January 2023 patch roundup: Microsoft tees up 98 updates
Credit to Author: Angela Gunn| Date: Wed, 11 Jan 2023 02:05:40 +0000
Microsoft on Tuesday released patches for 98 vulnerabilities in nine Microsoft product families. This includes 11 Critical-severity issues affecting SharePoint and Windows. Once again the majority of CVEs affect Windows; the operating system accounts for 66 CVEs. It’s followed by 3D Builder, a less-common Patch Tuesday target, with 14 Important-severity RCE issues. (3D Builder was installed by default on Windows 10, but not on earlier or later versions of the OS.)
As for the rest, Office and Exchange pick up six and five patches respectively (all Important-severity), SharePoint receives three fixes, and Azure, Microsoft’s Malware protection Engine, .NET, and Visual Studio each pick up one.
Microsoft also announced one previously issued patch addressing a Moderate-severity RCE sandbox escape affecting that Chromium-based Edge browser; as is customary with Patch Tuesday releases, this issue is not counted among the 98 and requires no action as part of the release itself.
Despite a high total number of patches, so far the 98 issues addressed have apparently flown under the radar for the most part. Just one issue addressed this month (CVE-2022-21674, an Important-severity Windows EoP) has been discovered to be under exploit, and even then there appears to be no disclosed code addressing this ALPC (Advanced Local Procedure Call) bug.
That said, Microsoft’s own severity ratings may not tell the entire tale. Five of this month’s Windows patches garnered a Critical-severity 9.8 CVSS (Common Vulnerability Scoring System) base score, a consideration for many administrators looking to prioritize their task lists. Four of those five patches touch Windows Layer 2 Tunnelling Protocol (L2TP); all five involve remote code execution issues, and all five require neither user interaction nor privileged access to exploit. L2TP is also at the heart of two additional patches in this month’s set, and users of Microsoft’s VPN services are encouraged to regard those L2TP patches seriously.
Today is also the final day of Patch Tuesday activity for Windows 7, as the end of Extended Security Update support brings the long life of that version of the operating system to a close. (Mainstream support for Win 7 ended in 2020; the end of ESU means that even crucial security updates will no longer be regularly issued.) Support is also concluding for Windows 8, 8.1, and RT, which were not granted an ESU of their own. Of this month’s patches, 42 apply to Win7, and 48 apply to at least one version of Win8.
Elsewhere in patching news, Microsoft also relayed information on 15 issues addressed today by patches for Adobe Acrobat and Reader for Windows and MacOS – the first Reader patches released since October 2021. All 15 affect Reader versions 22.003.20282 (Windows), 22.003.20281 (Mac), and earlier, and Acrobat versions 20.005.30418 and earlier. None of the 15 are known to be under active exploit in the wild. The specifics of the vulnerabilities do, however, vary somewhat, with 4 out-of-bounds reads, 2 out-of-bounds writes, and a pair of violations of secure design principles among the issues addressed. Adobe also today released patches for Dimension, InDesign, and InCopy. More information on Adobe patches is available from the company’s site.
By the Numbers
- Total Microsoft CVEs: 98
- Total advisories shipping in update: 0
- Publicly disclosed: 0
- Exploitation detected: 1
- Exploitation more likely in latest version: 7
- Exploitation more likely in older versions: 4
- Severity
- Critical: 11
- Important: 87
- Impact
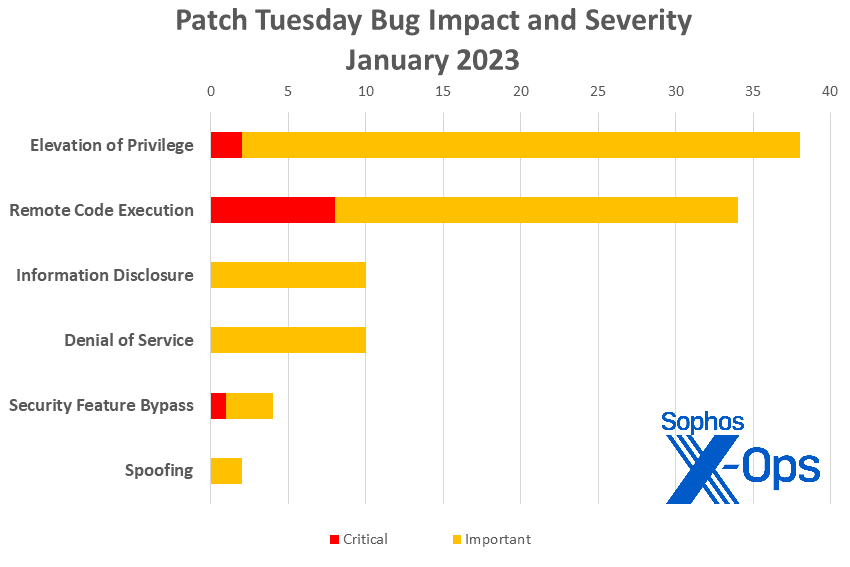
- Elevation of Privilege: 38
- Remote Code Execution: 34
- Information Disclosure: 10
- Denial of Service: 10
- Security Feature Bypass: 4
- Spoofing: 2
Figure 1: 2023 opens with a higher–than–usual number of Information Disclosure issues, but Elevation of Privilege and Remote Code Execution still rule the roost
Products affected:
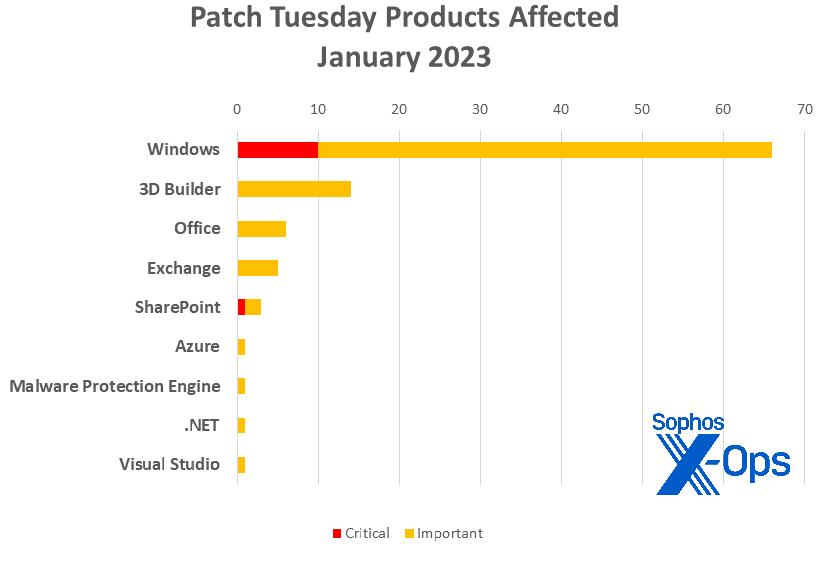
- Microsoft Windows: 66
- 3D Builder: 14
- Microsoft Office: 6
- Microsoft Exchange: 5
- SharePoint: 3
- Azure: 1 (not including 70 Windows patches applicable to Windows Server 2022 Datacenter: Azure Edition)
- Malware Protection Engine: 1
- .NET: 1
- Visual Studio: 1
Figure 2: Windows gets a variety of patches this month, dwarfing requirements for other product families
Notable January Updates
CVE-2023-21743: Microsoft SharePoint Server Security Feature Bypass Vulnerability
The only Critical-severity issue among January’s three SharePoint patches, this issue – which would allow an unauthenticated user to make an anonymous connection to a specific SharePoint server — is marked by Microsoft as being more likely to be exploited within the first thirty days after Patch Tuesday. This makes implementing this patch a priority for administrators, but Microsoft notes that there are extra manual steps to the patching process: Customers must also trigger a SharePoint upgrade action in conjunction with this patch. This required upgrade action can be triggered by running the SharePoint Products Configuration Wizard, the Upgrade-SPFarm PowerShell cmdlet, or the “psconfig.exe -cmd upgrade -inplace b2b” command on each SharePoint server after installing the update.
CVE-2023-21531, Azure Service Fabric Container Elevation of Privilege Vulnerability
This Important-class issue is fairly specific in its parameters: Only users who implement the Docker app containers are affected, and an attacker would first have to be present on the system with root access, and the targeted environment would have to be already set up in a specific fashion. If successful, the attacker would gain control over the Service Fabric cluster in question, but not to elevate privileges outside that compromised cluster. All that said, the bulletin does flag that the patch restricts access to a specific internal Azure platform resource (168.63.129.16), and that admins should check to make sure they’re not making calls or requests to that IP address before proceeding with the patch since once the patch is enabled, requests from the cluster to that specific resource will fail.
CVE-2023-21559, Windows Cryptographic Services Information Disclosure Vulnerability
CVE-2023-21678, Windows Print Spooler Elevation of Privilege Vulnerability
Two otherwise unremarkable Important-severity vulnerabilities, these are mainly interesting because of their credited finders; respectively, Canada’s Communications Security Establishment (CSE) and the US’s National Security Agency (NSA).
Sophos protections
As you can every month, if you don’t want to wait for your system to pull down Microsoft’s updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your particular system’s architecture and build number.