The Phantom Menace: Brute Ratel remains rare and targeted
Credit to Author: gallagherseanm| Date: Thu, 18 May 2023 11:00:58 +0000
Last year, we reported the growing use of the commercial offensive security tool Brute Ratel by criminal actors, including those behind Black Cat ransomware incidents. After public exposure of a version of the tool, many were concerned that Brute Ratel would become widely adopted as the successor to Cobalt Strike, the long-lived and long-abused offensive security tool that has been the go-to for malicious actors’ lateral movement needs.
Marketed as “the most advanced Red Team and Adversary Simulation Software,” Brute Ratel consists of a remote access agent (a “Badger”), a server, and “commander” user interface software. Similar to Cobalt Strike’s “beacons,” Badger instances can communicate with each other as well as with the C2, providing a covert communication channel from the initial point of compromise in a breach to other systems with Badger instances running on them within a targeted network. Badger-to-Badger communications can be over TCP and the SMB file-sharing protocol; communications back to the C2 server are over web protocols (HTTP and HTTPS), and DNS over HTTPS (DOH).
Despite the developer’s insistence that Brute Ratel could not be pirated or abused like Cobalt Strike, the tool suite was compromised in 2022. During the summer of 2022, the use of Brute Ratel by ransomware actors raised concerns that it would soon replace Cobalt Strike in malicious actors’ toolboxes.
Those fears did not come to fruition. In September of 2022, a full copy of Brute Ratel version 1.2.2 (codenamed “Scandinavian Defense”) was uploaded to Virus Total by a user in Ukraine, making it available to researchers for analysis. Even then, it was rarely encountered; in an examination of Sophos endpoint detection data from September 2022 to March 2023, we found less than 20 unique detections of Brute Ratel in customer telemetry—excluding threat simulations and other security testing. Sophos’ incident response team dealt with only two cases in 2022 where Brute Ratel played a role.
In an examination of samples generally associated with Brute Ratel attacks, I found a small number of cases where threats that were later identified as Brute Ratel-related were blocked based on behavior or file analysis as generic malware. Based on an analysis of the telemetry, these cases were associated with attack simulations and testing by security teams, and not with actual attacks.
On the other hand, the long-leaked and reverse-engineered offensive security tool Cobalt Strike seems to have gained even more adoption, and remains a common factor in many incidents, including ransomware attacks. There were thousands of instances over the same period where Cobalt Strike was detected.
That is not to say that Brute Ratel has not been seen used by threat actors at all—rather, the cases where it has been seen have been well-resourced attackers targeting specific organizations. The Polish government recently identified a cyberespionage campaign—alleged to be connected to Russian intelligence services—that used a combination of Brute Ratel and Cobalt Strike in at least one case. (Sophos has updated detections for Brute Ratel based on this incident.) However, there have been few other recent cases, and none involving smaller cybercriminal organizations.
What the market will badger
Brute Ratel, like Cobalt Strike, is a post-exploitation tool—in order to do anything with it, a user has to have already gained initial access. That access can be provided in a number of ways, including email attachments that install an attack payload when opened or existing vulnerabilities on an Internet-exposed server. But once delivered, Brute Ratel provides a well-documented and polished set of tools to move beyond that initial landing point (although some posters on underground boards used colorful language when complaining about its user interface).
Brute Ratel has been marketed with claims of being able to evade enhanced detection and response (EDR) platforms. As of six months ago, Brute Ratel developer Chetan Nayak claimed that its “badger” agent had not been detected by any antivirus software. So, naturally, there’s been some interest in Brute Ratel from the criminal world.
Various versions of Brute Ratel have found their way to criminal marketplaces despite updates by the developer that allegedly prevent license abuse—including some sellers who offer it as a service. Prices range from $4,000 for the full suite of a recent version ($1,000 more than the developer’s price) to $2,250 per year as a service (plus a $500 C2 server set-up fee).
In comparison, there are many leaked versions of Cobalt Strike freely available on both dark web and public sites (though some of the more public postings have been taken down as the result of Digital Millennium Copyright Act takedown requests). Version 4.7’s code has been in the wild since the fall of 2022 through file-sharing sites; later versions are also available for sale for a range of prices, including as-a-service offerings starting at $5,000. But cracked versions of Cobalt Strike’s components are widely available, so only those threat actors with less experience are likely to pay someone for it.

This is probably why we see so many Cobalt Strike detections in our telemetry. Cobalt accounted for about 20 percent of signature-based attack tool detections in Sophos telemetry in the first quarter of 2023. There were hundreds of actual incidents involving Cobalt Strike (discounting simulations and analyst uploads) during that period. In comparison, there was only one such detection of Brute Ratel during the same period.
Even so, Cobalt Strike is not the most frequently used post-access offensive security framework used by attackers. There are other open source and commercially supported post-exploitation tools available, some of which have occasionally been positioned as Cobalt Strike replacements. The most frequently encountered of these are two well-known open-source toolkits—PowerSploit and Empire—which typically require some other command and control tool (or a remote shell over RDP or another remote access tool) to be used.
And then there is Metasploit, usable both for vulnerability exploitation and post-exploit operations through “Meterpreter” agents (including customized versions that have been built from its open-source code). Meterpreter detections, including malicious agents built using the Meterpreter command and control protocols, were far more common in both signature-based and behavior-based detections over the last six months, as shown in the graphs below. Also seen (but much less frequently) is Sliver, another open-source “adversary emulation” framework. Sliver file detections have approached Cobalt Strike detections in frequency, sometimes exceeding them—as they have in the past two months.
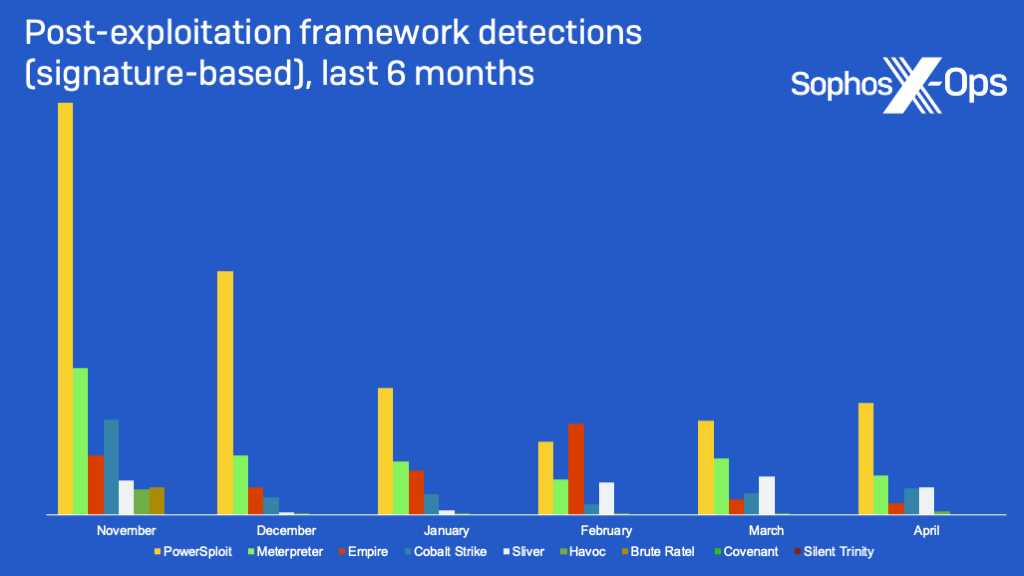
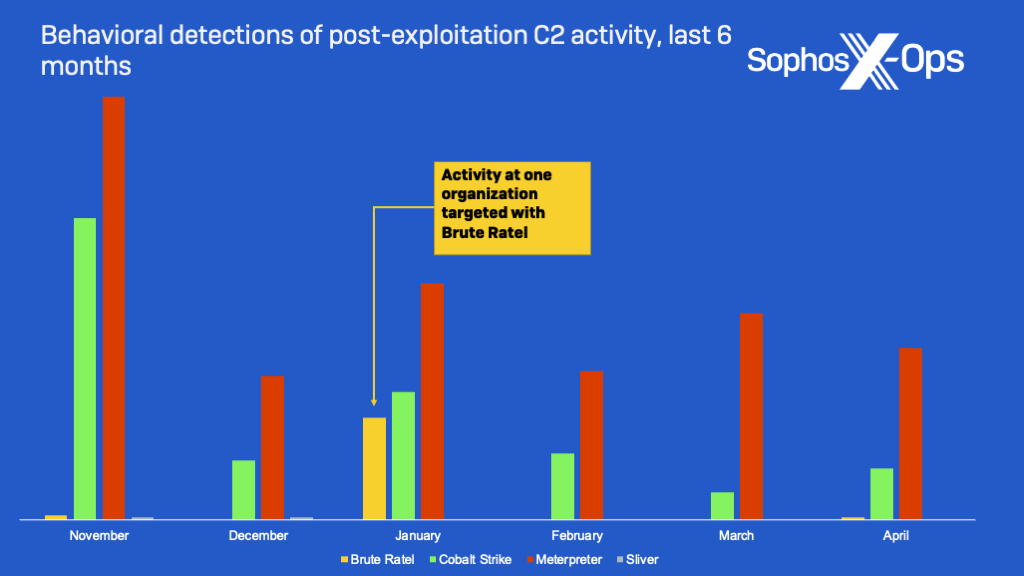
Brute Ratel behavioral detections were also extremely rare. Most of the signature-based detections we saw were likely related to samples downloaded for analysis or some attempts to distribute payloads by email. And the most significant group of actual command and control (C2) related behavior we saw related to Brute Ratel came from a single incident in January, where a previously unseen script was used to inject a “badger” beacon.
Brute Awakening
On January 1, a Windows server at a managed service provider executed a script file extracted from a .zip file:
\Temp1_Julie Ramzel_1040_1120s 2019-2021.zip\passwords_Julie Ramzel_1040_1120s 2019-2021.js”
A file with the same name was also detected as part of a blocked Brute Ratel launch at another organization on the same date, and other threat researchers have encountered it as well in the same timeframe—indicating that it was part of a campaign by a particular threat actor. The same file was uploaded to Virus Total on January 10 by two unrelated .The same file, with the same filename, was uploaded to Virus Total on January 10 by two unrelated parties.
In addition to the script file, the .zip archive contained a PDF; it was encrypted and we could not analyze its contents. But the script itself was highly obfuscated JS which injected the “badger” implant code into notepad.exe.
Once injected, the agent made an HTTPS POST connection to two URIs, sending encoded data:
- prefectrespond[.]online/share.php (still active at 5.161.100.208. on a German ISP)
- instrumentation-database-fc-lows[.]trycloudflare.com/share[.]php(now down)
The communication was detected as a Brute Ratel call-home and blocked by a behavioral rule. But the script remained running, and re-attempted connections repeatedly while continuously being blocked. Sophos reported the behavior to the MSP, and the issue was resolved by the MSP’s security team. The .zip that delivered the injection script and the obfuscated JavaScript script itself are now blocked by file rules as well as behavior.
The same day, there was a similar attack attempt blocked by behavioral rules for Brute Ratel attempting communication with the same C2 server in Germany. The only other behavioral detection in the past six months was in November, and appeared to be someone experimenting with the malware on a home system.
Why so scarce?
There are multiple probable factors contributing to the gap between detected Cobalt Strike and Brute Ratel detections and incidents. Firstly, because of Brute Ratel’s favored deployment methods, many attacks that could be based on Brute Ratel are detected based on generic malware behavior by scripts and shellcode. That means that we never get to see the signatures and behaviors related to Brute Ratel agents.
Other factors are likely related to the continued success attackers have using the widely available cracked and reverse-engineered versions of Cobalt Strike, the limited distribution of fraudulently obtained Brute Ratel tools, and a desire by threat actors to limit Brute Ratel usage to targeted attacks where other tools (including Cobalt Strike) had failed.
Even among well-resourced ransomware actors, the use of Brute Ratel has become rare. There are a number of possible reasons for this:
- Distaste for the tool among threat actors. There have been negative comments about Brute Ratel’s interface and features on underground forums, and actors who have experience with other tools may not feel that a change is worth the learning curve.
- The leaking of cracked Brute Ratel code to VirusTotal has made it widely available to researchers and information security vendors, so the types of targets that threat actors would have used Brute Ratel against—organizations with managed detection and response platforms that Brute Ratel claims to bypass—were quickly hardened against it. This would explain the rapid drop-off in file-based detections in the fall timeframe.
- The efforts made by Brute Ratel’s developer to prevent follow-on versions of the tool from being “cracked” and widely abused may have prevented further illicit distribution, and only threat actors capable of concealing their purchase through a front company have access to newer versions.
- Success with the cracked Brute Ratel at this point is dependent on evading file detection and behavioral detection, so attackers who are still using it may be avoiding deploying it when Sophos and other detection tools are present or are focusing on using other methods to attempt to bypass those detections. This limits use to a relatively small number of skilled threat actors.
While this means that Brute Ratel is not the widespread threat that it was once feared to become, it does not mean that the tool is not in use or that defenders should be complacent about its use.
Sophos detects Brute Ratel-related threats by signature (ATK/Brutel) and by behavioral and memory detection. We continue to monitor its usage and work to defend against both legitimate and malicious deployments of the tool to better defend networks. Indicators of compromise related to the cases we have mentioned in this post can be found on the SophosLabs Github page.