MyKings botnet spreads headaches, cryptominers, and Forshare malware
Credit to Author: Gabor Szappanos| Date: Wed, 18 Dec 2019 14:16:38 +0000
There’s a pretty good chance everyone who reads this story will have had some degree of interaction with a botnet we call MyKings (and others call DarkCloud or Smominru), whether you know it or not. For the past couple of years, this botnet has been a persistent source of nuisance-grade opportunistic attacks against the underpatched, low-hanging fruit of the internet. It’s probably knocking at your firewall right now. They certainly wouldn’t be the first.
This botnet is a relentlessly redundant attacker, targeting primarily Windows-based servers hosting any of a variety of services: MySQL, MS-SQL, Telnet, ssh, IPC, WMI, Remote Desktop (RDP), and even the servers that run CCTV camera storage.
While much has been said about individual components of the botnet, in a report on MyKings SophosLabs is releasing today, principal malware researcher Gabor Szappanos writes that his goal is “to provide a full picture of the operation of the botnet” looking at all its tools and behaviors, globally.
Attacks by the MyKings botnet operators follow a predictable pattern: The botnet attempts a stable of different attacks against a server. Unpatched, or underpatched, Windows servers may be vulnerable to a wide range of attacks, the goal of which is to deliver a malware executable, more often than not, a Trojan named Forshare.
The infected endpoints we observed totaled about 43900 unique IP addresses. This number includes only those endpoints that have a public IP address; internal addresses were not counted (we found 10973 more using internal NAT ranges) but then we would have less confidence that we were counting unique computers.
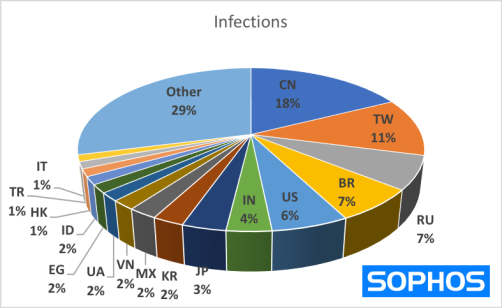 The countries with the highest population of infected hosts include:
The countries with the highest population of infected hosts include:
- China
- Taiwan
- Russia
- Brazil
- USA
- India
- Japan
The botnet attacks like it’s playing in a CTF competition: It establishes a beachhead, then clears out any trace of the competition, removing indicators of competing malware families, then securing the door it used to break in behind itself.
 This kill list is how MyKings looks for and attempts to terminate the processes or services of a variety of endpoint security tools.
This kill list is how MyKings looks for and attempts to terminate the processes or services of a variety of endpoint security tools.
 Redundant is also part of the MyKings pattern, and plays a key part in its persistence mechanism. There are several component parts to MyKings, and each of them does a very similar self-update procedure. Everything repeats itself several times over, using a variety of command combinations.
Redundant is also part of the MyKings pattern, and plays a key part in its persistence mechanism. There are several component parts to MyKings, and each of them does a very similar self-update procedure. Everything repeats itself several times over, using a variety of command combinations.
Even if most of the components of the botnet are removed from the computer, the remaining ones have the capability to restore it to full strength simply by updating themselves. All of this is orchestrated using self-extracting RAR archives and Windows batch files. One of the downloaded components is a WinRAR self-extracting archive that creates two files, n.vbs and c3.bat. This batch file is the cornerstone of Mykings operations: A lot of activities are concentrated into this single component.

The MyKings network attacks go through constant refinement, so they change over time. The criminals behind this botnet prefer to use open source or other public domain software and have enough skills to customize and enhance existing source code. For instance, the botnet has begun to experiment with hiding malware payloads in plain sight, storing the file in an image using a process called steganography.
 In this sample image, a Windows malware executable (identifiable by its characteristic MZ header bytes and text) appears within the image data in a modified .jpg photo of Taylor Swift. MyKings’ operators uploaded this innocuous-looking image file to a public repository, and then used it to deliver an update to the botnet.
In this sample image, a Windows malware executable (identifiable by its characteristic MZ header bytes and text) appears within the image data in a modified .jpg photo of Taylor Swift. MyKings’ operators uploaded this innocuous-looking image file to a public repository, and then used it to deliver an update to the botnet.
MyKings also redundantly employs a number of methods of establishing persistence on the infected host: It uses a bootkit, which launches the botnet immediately upon reboot; sets Registry run keys; and creates a number of Scheduled Tasks and WMI listeners.
MyKings is not content to remain on your internet-facing server for long. The malware leverages the EternalBlue exploit and other exploits leaked by the Shadow Brokers. We know that because the first version of the MyKings package used a compressed archive that named them all. We found two very different EternalBlue implementations used in MyKings campaigns.
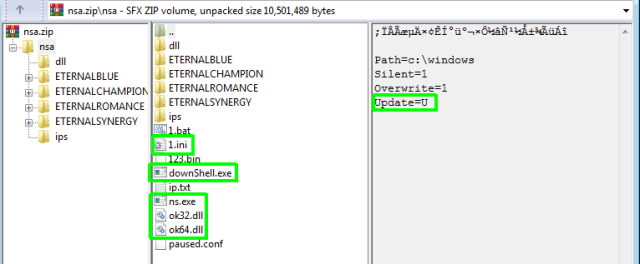
The earlier version, found in August 2018, was completely based on the files leaked by the Shadow Brokers, along with the MyKings additions. It was literally named nsa.zip.
It is a self-extracting ZIP file with a couple of custom components inserted. The comment is turned out to be in Chinese, and it is the same as in the .bat file: “The following comments contain self-extracting script commands”The botnet is medium sized, has about 45,000 infected hosts.
What’s it all for?
Unbelievably, all this effort was made in order to deliver one of various different Monero cryptominers. Forshare gets used to ensure the miners are running.
The criminals who run the botnet have reportedly earned about 9,000 XMR over its lifetime, estimated to be valued at about $3 million. The current MyKings income is about $300 per day, mainly due to a lower Monero exchange rate.
For more on the botnet and how it operates, please read MyKings: The slow but steady growth of a relentless botnet.
IoCs
All IoCs relating to this publication can be found on the SophosLabs Github.