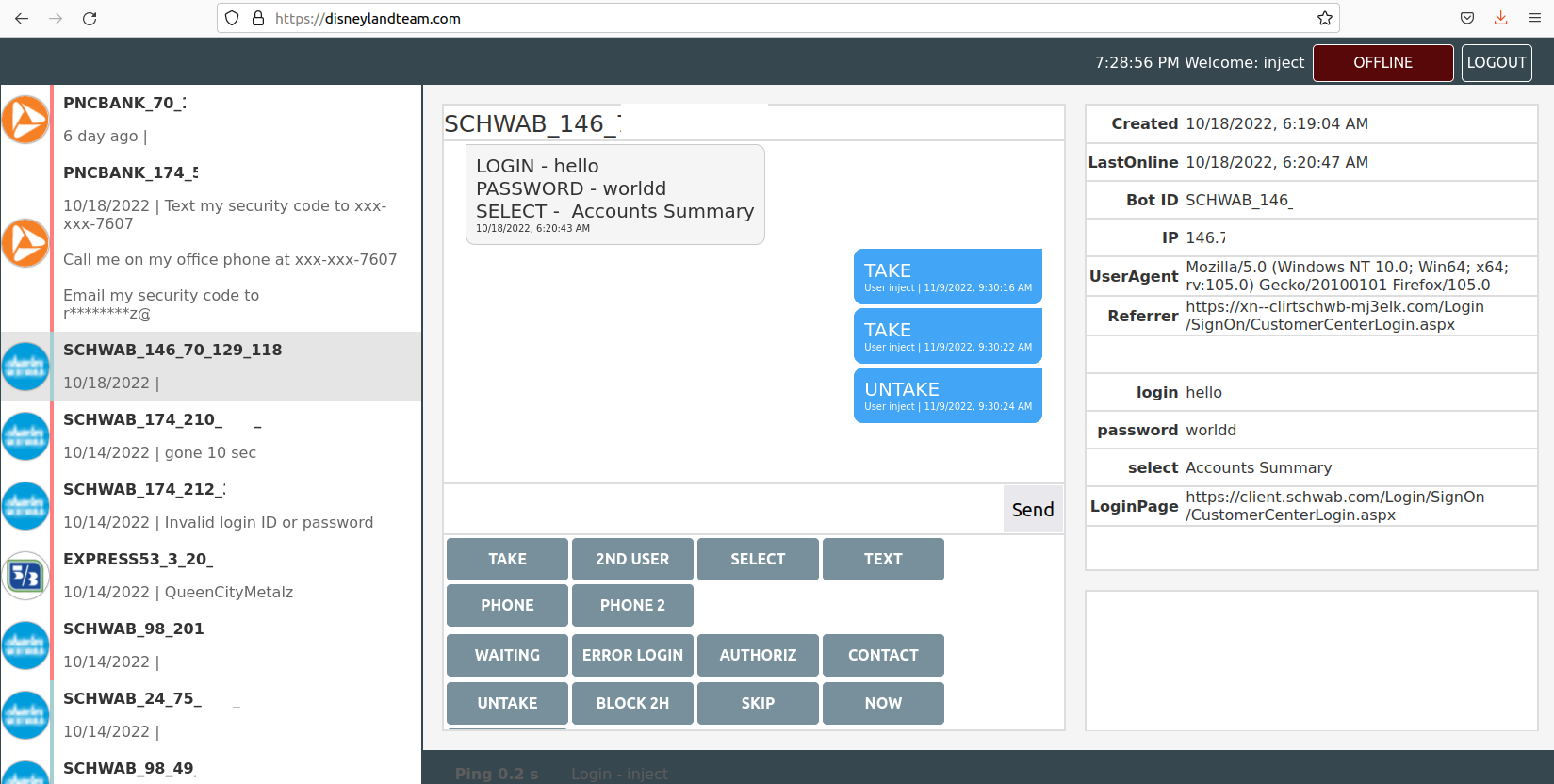
DEV-0569 finds new ways to deliver Royal ransomware, various payloads
Credit to Author: Microsoft 365 Defender Threat Intelligence Team| Date: Thu, 17 Nov 2022 17:00:00 +0000
DEV-0569’s recent activity shows their reliance on malvertising and phishing in delivering malicious payloads. The group’s changes and updates in delivery and payload led to distribution of info stealers and Royal ransomware.
The post DEV-0569 finds new ways to deliver Royal ransomware, various payloads appeared first on Microsoft Security Blog.
Read more



 Cybercrimes have been on the rise post-pandemic and are becoming even more sophisticated. Digitization and work from home…
Cybercrimes have been on the rise post-pandemic and are becoming even more sophisticated. Digitization and work from home…