A lighter Patch Tuesday, but one heavy with remote code execution bugs
Credit to Author: Matt Wixey| Date: Tue, 13 Sep 2022 18:38:14 +0000
Microsoft on Tuesday released patches for 62 vulnerabilities in nine Microsoft product families, making this a relatively light Patch Tuesday. All but two bugs are rated Critical or Important in severity, with the majority (36) affecting Windows.
Only one vulnerability in the release, CVE-2022-37969, has been publicly disclosed. This is an elevation of privilege vulnerability in the Windows Common Log File System (CLFS) Driver, and according to Microsoft, is also the only bug in this month’s update to have been exploited.
There are five Critical-class vulnerabilities this month, all of which are remote code execution bugs. Two of these (CVE-2022-34700 and CVE-2022-35805) are in Microsoft Dynamics 365 (on-premises), and another two (CVE-2022-34721 and CVE-2022-34722) are in Windows Internet Key Exchange (IKE). The standout is CVE-2022-34718, covered in more detail below, which is an unauthenticated remote code execution vulnerability in Windows TCP/IP. It’s the only Critical-class bug which is listed as more likely to be exploited (although not for older software releases).
By the numbers
- Total Microsoft CVEs: 62
- Publicly disclosed: 1
- Exploited: 1
- Exploitation more likely: 7 (older and/or newer product versions)
- Severity
- Critical: 5
- Important: 56
- Moderate: 1
- Low: 0
- Impact
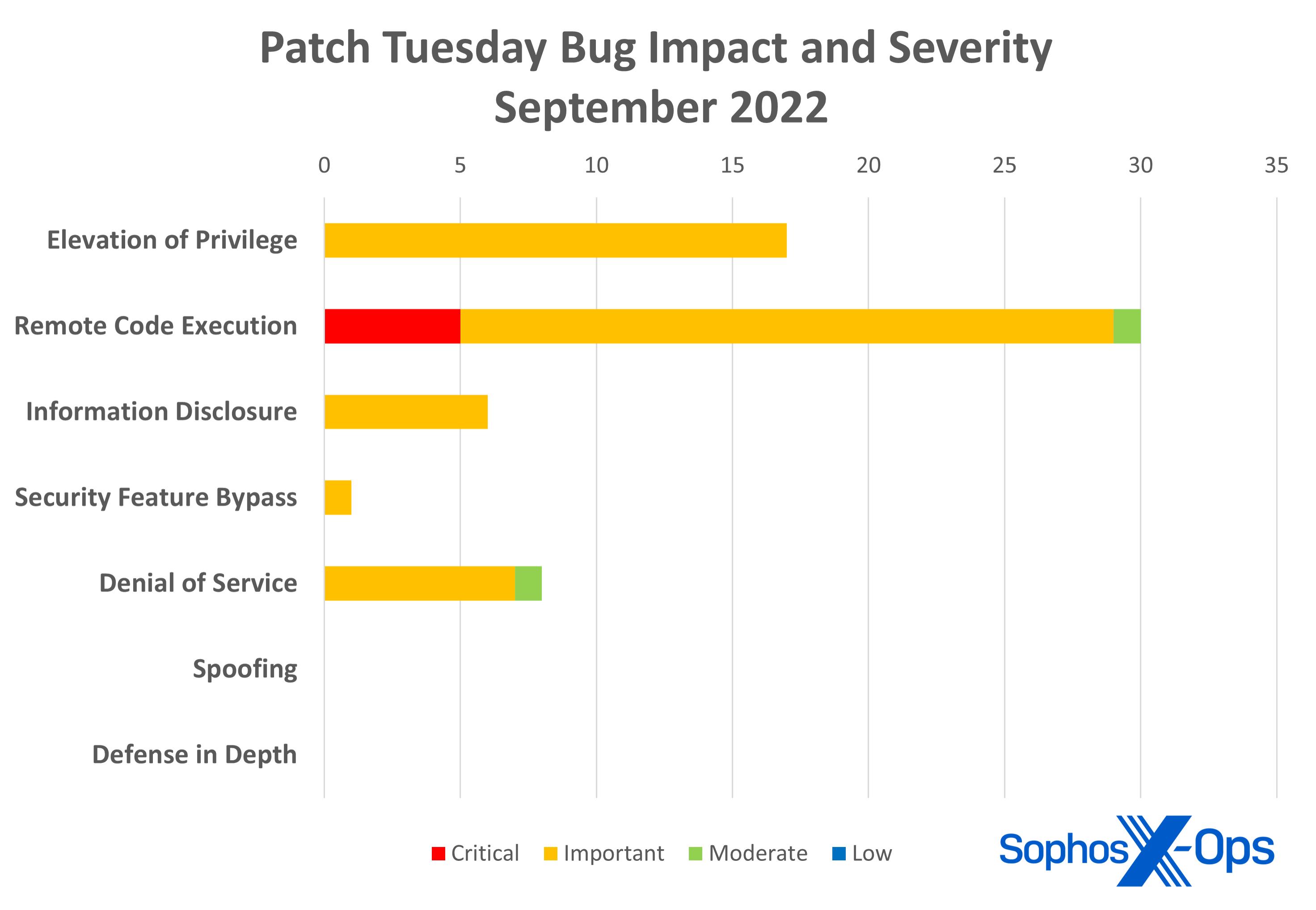
- Remote Code Execution: 30
- Elevation of Privilege: 17
- Denial of Service: 8
- Information Disclosure: 6
- Security Feature Bypass: 1
Figure 1: Important remote code execution vulnerabilities make up the majority of this month’s numbers, with all five critical bugs also being remote code execution
Products
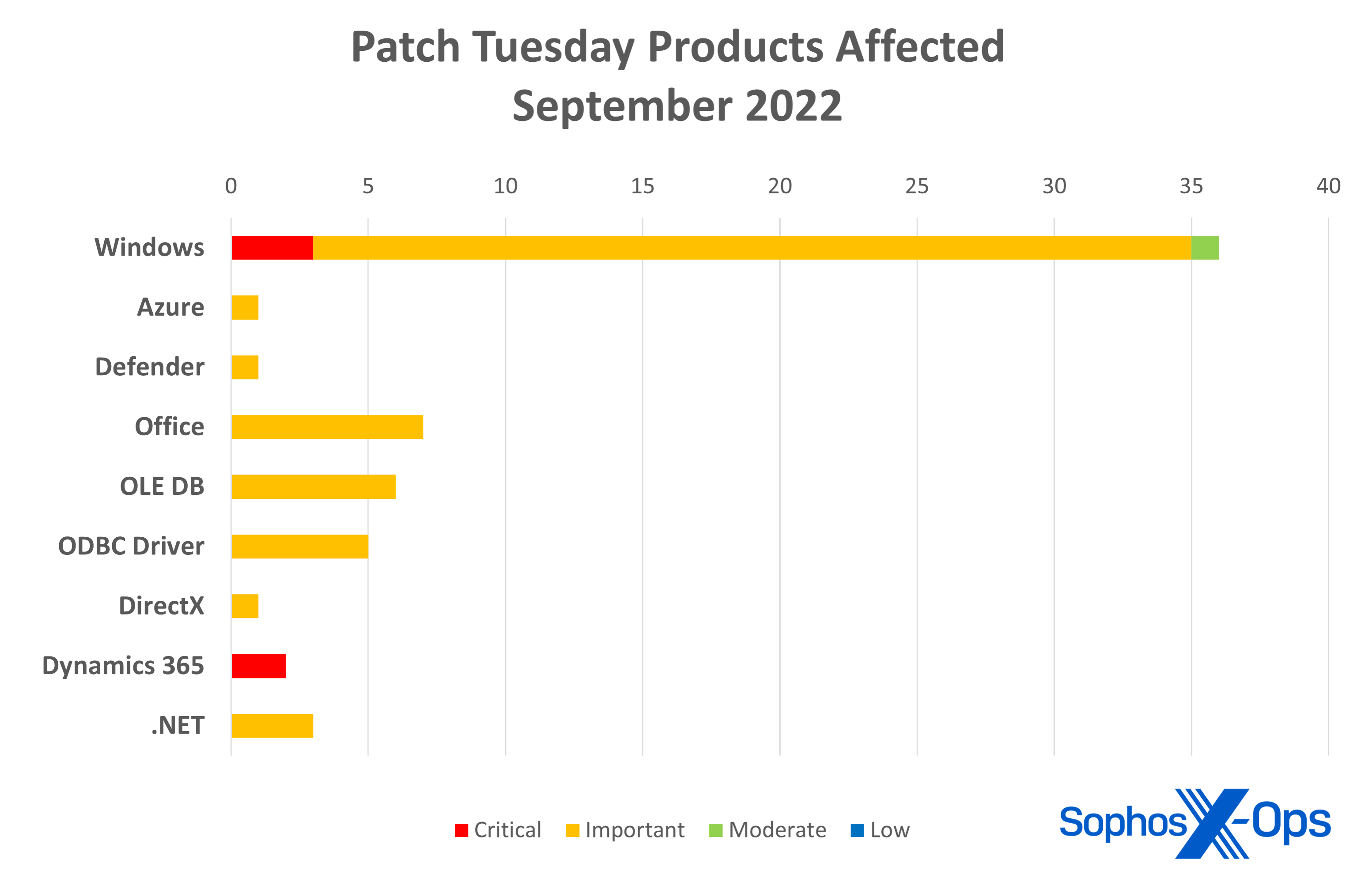
- Windows: 36
- Office: 7
- OLE DB: 6
- ODBC Driver: 5
- Azure: 1
- Dynamics 365: 2
- .NET: 3
- Defender: 1
- DirectX: 1
Figure 2: As with the previous 2 months, Windows makes up the bulk of vulnerabilities in September – but far fewer Azure bugs this time round
Notable vulnerabilities
Windows TCP/IP Remote Code Execution Vulnerability (CVE-2022-34718)
One of the five critical vulnerabilities in this month’s update, CVE-2022-34718 is an unauthenticated remote code execution vulnerability in Windows TCP/IP. The bug is described as being of low attack complexity, with exploitation involving sending a crafted IPv6 packet to a Windows node where IPSec is enabled. This vulnerability appears to affect multiple versions of Windows 7, 8.1, 10, 11, and Windows Server 2008, 2012, 2016, 2019, and 2022. Microsoft assesses exploitation is more likely for latest product releases, but less likely with older releases. Two other critical vulnerabilities in this month’s update (CVE-2022-34721 and CVE-2022-34722) also involve remote code execution as a result of sending a crafted IP packet to Windows nodes with IPSec enabled, although both these vulnerabilities are in the Windows Internet Key Exchange (IKE) protocol (IKEv1 only).
Remote code execution vulnerabilities in Office products
September’s Patch Tuesday also includes a host of Office remote code execution vulnerabilities, with several SharePoint bugs (all of which require authentication and appropriate permissions), one in PowerPoint (CVE-2022-37962) and two in Visio (CVE-2022-37963 and CVE-2022-38010). The latter three bugs are rated as Important, but with exploitation less likely. The attack vector for these is local, according to the CVSS metrics, as exploitation of the vulnerabilities themselves occurs locally. A remote attacker could send a crafted file to a victim, leading to a local attack on the victim’s machine – so some user interaction is required.
Windows Common Log File System Driver Elevation of Privilege Vulnerability (CVE-2022-37969)
This bug, which if successfully exploited would elevate an attacker’s privileges to SYSTEM, is in the Windows CLFS driver. Microsoft has detected exploitation against the latest product release, and says this bug has been publicly disclosed. with low attack complexity and no user interaction required. While the specific attack vector isn’t known, a previous privilege escalation vulnerability in CLFS (CVE-2021-31954) was due to a lack of proper validation of the length of user-supplied data, resulting in a buffer overflow. Another elevation of privilege bug in CLFS, CVE-2022-35803, appears in this month’s release, but has not been exploited.
Windows Kernel Elevation of Privilege Vulnerabilities (CVE-2022-37956 and CVE-2022-37957)
Finally, this month’s release includes two kernel privilege escalation vulnerabilities, CVE-2022-37956 and CVE-2022-37957. Microsoft assesses the latter as more likely to be exploited, but both have low attack complexity and do not require user interaction. Successful exploitation of either bug would result in an attacker gaining SYSTEM privileges.
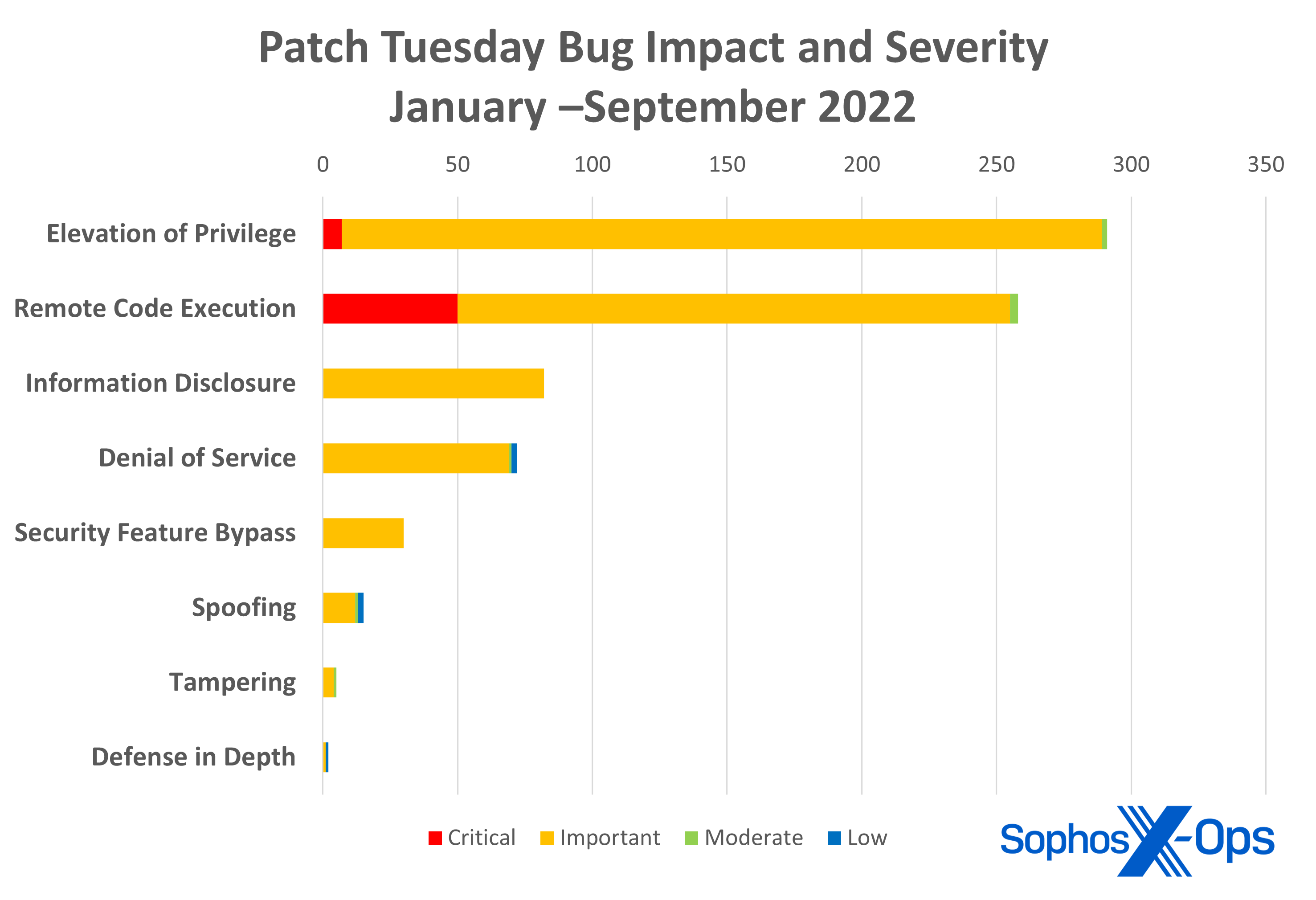
Figure 3: Elevation-of-privilege vulnerabilities are still in the lead as we head into the final quarter of 2022, although remote code execution bugs are catching up, with a higher percentage of critical ratings
As you can every month, if you don’t want to wait for your system to pull down the updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your particular system’s architecture and build number.