A little something for everyone on a patchwork Patch Tuesday
Credit to Author: Angela Gunn| Date: Tue, 14 Mar 2023 18:58:33 +0000
Microsoft on Tuesday released patches for 73 vulnerabilities in ten product families, including 6 Critical-severity issues in Windows. As is the custom, the largest number of addressed vulnerabilities affect Windows, with 54 CVEs. Dynamics follows with 6 CVEs; followed by Office (4), Azure and SharePoint (2 each), and MMPE (1). In an unusually wide-ranging month, there are also patches for other platforms entirely – Android (3), iOS (1), and macOS (1).
At patch time, just one of the issues this month has been publicly disclosed, and only two appear to be under exploit in the wild: CVE-2023-23397, an Important-severity spoofing issue in Outlook, and CVE-2023-24880, a Moderate-severity security feature bypass in Windows SmartScreen. However, Microsoft cautions that seven of the issues addressed are more likely to be exploited in either the latest or earlier versions of the affected product soon (that is, within the next 30 days).
And surprises happen, after all: Microsoft is currently contending with not one but two publicly revealed proofs of concept for recently patched issues — January’s CVE-2023-21768 and February’s CVE-2023-21716 – the latter of which was dubbed “less likely” to be exploited soon when the patch was released just 28 days ago.
By the numbers
- Total Microsoft CVEs: 73
- Total advisories shipping in update: 0
- Publicly disclosed: 1
- Exploited: 2
- Exploitation more likely in latest version: 6
- Exploitation more likely in older versions: 1
- Severity
- Critical: 6
- Important: 66
- Moderate: 1
- Impact
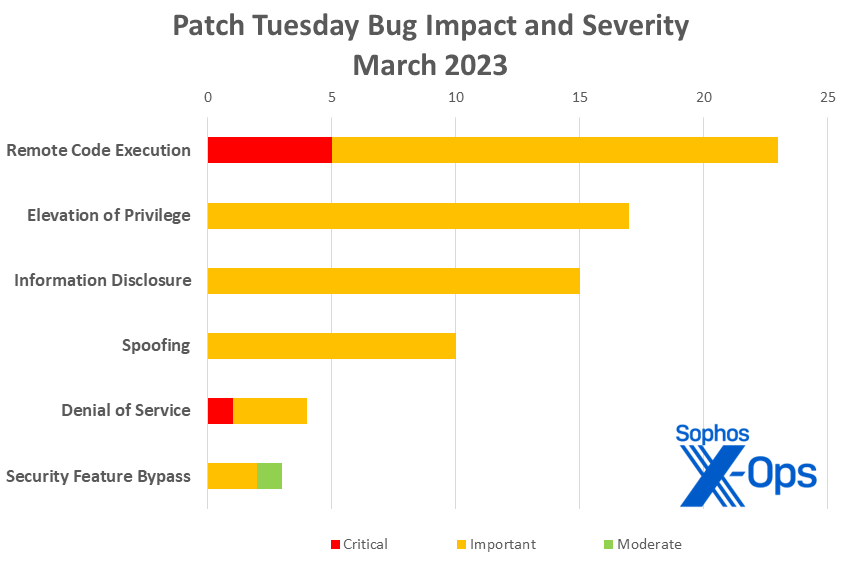
- Remote Code Execution: 24
- Elevation of Privilege: 17
- Information Disclosure: 15
- Spoofing: 10
- Denial of Service: 4
- Security Feature Bypass: 3
Figure 1: As it did last month, remote code execution issues make up the largest portion of March 2023’s patches from Microsoft
Products
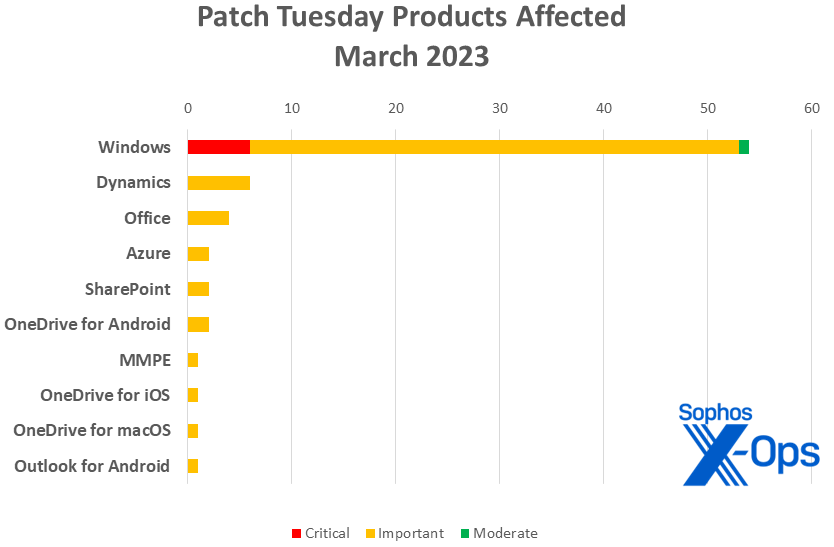
- Windows: 54
- Dynamics: 6
- Office: 4 (one shared with SharePoint)
- Azure: 2
- SharePoint: 2 (one shared with Office)
- OneDrive for Android: 2
- MMPE: 1
- OneDrive for iOS: 1
- OneDrive for macOS: 1
- Outlook for Android: 1
This month’s release also included information on four Important-severity GitHub CVEs affecting Visual Studio. Microsoft provided information on the four (CVE-2023-22490, CVE-2023-22743, CVE-2023-23618, and CVE-2023-23946) mainly to reassure administrators that the latest builds of Visual Studio are no longer susceptible to those issues. These four CVEs are not reflected in the monthly statistics. Neither is the sole Edge patch this month (CVE-2023-24892), which addresses an Important-class spoofing issue; nor are two other issues (CVE-2023-1017, CVE-2023-1018) believed to be related to a vendor-specific implementation of TPM.
Figure 2: Windows patches make up two-thirds of the March 2023 load, including all of the Critical-class issues
Notable March updates
CVE-2023-23397 – Microsoft Outlook Spoofing Vulnerability
This issue, which has a 9.1 CVSS base score despite being classified by Microsoft as Important-severity, is one of the two for which exploitation has already been detected. To exploit this vulnerability, an attacker would send a maliciously crafted email that would create a connection from the victim to an external UNC location under the attacker’s control. This connection would leak the Net-NTLMv2 hash of the victim to the attacker, who could then relay this hash to another service and thus authenticate as the victim. Unfortunately, no user interaction is required to cause this. In fact, a skilled attacker could send an email that triggers the vulnerability when it is retrieved and processed by the email server – in other words, even before it reaches the Preview Pane, let alone is opened.
CVE-2023-24880 – Windows SmartScreen Security Feature Bypass Vulnerability
The other issue in March’s patch collection for which exploitation has been detected (and the only one publicly disclosed), this is a Moderate-class issue in SmartScreen. A defender looking to evade SmartScreen’s reputation checks could craft a file that evades Mark of the Web (MotW) tagging defenses, allowing an image originating from the Internet to be treated as trusted.
CVE-2023-23411 – Windows Hyper-V Denial of Service Vulnerability
Another no-user-interaction-required issue, though fortunately this Critical-class Hyper-V issue requires attackers to achieve a local attack vector for success. Once accomplished, though, total loss of host availability is at hand.
CVE-2023-23392 – HTTP Protocol Stack Remote Code Execution Vulnerability
One of the issues Microsoft believes to be more likely to be exploited within 30 days of patch release, this Critical-class RCE is remotely exploitable and requires no user interaction or system privileges. A successful attacker would exploit this by sending a maliciously crafted packet to a targeted server that uses the http.sys (the HTTP Protocol Stack) to process packets. Interestingly, this issue affects only the latest versions of the operating system (Windows 11, Windows Server 2022).
CVE-2023-23403, CVE-2023-23406, CVE-2023-23413, CVE-2023-24856, CVE-2023-24857, CVE-2023-24858, CVE-2023-24863, CVE-2023-24864, CVE-2023-24865, CVE-2023-24866, CVE-2023-24867, CVE-2023-24868, CVE-2023-24870, CVE-2023-24872, CVE-2023-24876, CVE-2023-24906, CVE-2023-24907, CVE-2023-24909, CVE-2023-24911, and CVE-2023-24913 (various titles)
What do these twenty patches have in common? PostScript. All twenty of these involve PostScript printer drivers, and one (CVE-2023-23403) touches PCL Class 6 printer drivers as well. Nine vulnerabilities can lead to remote code execution, with 10 allowing information disclosure and one permitting elevation of privilege. Microsoft rates the severity of all 20 as Important, but their CVSS base scores range from a medium-level 5.4 information disclosure (CVE-2023-24857) to two RCEs weighing in at a concerning 9.8 (CVE-2023-23406, CVE-2023-24867). Another issue, CVE-2023-24876, is deemed to be more likely to see exploitation in the next thirty days. Remarkably, just four researchers are responsible for all these finds: Zhiniang (Edward) Peng, Zesen Ye, kap0k, and (from Microsoft’s own MSRC team) Adel.
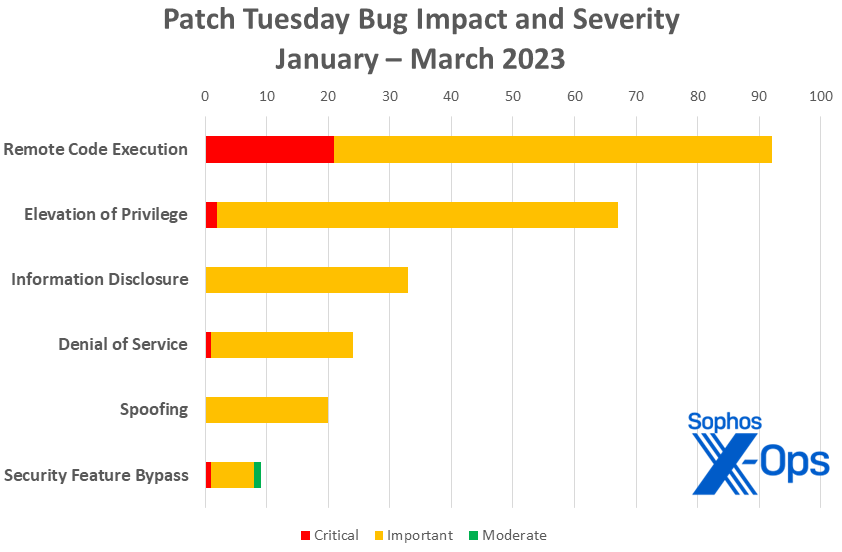
Figure 3: As the year goes on, remote code execution flaws account for the largest number of patches overall and the largest number of critical-severity patches so far. Note that the total number of spoofing vulnerabilities addressed in 2023 doubles with this month’s release
Sophos protections
For CVE-2023-23416, the signatures for both Sophos Intercept X/Endpoint IPS and Sophos XGS Firewall are silent detections (monitoring telemetry).
As you can every month, if you don’t want to wait for your system to pull down Microsoft’s updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your specific system’s architecture and build number.