The Complete Guide to Two-Factor Authentication (2FA)
Credit to Author: Elliot Hill| Date: Tue, 29 Oct 2019 10:35:53 +0000
Two-factor authentication, more commonly known as ‘2FA’, is one of the easiest and most secure methods of protecting sensitive online accounts from being accessed by would-be fraudsters. A simple way of protecting accounts, many top-ranking websites, and service providers now offer 2FA log-in protection for their customers.
However, there are still relatively few people using 2FA, choosing instead not to enable 2FA protection despite its availability. One online research firm found that a shockingly low 28% of users are regularly using 2FA to access sensitive accounts, with only 54% of these using it voluntarily, rather than it being enforced by their service providers.
But two-factor authentication isn’t a new process, and although some users may see it as an extra hoop to jump through, 2FA is one of the most critical steps to ensuring basic security of online accounts.
For cryptocurrency users, holders of digital assets, and those regular transacting via online exchanges, keeping your information secure is a top priority. Using 2FA services is an important first step in that security process. Here, we’re going to guide you through what 2FA is, which applications are best, 2FA’s limitations, and where you should look to increase your security.
What is 2FA?
Authenticating logins or identities through 2FA originates from a concept called ‘Multi-factor authentication’, or MFA. Multi-factor authentication is based on a user having specific knowledge of something personal to them, for example, a PIN or a pet’s name; possession of something, for example, their smartphone or bank card; or something they have which is individual to them, like a fingerprint.
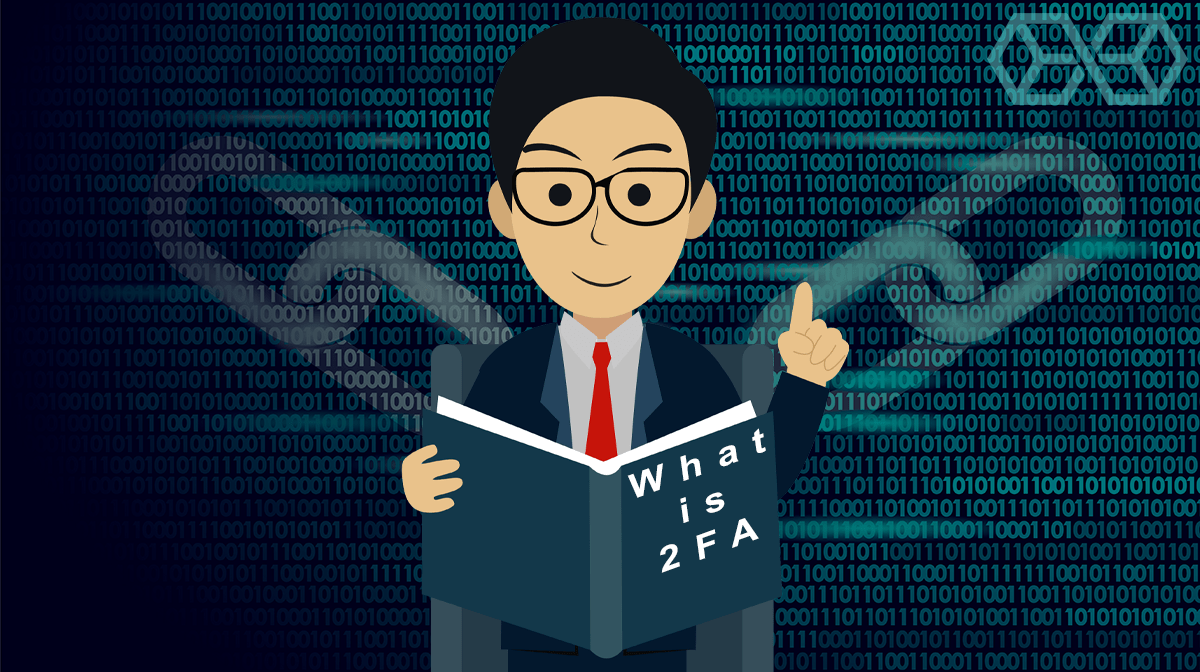
As the name suggests, 2FA only requires two of these factors to authenticate an individual. This is perfectly adequate for the security of most normal user accounts and takes significantly less time than verifying through three or more steps. This is one of the main reasons that 2FA has become the most popular form of verification.
While we are going to talk about 2FA for online verification and authentication software here, chances are you’ve already used 2FA in your daily life. For traditional banking providers, chip and PIN is one of the most basic forms of a two-step verification process, requiring a user to present a bank card, which is something they ‘have’, alongside a PIN, which is something they ‘know’.
When transacting online, such as entering login details into a website, you might not have a PIN or a physical card. So how does the website know you are who you claim to be, and not a hacker attempting to gain access to your account? This is where modern 2FA methods and applications are used. Let’s explore how these systems work.
How Does 2FA Work?
We’ve explored the theory behind 2FA, now let’s examine how it works in practice. Most authenticator apps work through what is known as a ‘Time-Based One-Time Password’, or ‘TOTP’. This is a kind of ‘software-token’, and it’s the type of 2FA we are going to be discussing for the majority of this article.
Just so you know the difference, a 2FA ‘hardware-token’ is a generated code on a physical and dedicated piece of hardware, like a key-fob with a small LCD screen. These units are not commonly used now, because they are expensive and easy to lose – or easily stolen. Instead, let’s see how a software-token based 2FA system works with a real-world example.
When you create an exchange account, let’s use Binance here, you have the option to turn on 2FA and use an authenticator app to verify your logins. Say we are using Google Authenticator with our Binance account. Binance would generate a secret key, which you could then scan using a QR code through your mobile device. You could also do this with many other authenticator apps as the generated key is part of a TOTP standardized code.
Now, these two accounts are linked, and no one but your authenticator app and the service provider can see the generated codes. The authenticator app will combine your individual secret key with an access code, using a secure hash function. Similar to how hash functions work in a blockchain capacity, the authenticator will use a cryptographic hash to authenticate the request from the exchange and generate a unique six-digit code to access your account.
In this example, when you next try to log on to Binance, the exchange will prompt you for your 2FA code. At this point, you would have your phone ready and your authenticator app open, and you would look for the 6-digit code marked ‘Binance’.
Simply type this code in, and the service provider will authorize your login. It’s simple and quick in practice, although there are a few things to remember. Firstly, as this is a one-time passcode, it will usually expire and generate a new code every 30 seconds.
Secondly, if you lose your phone or the authenticator app, you’ll no longer be able to access your linked accounts. That’s why it’s highly important that when you first link your authenticator to a new account, you keep a secure record of the 16-digit recovery key, which is generated on setup. This allows you to quickly restore accounts, rather than waiting for your identity to be manually verified by the service provider.
Best 2FA Authenticator Applications
While some sites generate a simple form of 2FA for their users, such as sending a code via email or SMS message, others enlist the help of more advanced solutions. In these cases, websites or service providers will use standard code to generate a TOTP number, which can be revealed using a dedicated authenticator app.
These authenticator applications generally use encryption techniques to keep user data safe, they may require a PIN or biometric data to access, and they can usually be accessed via mobile apps. Let’s review the best authenticator apps below.
Authy
Authy was founded in 2011 by security experts Daniel Palacio and Gleb Chuvpilo. Since its establishment, it has grown into one of the most widely used authenticators on the market, serving customers on services such as Uber, LinkedIn, and Gmail.

Available for free download on Android and iOS, Authy is one of the leading providers of 2FA solutions. As the top-rated authentication app, Authy can be synced across multiple devices. Many users rely on Authy because it’s one of the only authentication apps which is dedicated to 2FA, whereas other offerings like Microsoft and Google’s authenticators are made first and foremost to access their own services.
Unlike Google Authenticator, Authy can also be used with Windows desktop, and Apple watches. However, if a user doesn’t trust storing software-tokens across multiple devices, they can disable this feature at will.
Another great feature Authy offers its users is encrypted backups in the cloud. This means that if you lose your mobile device, as long as you have multi-device functionality enabled, you can simply access your accounts from another linked device. Other apps don’t offer this, so if you lose your mobile, you have to reset all of your authentication codes.
Authy is completely free for end-users to download and use. Instead of charging users, Authy monetizes their service by working with service providers and businesses who purchase software solutions through their parent company, Twilio. As a result, it’s likely Authy will always remain a free service.
Microsoft Authenticator
The official authenticator from computing giant Microsoft is available on both Android and iOS and allows multiple accounts to be added to the app. As you can see in the screenshot, the Microsoft Authenticator generates 6-digit codes valid for 30 seconds.
Like other authenticators, Microsoft’s app uses the TOTP industry standard for generating auth codes. This means that any account which uses this same standard can be added to the Microsoft Authenticator app, regardless of whether it’s in the Microsoft software family or not. However, Microsoft’s authenticator is mobile-only.
Microsoft’s Authenticator is a simple and functional piece of software, but despite this, it hasn’t enjoyed the same degree of use as other authentication applications.
Google Authenticator
The Google Authenticator software is one of the most frequently used and easiest applications to perform 2FA with. Like other apps, Google’s Authenticator uses a TOTP standard password algorithm to generate passcodes.
To support the Google Authenticator app, service providers must generate a highly secure 80-bit secret key for each individual user, which allows the app to generate an HMAC-SHA1 cryptographic message or code.
Originally released on an open-source license, Google Authenticator is now proprietary software, which may indicate how big Google sees the 2FA market becoming in years to come. However, despite being proprietary, the Google Authenticator app is currently completely free to download and use.
The Google Authenticator is currently only available on mobile devices, and unlike Authy, it can’t be used on desktops. Despite this, it can be installed on both Android and iOS devices, including tablets and iPads.
Which Sites Are Already Using 2FA?
There are thousands of sites that support 2FA. These include major social media websites, such as Facebook, Twitter, LinkedIn, and Instagram, to retailers like eBay, Etsy, and Shopify. In recent times, the number of websites supporting software-token based 2FA is growing rapidly.

Despite this, there are still some major websites which don’t yet support software-token 2FA. Chinese retail giant, AliExpress, does not support 2FA on their site, despite being linked to payment methods and holding personal address details. Similarly, leading U.S. streaming service Netflix doesn’t support 2FA login, and surprisingly nor does music streaming service Spotify.
So, we could ask, does every website or every user need to enable 2FA? If you’re only accessing sites where security isn’t a top concern, you may not want the extra login step of authenticating through 2FA. Instead, there are other ways of easily authenticating a login such as biometric fingerprint scans or facial recognition. That said, it’s still highly recommended that you have 2FA enabled on all your accounts!
Email & SMS Authentication VS. Authentication Apps
You might be thinking, why go to the trouble of downloading a dedicated app for 2FA, when companies can simply send a code through to an associated email account or via SMS? It’s a great question, as SMS and email-based authentication methods are still safer than having no two-step authentication at all.
But when it comes to protecting your accounts, SMS and email are nowhere near as secure as dedicated authenticators. Here are some of the ways hackers could bypass a simple SMS or email authentication method.
- Sim Swapping – Sim swapping is becoming increasingly problematic. Essentially, sim swapping is when criminals contact your mobile network carrier and request that your number is transferred to a new sim card. While you might question why a carrier would allow this, it’s common practice if a user has lost their phone and wants to retain their original telephone number. Naturally, once a fraudster has your phone number, every SMS meant for you will make its way to them. If SMS-based 2FA is the only protection on your account, and this hacker already has your username and password, they now have full access to your account. If this is an exchange account, such as Bitmex, they could withdraw all of your funds. This is a major reason why most exchange accounts will caution against using SMS based authentication methods.
- Email Pwnage – The popular site ‘Have I Been Pwned?’ is a huge database of all the largest data breaches to happen worldwide. Unless you’re an incredibly meticulous user, you’ll probably find that at some point, your data has been breached. Data breaches happen when sites you’ve signed up for using your email address are compromised, and user data is stolen. In the worst-case scenarios, this can include payment and identity information, but hackers often steal usernames, emails, and passwords. If you’re like the majority of users, you likely reuse the exact same password or a similar password for multiple sites. This is a hacker’s dream – because if they know your email and password from one breach, they could use it to access your email. We’ve explored why you need a secure password manager here; but for the purposes of email-based 2FA, it’s best to assume your account could be compromised.
Instead, as we’ve examined, authenticators provide encrypted security on a separate device. If a hacker wanted to gain access to your exchange account, which was protected by Google 2FA for example, they would have to physically have your mobile device, or be a fairly experienced hacker.
If your 2FA authenticator app is also protected by a biometric marker, like a fingerprint, it’s going to be even harder for a hacker to gain access. Nevertheless, 2FA isn’t bulletproof. Here are some instances where 2FA has been breached.
Where Has 2FA Failed?
No technology is infallible, and 2FA is no exception. There have been instances where 2FA has failed to protect user accounts – but this doesn’t mean you shouldn’t use it. Let’s look at some cases where 2FA has been proven to be vulnerable, and why.
The first and foremost vulnerability is a straightforward phishing attack. The FBI has recently warned users that hackers could be using a ‘man-in-the-middle’ type phishing attack to lure users into entering their login details and their passcodes into a fake website.

Such sites, which may be linked through a completely genuine-looking email, relay this information to the real site and then allow the hackers access to your account. This is an attack-type that makes use of social engineering. Although it may seem simple, social engineering is one of the most effective forms of phishing for user data and hacking accounts.
Essentially, social engineering relies on the fact that the average user won’t notice that they are being redirected to a fake website, which may have an imperceptibly different URL, for example, ‘gmaiI (dot) com’, where the ‘L’ is, in fact, a capital ‘i’. These types of attacks are common, and for the average user, they are incredibly difficult to detect.
The digital security company, Knowbe4, warns that often hackers are only after user’s session tokens. This is a unique cookie that is generated for each session a user starts on a website, for example, LinkedIn or Facebook. Hackers can then steal the session token and use it to hijack a user’s legitimate session – accessing all their private data.
Knowbe4 also warn that more advanced hackers can create a duplicate code generator. In this instance, an attacker could learn the seed number and algorithm used to generate the authentication code and use them to generate a code identical to the victims. If the attacker already knows your username or password, they could use this method to complete 2FA authentication.
These might seem worrying, but unless you’re a fairly high-profile target, hackers aren’t likely to use these costly and time-consuming methods to compromise your accounts. Similarly, in instances where 2FA hasn’t been used at all, hackers can get access to user accounts much faster, and with disastrous effects – let’s examine some of the most high-profile hacks where 2FA could have helped.
Hacks That 2FA Could Have Prevented
Throughout the end of 2016 and into early 2017, American consumer credit reporting agency Equifax experienced a data breach which led to huge numbers of fraudulent tax claims. In the breach, hackers accessed the simple 4-digit PIN code, which was issued to employees of the platform to access their records.

After lifting this info and successfully answering personal questions, the criminals went after-tax data, stolen from a ‘payroll-related service’. This data was then used to lodge fraudulent tax-return claims in employees’ names to steal tax refunds.
Had Equifax had 2FA in place for these employees, instead of a simple PIN code, then it’s highly unlikely the hackers wouldn’t have been so successful. Similarly, this also shows how our personal info, like security questions, isn’t as secure or secret as we think.
A similar scenario took place with several popular sites and affected Citrix’s GoToMyPC in 2016. Many sites suffered large scale breaches in which users had their usernames and passwords stolen. Although these sites, which counted LinkedIn and MySpace among their ranks, identified the hacks and notified all users, this stolen information was still listed for sale on the dark web.
As a result, attackers tried to use the information to access accounts on ‘GoToMyPC’, a remote desktop software provider that allows users to access their PC’s desktop from other machines. Naturally, this is a highly attractive target to hackers, made possible by most people’s poor password security. The breach was identified, but not before attackers managed to access some user’s accounts.
However, if 2FA had been enabled in this scenario, attackers wouldn’t have been able to get past the initial GoToMyPC login page. Both LinkedIn and GoToMyPC have since implemented 2FA login authentication.
2FA Pros
- Adds an extra layer of security to your online accounts
- Essential for fund safety on exchanges
- Better than SMS or Email authentication
- Not infallible, but highly increased security
- When used in conjunction with a password manager, makes accounts incredibly secure
2FA Cons
- Adds an extra step to the login process
- If you lose your authenticator app, it can be hard to access your accounts
Should You Use 2FA?
The short answer is yes. Although some users may be put off by the extra log in steps required, 2FA undoubtedly provides an important extra layer of security for your online accounts.
Think of 2FA as choosing to use a seat belt in a vehicle. Everyone knows that a seat belt is going to increase their chances of survival in a crash. While it’s not a total guarantee of safety, it’s an extra layer of essential protection.

In the same way, while 2FA can’t guarantee your accounts won’t be compromised, it makes it much harder for a hacker to gain access. So, just like you would be crazy not to wear a seat belt in a speeding car, you’d be crazy not to use 2FA solutions to protect your online accounts.
That said, it’s difficult to choose the best authenticator apps. Overall, each of the authenticator apps we have discussed above are great all-around options to add an extra layer of protection to your accounts. However, all users should also consider using 2FA apps in conjunction with a password manager, and ensure that a sufficiently strong PIN or biometric code is used to access your mobile device.
We also recommend using a secure browser and a reputable VPN service to further increase security and privacy online.
References
Eleven Ways to Defeat Two-Factor Authentication by Roger Grimes
The SIM Swapping Bible: What To Do When SIM-Swapping Happens To You
How Time-based One-Time Passwords work and why you should use them in your app
The Complete Guide to Two-Factor Authentication (2FA) was originally found on Cryptocurrency News | Tech, Privacy, Bitcoin & Blockchain | Blokt.