February, 2020 Patch Tuesday brings a century of updates to Microsoft, Adobe products
Credit to Author: SophosLabs Offensive Security| Date: Tue, 11 Feb 2020 20:50:22 +0000
For this second Patch Tuesday of 2020, Microsoft has released a hundred patches to Windows and other Microsoft software, including 12 vulnerabilities flagged as Critical, and 87 flagged as Important. In addition, Adobe also published updates for its Flash Player, Acrobat, Framemaker, Experience Manager, and Digital Editions products in notifications timed to coincide with Microsoft’s publication.
Microsoft’s Security Update Guide. will update itself as more information becomes available but the page list no fewer than 26 CVE records that address various vulnerabilities in Microsoft products. If that seems like a lot, Adobe’s list (published on their Security Bulletins and Updates page) lists 17 CVEs just for the Acrobat product lines, 12 of which are rated a critical fix. Any way you cut it, February may be a short month but it’s one of the largest for updates we’ve seen.
 As always, you can manually download the update rollup specific to your supported Windows system from the Microsoft Update Catalog website.
As always, you can manually download the update rollup specific to your supported Windows system from the Microsoft Update Catalog website.
On Windows, the most critical components requiring attention are:
- Windows Kernel
- Windows Remote Desktop Protocol (RDP)
- Scripting Engine
- Windows Media Foundation
- Windows Backup Service
Some particular attention should be drawn to CVE-2020-0674 (Scripting Engine Memory Corruption Vulnerability) as its exploitation has been detected in the wild.
Additionally, the February Patch Tuesday addresses many critical vulnerabilities, which have not (yet) been spotted as actively exploited, but may be in a near future, including:
CVE-2020-0662: Windows Remote Code Execution Vulnerability
CVE-2020-0681: Remote Desktop Client Remote Code Execution Vulnerability
CVE-2020-0734: Remote Desktop Client Remote Code Execution Vulnerability
CVE-2020-0729: LNK Remote Code Execution Vulnerability
CVE-2020-0738: Media Foundation Memory Corruption Vulnerability
CVE-2020-0673: Scripting Engine Memory Corruption Vulnerability
CVE-2020-0710: Scripting Engine Memory Corruption Vulnerability
CVE-2020-0711: Scripting Engine Memory Corruption Vulnerability
CVE-2020-0712: Scripting Engine Memory Corruption Vulnerability
CVE-2020-0713: Scripting Engine Memory Corruption Vulnerability
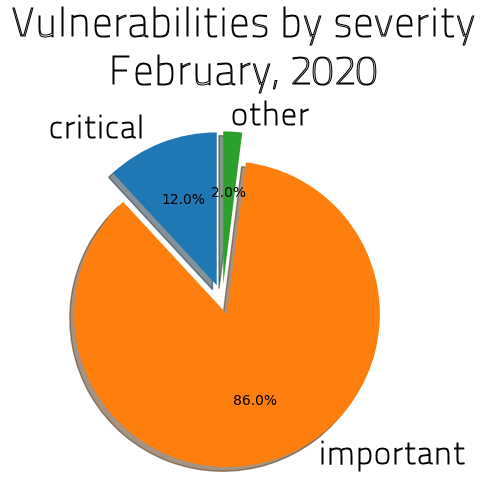
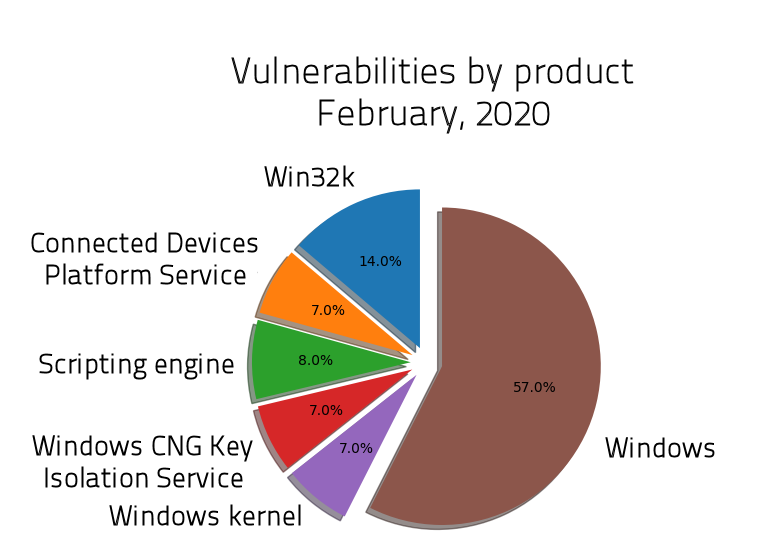
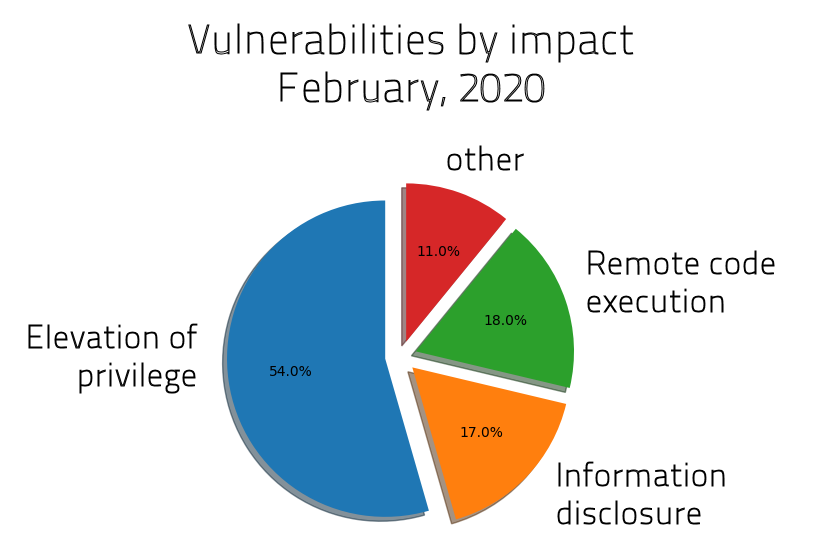
SophosLabs has broken down the content of the February 2020 edition of Patch Tuesday as follows:
LNK vulnerability
CVE-2020-0729
One of the most interesting vulnerabilities of this month is CVE-2020-0729: LNK Remote Code Execution Vulnerability. The LNK file type is a [publicly documented] binary format. Unlike Linux which uses Symbolic Links to create shortcuts, Windows relies on this LNK format (although Windows also supports and uses Symbolic Links, via NTFS). As a binary format, it requires the operating system to parse the contents, which can introduce vulnerabilities, as has happened in the past (CVE-2017-8464 or CVE-2015-0096). Little information was communicated from Microsoft, except that a succesful exploitation of this new vulnerability (CVE-2020-0729) would lead to a code execution, possibly remotely. That is probably why Microsoft decided to classify this vulnerability as “Critical.”
Scripting Engine
CVE-2019-1451, CVE-2020-0673, CVE-2020-0674, CVE-2020-0710,
CVE-2020-0711, CVE-2020-0712, CVE-2020-0713
Several Remote Code Execution (RCE) vulnerabilities were discovered and patched this month. Even though those vulnerabilities would not immediately be linked to a full system compromise, their successful exploitation would give an attacker a foothold onto a targeted computer, with associated privileges, allowing further horizontal or vertical escalation.
CVE-2020-0674 is the one other vulnerability that stands out this month, mostly because it has been found exploited in the wild, so its exploitation is not merely theoretical. Therefore SophosLabs urges to apply immediately the available patches to avoid being compromised by any of those vulnerabilities.
RDP service and client
CVE-2020-0655,CVE-2020-0660,CVE-2020-0681, CVE-2020-0734
This month again, RDP happens to be a target of choice, where 4 vulnerabilities were fixed in several components:
– Remote Desktop Service: CVE-2020-0655
– Remote Desktop Client: CVE-2020-0681, CVE-2020-0734
Interestingly some vulnerabilities in the RDP components are related to a incorrect packet parsing when a connection is performed via UDP (CVE-2020-0681), as it was the case last month for CVE-2020-0609 and CVE-2020-0610, which also stemmed from an incorrectly validation of UDP packets.
Aside of the RCE bugs mentioned above, a DoS issue was also patched (CVE-2020-0660).
Windows Kernel Win32k component
CVE-2020-0691, CVE-2020-0716, CVE-2020-0717, CVE-2020-0719,
CVE-2020-0720, CVE-2020-0721, CVE-2020-0722, CVE-2020-0723,
CVE-2020-0724, CVE-2020-0725, CVE-2020-0726, CVE-2020-0731,
CVE-2020-0714, CVE-2020-0709, CVE-2020-0792
Several memory corruption vulnerabilities have been discovered and patched by Microsoft, in Win32k and DirectX kernel components. Although those vulnerabilities vary by their nature (Use after Free, buffer overflow), their successful exploitation would allow an attacker to locally elevate their privilege; or in the case of a remote scenario (and coupled with (at least) a browser exploit) such vulnerabilities could be triggered remote and allow a browser sandbox escape, giving full control to the attacker and so entirely remotely.
How is Sophos responding to these threats?
Here is a list of protection released by SophosLabs in response to this advisory to complement any existing protection and generic exploit mitigation capabilities in our products.
Additional IPS Signatures
CVE | SID |
| CVE-2020-0658 | 2301474 |
How long does it take to have Sophos detection in place?
We aim to add detection to critical issues based on the type and nature of the vulnerabilities as soon as possible. In many cases, existing detections will catch exploit attempts without the need for updates.
What if the vulnerability/0-day you’re looking for is not listed here?
If we haven’t released an update for a specific exploit, the most likely reason is that we did not receive the data that shows how the exploit works in the real world. As many of this month’s exploits were crafted in a lab and have not been seen in the wild, nobody has enough information (yet) about how criminals would, hypothetically, exploit any given vulnerability. If or when we receive information about real attacks, we will create new detections, as needed.