How to prevent data loss on your network

Use these tools and techniques to protect important data from being exfiltrated from your Windows network.

Use these tools and techniques to protect important data from being exfiltrated from your Windows network.
Credit to Author: Todd VanderArk| Date: Tue, 18 Feb 2020 17:00:31 +0000
The “Defending the power grid against supply chain attacks” blog series analyzes how supply chain attacks are conducted and the steps utilities, device manufacturers, and software providers can take to better secure critical infrastructure.
The post Defending the power grid against supply chain attacks—Part 1: The risk defined appeared first on Microsoft Security.
Read more
Credit to Author: BrianKrebs| Date: Tue, 18 Feb 2020 18:00:29 +0000
Crooks are constantly dreaming up new ways to use and conceal stolen credit card data. According to the U.S. Secret Service, the latest scheme involves stolen card information embedded in barcodes affixed to phony money network rewards cards. The scammers then pay for merchandise by instructing a cashier to scan the barcode and enter the expiration date and card security code.
Read more
Enforcement of the California Consumer Privacy Act begins this summer, but lawsuits are already being filed. To help you comply and avoid being sued, CSO contributor Maria Korolov joins IDG TECH(talk) host Juliet Beauchamp to discuss critical components of the CCPA and answer viewers’ questions.
Credit to Author: Malwarebytes Labs| Date: Tue, 18 Feb 2020 17:25:42 +0000
 | |
| With security, compliance, and customer engagement driving organizations to the cloud, it’s no wonder IDaaS has become the standard in identity management. Learn about the benefits and concerns of IDaaS for organizations of all sizes. Categories: Tags: hybrid environmentiamIDaaSidentity and access managementidentity-as-a-servicesinge sign-onsso |
The post Harnessing the power of identity management (IDaaS) in the cloud appeared first on Malwarebytes Labs.
Read moreCredit to Author: Malwarebytes Labs| Date: Tue, 18 Feb 2020 16:40:45 +0000
 | |
| A roundup of the previous week’s security news, including Malwarebytes’ release of the 2020 State of Malware Report, online dating woes, Emotet infection vectors, ransomware attacks, and more. Categories: Tags: accusoftCISOcoronavirusDellemotetEquifaxgigabytegridworkshelixHollywoodnude photosonline datingrobbinhoodstate of malware reportxHelper |
The post A week in security (February 10 – 16) appeared first on Malwarebytes Labs.
Read more
Credit to Author: Steven J. Vaughan-Nichols| Date: Tue, 18 Feb 2020 07:00:00 -0800
Why am I still writing about Windows 7? It’s dead, Jim! The tombstone reads, “June 22, 2009 – January 14, 2020.” It was a good run, but unless you’re shelling out some serious coin for Windows 7 Extended Security Updates (ESU), you shouldn’t be running Windows 7.
But many of you are. According to the best survey of who’s running what, the U.S. government’s Digital Analytics Program (DAP), on Feb. 14, weeks after Win7’s end of life, just over one in 20 of Windows users was still using Windows 7! Oh, come on! More than 5%! A dead and buried OS! Get with the program!
Credit to Author: Chris McCormack| Date: Tue, 18 Feb 2020 14:00:18 +0000
Introducing the all-new Xstream Architecture<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/wTiPAHQ-dzk” height=”1″ width=”1″ alt=””/>
Read more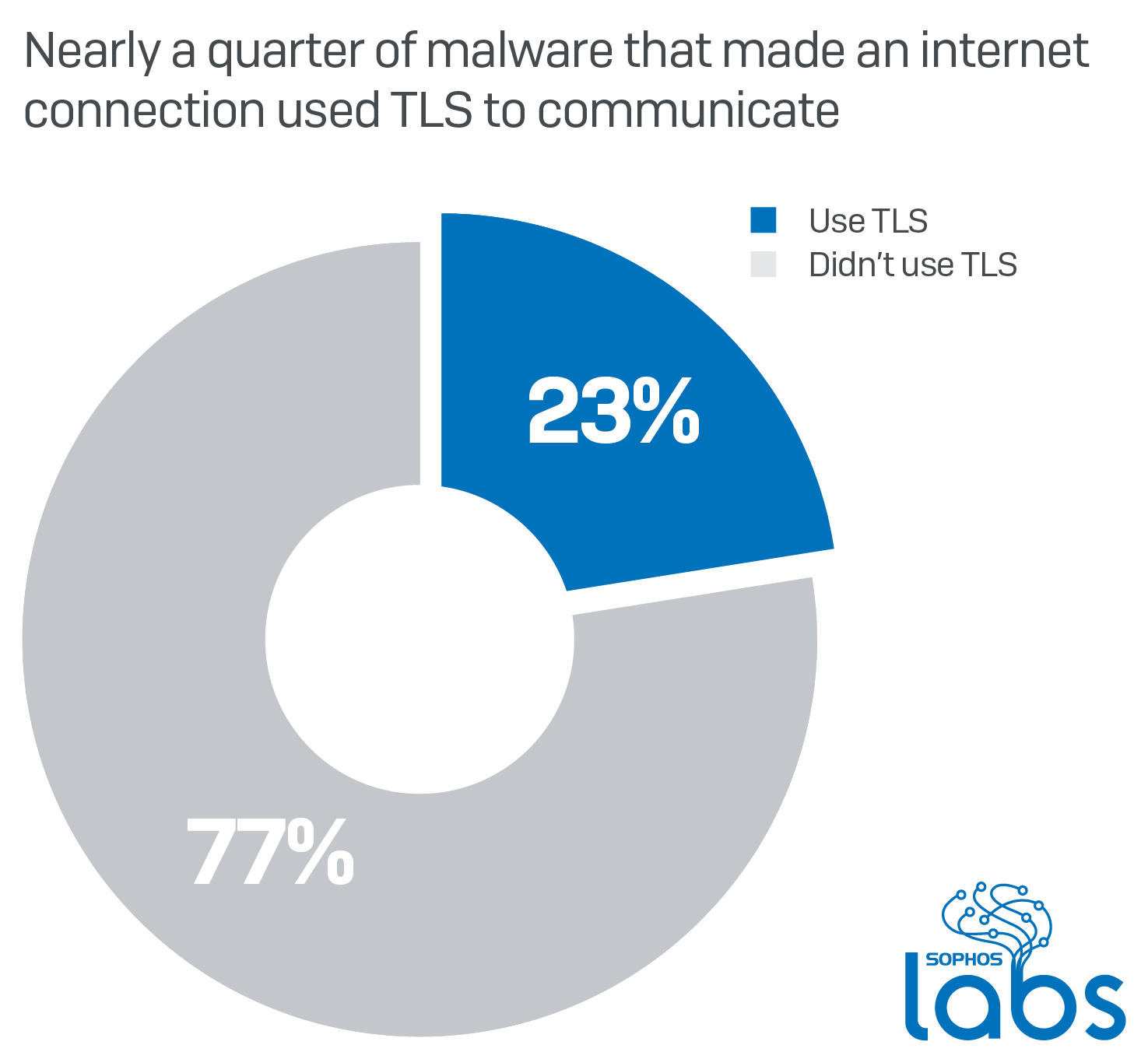
Credit to Author: Luca Nagy| Date: Tue, 18 Feb 2020 13:30:07 +0000
Encryption is one of the strongest weapons malware authors can leverage: They can use it to obfuscate their code, to prevent users (in the case of ransomware) from being able to access their files, and for securing their malicious network communication. As websites and apps more widely adopt TLS (Transport Layer Security) and communicate over […]<img src=”http://feeds.feedburner.com/~r/sophos/dgdY/~4/XXvUtjG7XVU” height=”1″ width=”1″ alt=””/>
Read more
Credit to Author: Andy Greenberg| Date: Tue, 18 Feb 2020 11:00:00 +0000
The lax security of supply chain firmware has been a known concern for years—with precious little progress being made.
Read more