Living off another land: Ransomware borrows vulnerable driver to remove security software
Credit to Author: Andrew Brandt| Date: Thu, 06 Feb 2020 15:22:24 +0000
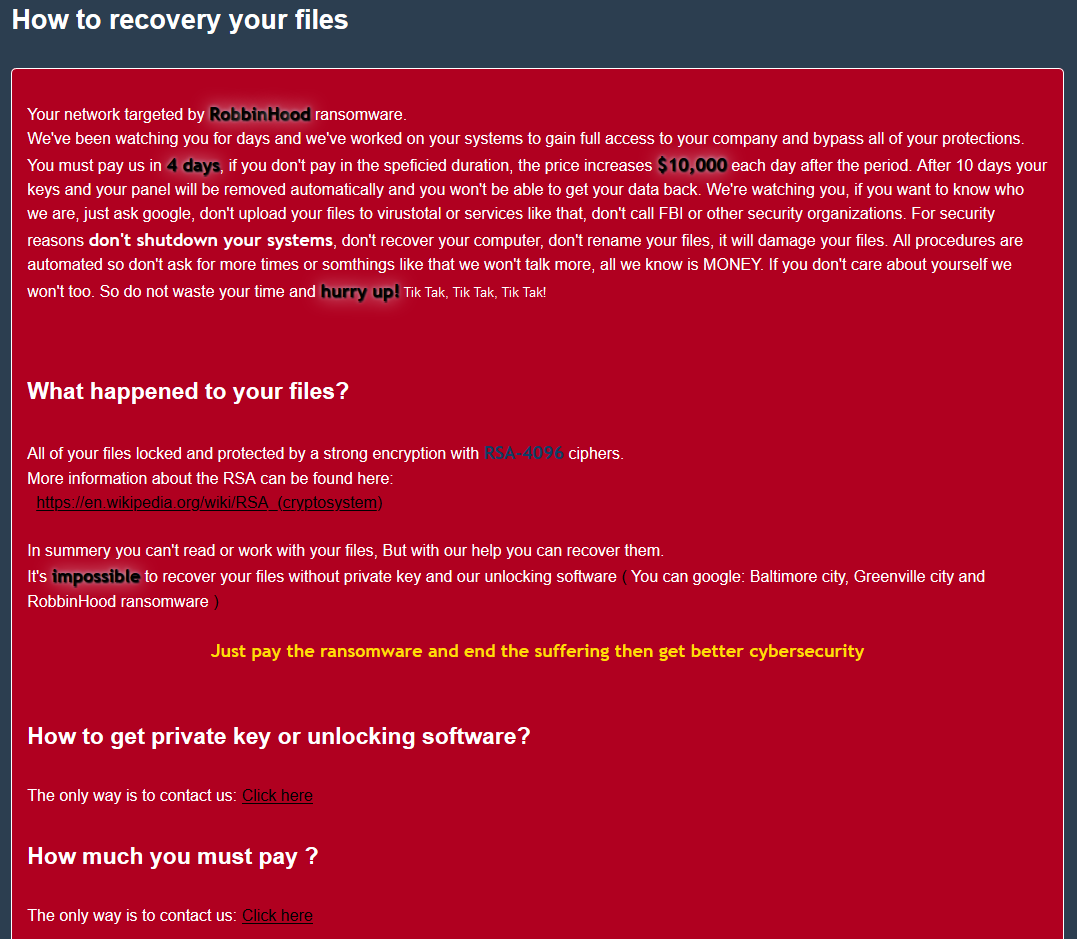
Sophos has been investigating two different ransomware attacks where the adversaries deployed a legitimate, digitally signed hardware driver in order to delete security products from the targeted computers just prior to performing the destructive file encryption portion of the attack. The signed driver, part of a now-deprecated software package published by Taiwan-based motherboard manufacturer Gigabyte, […]<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/uepwaOU8_Ek” height=”1″ width=”1″ alt=””/>
Read more