Zoom expands end-to-end encryption for Phone and breakout rooms
Credit to Author: Charlotte Trueman| Date: Fri, 22 Jul 2022 03:44:00 -0700
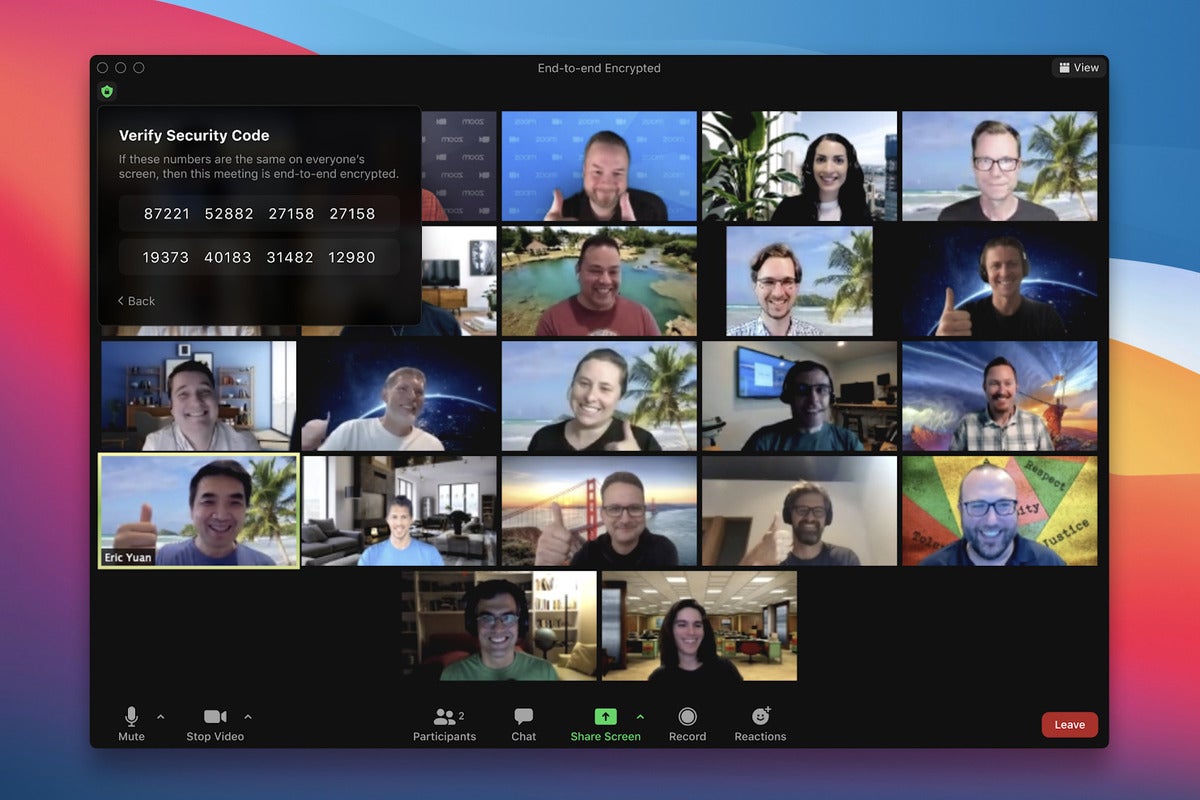
Zoom has announced it is expanding end-to-end encryption (E2EE) capabilities to Zoom Phone, with breakout rooms to be given the same level of encryption in the near future.
Zoom Phone customers now have the option to upgrade to E2EE during one-on-one Zoom Phone calls between users on the same Zoom account that occur via the Zoom client.
During a call, when users select “More” they will see an option to change the session to an end-to-end encrypted phone call. When enabled, Zoom encrypts the call by using cryptographic keys known only to the devices of the caller and receiver. Users will also have the option to verify E2EE status by providing a unique security code to one another.





