3CX users under DLL-sideloading attack: What you need to know
Credit to Author: Greg Iddon| Date: Thu, 30 Mar 2023 01:39:11 +0000
Sophos X-Ops is tracking a developing situation concerning a seeming supply-chain attack against the 3CX Desktop application, possibly undertaken by a nation-state-related group. This page provides an overview of the situation, a threat analysis, information for hunters, and information on detection protection.
We will update this page as events and understanding develop, including our threat and detection guidance.
[First version published 7pm PDT 29-March-2023]
Overview
The affected software is 3CX – a legitimate software-based PBX phone system available on Windows, Linux, Android, and iOS. The application has been abused by the threat actor to add an installer that communicates with various command-and-control (C2) servers.
The software is a digitally signed version of the softphone desktop client for Windows and is packaged with a malicious payload. The most common post-exploitation activity observed to date is the spawning of an interactive command shell.
At present, the only platform confirmed by our customer data to be affected is Windows.
Threat analysis
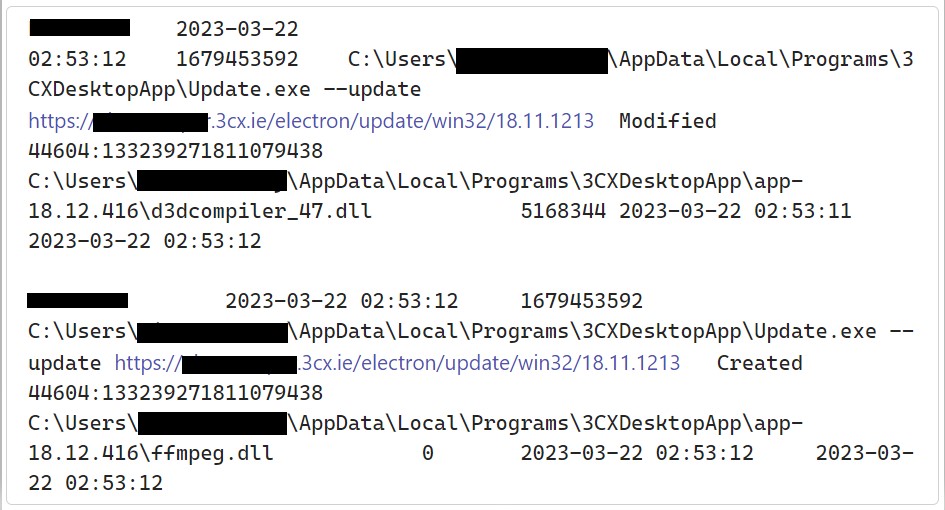
On March 22, users of 3CX began discussion of potential false-positive detections of 3CXDesktopApp by their endpoint security agents.
Figure 1: The update process at the moment the malicious version drops
Sophos MDR first identified malicious activity directed at its own customers and stemming from 3CXDesktopApp on March 29, 2023. Additionally, Sophos MDR has observed the campaign leveraging a public file storage to host encoded malware. This repository has been in use since December 8, 2022.
The attack revolves around a DLL sideloading scenario, one with a remarkable number of components involved. This is likely to ensure that customers were able to use the 3CX desktop package without noticing anything unusual about the affected package. To date, we have identified three crucial components:
- 3CXDesktopApp.exe, the clean loader
- d3dcompiler_47.dll, a DLL with an appended encrypted payload
- ffmpeg.dll, the Trojanized malicious loader
The file ffmpeg.dll contains an embedded URL which retrieves a malicious encoded .ico payload.
In a normal DLL sideloading scenario, the malicious loader (ffmpeg.dll) would replace the clean dependency; its only function would be to queue up the payload. However, in this case, that loader is entirely functional, as it would normally be in the 3CX product – instead, there’s an additional payload inserted at the DllMain function. This adds bulk, but may have lowered suspicions – the 3CX application functions as expected, even as the Trojan addresses the C2 beacon.
Hunting information
Determining impact with Sophos XDR
Determining whether hosts have communicated with threat actor infrastructure
The below query will search for hosts that have communicated with the various known URLs in use by this campaign. (The URLs are slightly obfuscated with brackets, which should be removed before the query is run.)
SELECT meta_hostname, sophos_pids, domain, clean_urls, source_ips, destination_ips, timestamps, ingestion_timestamp FROM xdr_data WHERE query_name = 'sophos_urls_windows' AND (LOWER(domain) = 'akamaicontainer[.]com' OR LOWER(domain) = 'akamaitechcloudservices[.]com' OR LOWER(domain) = 'azuredeploystore[.]com' OR LOWER(domain) = 'azureonlinecloud[.]com' OR LOWER(domain) = 'azureonlinestorage[.]com' OR LOWER(domain) = 'dunamistrd[.]com' OR LOWER(domain) = 'glcloudservice[.]com' OR LOWER(domain) = 'journalide[.]org' OR LOWER(domain) = 'msedgepackageinfo[.]com' OR LOWER(domain) = 'msstorageazure[.]com' OR LOWER(domain) = 'msstorageboxes[.]com' OR LOWER(domain) = 'officeaddons[.]com' OR LOWER(domain) = 'officestoragebox[.]com' OR LOWER(domain) = 'pbxcloudeservices[.]com' OR LOWER(domain) = 'pbxphonenetwork[.]com' OR LOWER(domain) = 'pbxsources[.]com' OR LOWER(domain) = 'qwepoi123098[.]com' OR LOWER(domain) = 'sbmsa[.]wiki' OR LOWER(domain) = 'sourceslabs[.]com' OR LOWER(domain) = 'visualstudiofactory[.]com' OR LOWER(domain) = 'zacharryblogs[.]com' OR (LOWER(domain) = 'raw.githubusercontent[.]com' AND LOWER(clean_urls) LIKE '%/iconstorages/images/main/%'))
We also recommend that users of 3CX’s software monitor the company’s communications channels; they have a blog and also a support-and-information forum.
A list of IOCs for this attack is published on our GitHub.
Detection protection
SophosLabs has blocked the malicious domains as well as published the following endpoint detection:
- Troj/Loader-AF
We have also blocked the list of known C2 domains associated with the threat and will continue to add to that list in the IOC file on our GitHub, as noted above. Finally, the malicious ffmpeg.dll file is flagged as being of low reputation.
SophosLabs is actively investigating additional detection opportunities for activity stemming from this software. In addition, for customers of Sophos MDR, the MDR Detection Engineering team has a variety of behavioral detections in place that will detect follow up activity.