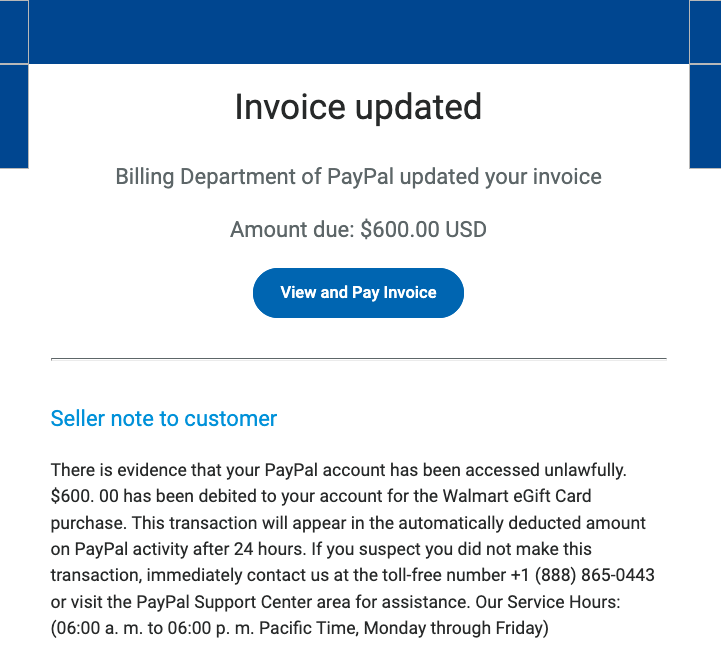
Business Email Compromise Attack Tactics
Credit to Author: Jon Clay| Date: Thu, 18 Aug 2022 00:00:00 +0000
Is BEC more damaging than ransomware? What tactics are BEC actors using? How can organizations bolster their defenses? Jon Clay, VP of threat intelligence, tackles these pertinent questions and more to help reduce cyber risk.
Read more