4 Tips for Better AWS Cloud Workload Security
Credit to Author: Hoa Nguyen| Date: Thu, 23 Mar 2023 00:00:00 +0000
Discover the challenges of AWS cloud workload security and the various technologies that can alleviate them.
Read moreCredit to Author: Hoa Nguyen| Date: Thu, 23 Mar 2023 00:00:00 +0000
Discover the challenges of AWS cloud workload security and the various technologies that can alleviate them.
Read more
Credit to Author: Paul Ducklin| Date: Thu, 23 Mar 2023 17:59:21 +0000
Listen now – latest episode. Full transcript inside.
Read moreCredit to Author: Jon Clay| Date: Thu, 23 Mar 2023 00:00:00 +0000
Misconfigured cloud and IT assets open the door to a wide range of cyber risks. Automated, continuous cybersecurity monitoring lets organizations watch accounts and systems for exposures in real time and maintain strong attack surface risk management.
Read moreCredit to Author: Brianna McGovern| Date: Thu, 23 Mar 2023 16:00:00 +0000
The latest Microsoft Defender for Business innovations offer new security features for small and medium-sized businesses so they can focus on what they care about most.
The post Microsoft continues to innovate to help secure small businesses appeared first on Microsoft Security Blog.
Read more
Credit to Author: Lily Hay Newman| Date: Wed, 22 Mar 2023 22:25:18 +0000
Image-editing tools from Google and Microsoft contain the “aCropalypse” bug, which can reveal information users intentionally removed.
Read moreCredit to Author: Vickie Su| Date: Thu, 23 Mar 2023 00:00:00 +0000
After months of investigation, we found that several undisclosed malware and interesting tools used for exfiltration purposes were being used by Earth Preta. We also observed that the threat actors were actively changing their tools, tactics, and procedures (TTPs) to bypass security solutions. In this blog entry, we will introduce and analyze the other tools and malware used by the threat actor.
Read moreCategories: Threat Intelligence Tags: Magecart Tags: skimmer Tags: Kritect Tags: Magento Compromised online stores have been injected with skimmers hiding around the Google Tag Manager script. We identified a new one that looked similar at first but is part of a different campaign. |
The post New Kritec Magecart skimmer found on Magento stores appeared first on Malwarebytes Labs.
Read moreCategories: Exploits and vulnerabilities Categories: News Tags: Google Tags: Pixel Tags: Markup Tags: CVE-2023-21036 Tags: recover Tags: PNG Tags: truncated A vulnerability in the Markup tool that comes pre-installed on Pixel phones allows anyone with access to the edited image to view parts of the original. |
The post Google Pixel: Cropped or edited images can be recovered appeared first on Malwarebytes Labs.
Read more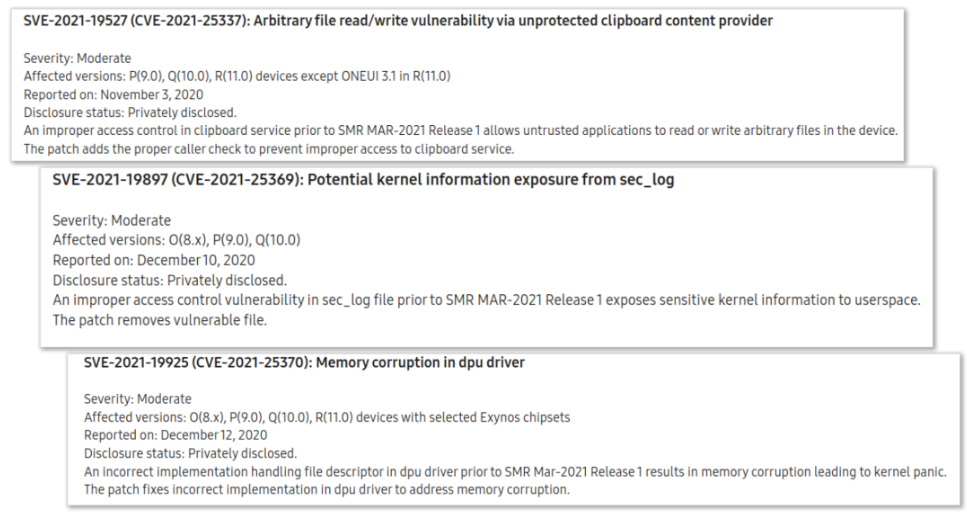
Credit to Author: BrianKrebs| Date: Wed, 22 Mar 2023 23:11:08 +0000
Google says it has suspended the app for the Chinese e-commerce giant Pinduoduo after malware was found in versions of the app. The move comes just weeks after Chinese security researchers published an analysis suggesting the popular e-commerce app sought to seize total control over affected devices by exploiting multiple security vulnerabilities in a variety of Android-based smartphones.
Read more
Credit to Author: Paul Ducklin| Date: Wed, 22 Mar 2023 17:59:10 +0000
Turns out that the Windows 11 Snipping Tool has the same “aCropalypse” data leakage bug as Pixel phones. Here’s how to work around the problem…
Read more