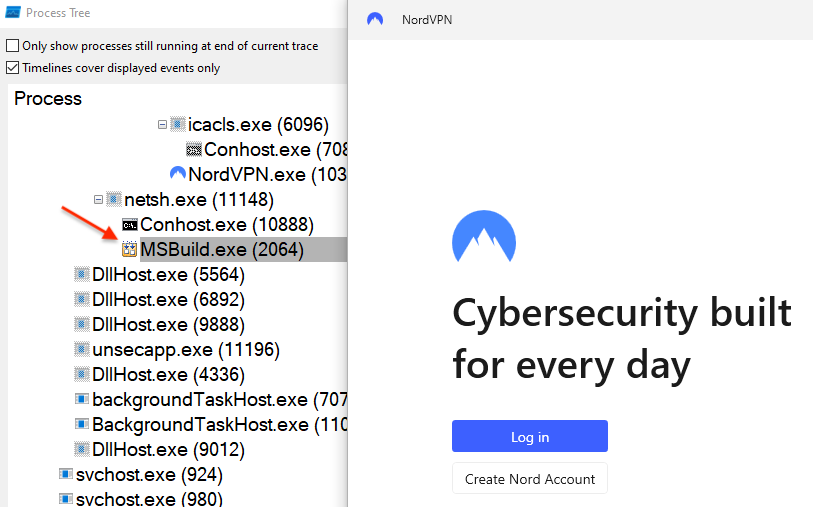
The payload is injected into MSBuild.exe and will connect to the malware author’s command and control server at 45.141.87[.]216 on port 15647.
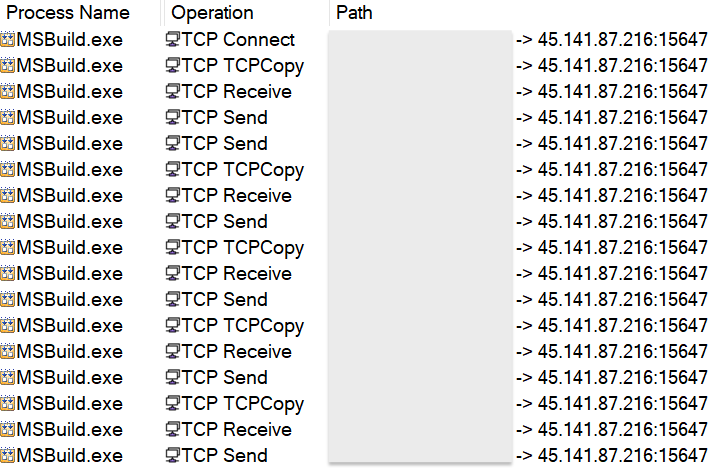
That network traffic is detected by Emerging Threats as Arechclient2 Backdoor, an alias for SecTopRAT.
Conclusion
Malvertising continues to show how easy it is to surreptitiously install malware under the guise of popular software downloads. Threat actors are able to roll out infrastructure quickly and easily to bypass many content filters.
ThreatDown customers who have DNS Filtering can proactively block online ads by enabling the rule for advertisements. This is a simple, and yet powerful way to prevent malvertising across an entire organization or in specific areas.
The malicious ad and related indictors have been reported as we work with industry partners to take down this campaign. Dropbox has already taken action to take down the malicious download.
Indicators of Compromise
Malicious domains
nordivpn[.]xyz
besthord-vpn[.]com
Fake NordVPN installer
e9131d9413f1596b47e86e88dc5b4e4cc70a0a4ec2d39aa8f5a1a5698055adfc
SecTopRAT C2
45.141.87[.]216