Is encryption rendering your firewall irrelevant?
Credit to Author: Chris McCormack| Date: Fri, 22 Nov 2019 12:09:36 +0000
Transport Layer Security (TLS) is the encryption standard used on the internet today – the terms SSL and TLS are often used interchangeably but Secure Sockets Layer (SSL) is an old standard that has been eclipsed by TLS. So, although the more common term is still SSL, just know that most people mean TLS when they say SSL.
Encryption provides privacy not security
TLS is designed to provide confidentiality and authenticity by encrypting the communication between two parties and verifying the server is who it claims to be, based on its certificate and who issued it.
TLS encryption does NOT provide any security or assurance of the content. So when someone says their connection to the server is secure, they really only mean it’s secure from eavesdropping and that the identity of the server is confirmed.
You can have a perfectly valid encrypted and ‘secure’ connection to a site hosting malicious payloads… which is why inspection of this encrypted traffic is so important.
TLS inspection is not easy
The problem is that TLS is a very complex protocol with different certificates having to be exchanged, as well as negotiation over cipher suites to be used to determine how the connection should be encrypted.
There are also, of course, several TLS versions, and many applications and web services do things differently. Despite having rigorous standards, this makes it very possible for things to be incompatible.
This presents enormous challenges for any security solution that attempts to inject itself into this process for the purpose of inspecting and securing the content that is exchanged.
On top of all the technical complexity, there are policy decisions that need to be made. Not all SSL traffic can or should be treated the same. It’s a balancing act: You have to balance privacy, performance, security and compliance. Some traffic, like banking and finance, should not be inspected and some traffic cannot be inspected.
Encrypted traffic volume is approaching 100%
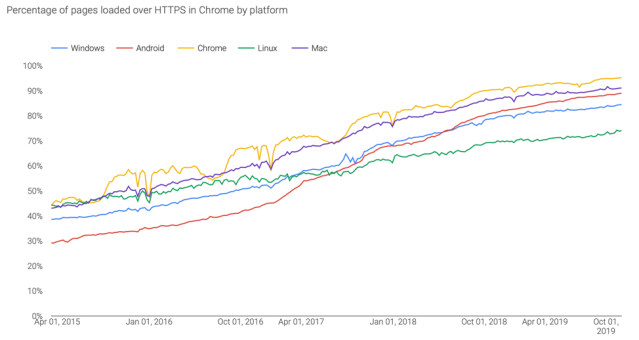
For many good reasons, most internet connections are now fully encrypted. In fact, on most platforms over 80% of web sessions are now encrypted according to the Google Transparency Report.
Has encryption rendered your firewall irrelevant?
Encryption is great for privacy, yes. But, it is also creating an enormous blind spot for most organizations, where their current firewalls are not up to the task of inspecting great volumes of encrypted traffic.
In effect, TLS encryption has rendered most firewalls irrelevant and useless as they no longer have insight into the majority of traffic passing through the network.
The real danger is the threats hiding in encrypted traffic
With the explosive growth in TLS encryption in recent years, it’s probably no surprise that hackers are catching onto this trend and leveraging it to help get malware on your network undetected and keep it there.
In fact, according to SophosLabs, about 1/3rd of malware and unwanted applications are using TLS, to stealthily get on your network and communicate once there, all in the interest of remaining undetected.
Why most organizations are powerless to do something
As I outlined earlier, TLS is complex and resource intensive.
It’s extremely expensive to invest in the R&D necessary to properly inspect TLS encrypted traffic at the firewall, in an efficient and effective way. As a result, most firewall products simply aren’t up to the task of inspecting the current volume of encrypted traffic passing through them.
Most network admins have been forced to accept the risk of threats and non-compliance due to serious performance limitations. Enabling TLS inspection is just too costly in terms of the performance impact.
On top of that, poor inspection implementations that don’t support the latest standards result in downgraded security, which opens up vulnerabilities, or simply break a lot of websites, resulting in a terrible user experience.
This situation is creating conditions for a perfect storm.
There has to be a better way
And, there is!
Over the last few years, we’ve been investing heavily in solving the problem with TLS inspection. The result of all that effort is the new Xstream Architecture in XG Firewall v18.
It offers a new ground-up solution to eliminating that vast blind spot, without all the performance and user experience compromises that have plagued other solutions.
It delivers:
- High performance – a light weight engine with high connection capacity
- Top security – supporting TLS 1.3 and all modern cipher suites
- Inspection of all traffic – being application & port agnostic
- A great user experience – with extensive interoperability to avoid breaking the internet
- Powerful policy – offering the perfect balance of performance, privacy and protection
- Unmatched visibility – into your encrypted traffic flows and any errors
There’s no longer a need to run blind. Return your firewall to relevance and start inspecting the traffic flowing through it.
You can try the new Xstream SSL Inspection in XG Firewall v18 as part of the early access program. Get started today! All our licensed XG Firewall customers get this great new capability at no charge.
Watch this video to learn more about how it works: