Rolling back Ryuk Ransomware
Credit to Author: Sally Adam| Date: Fri, 04 Oct 2019 16:05:36 +0000
In recent weeks SophosLabs has seen a significant spike in Ryuk ransomware. This particularly nasty threat is delivered via a sophisticated, multi-stage attack, paralyzing organizations and leaving them hostage to crippling ransoms.
To understand how to stop Ryuk it’s helpful to know how the attacks unfold.
The actors behind Ryuk are active adversaries who combine advanced attack techniques with interactive, hands-on hacking to increase their rate of success.
They typically target organizations that cannot withstand any downtime, such as newspapers, municipalities, and utilities, to increase the likelihood of payment. And speaking of payments – they’re big. Often 6-figure sums payable in Bitcoin.
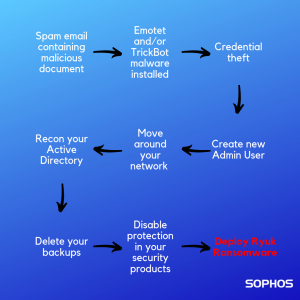
Ryuk attacks are complex. They frequently start with an Emotet or TrickBot attack, delivered via malicious attachments in spam emails, which enables the cybercriminals to get on your network.
Once there, they steal credentials and create a new admin user. With their escalated admin privileges in place, the hackers can move around your network, survey your Active Directory, and delete your backups.
After removing your safety net they attempt to disable your cybersecurity products before finally releasing the Ryuk ransomware, encrypting your files and demanding huge ransom payments.
Stopping Ryuk with Sophos Intercept X Advanced
Stopping Ryuk isn’t just about stopping one piece of software, it’s about stopping an active adversary and disrupting the attack chain that puts them in a position to run Ryuk. Sophos Intercept X Advanced includes a range of technologies to detect and disrupt different stages of the attack, including:
- Detecting and blocking the exploit techniques used to download and install Emotet and Trickbot (often via PowerShell or WMI), preventing the hackers from getting on your network.
- Blocking lateral movement across your network by working in real-time with Sophos XG Firewall.
- Preventing credential theft, thereby stopping unauthorized access to your systems and the escalation of admin privileges.
- Stopping the ransomware from executing by examining its “DNA” with our deep learning neural network.
- Detecting and rolling-back the unauthorized encryption of files via the CryptoGuard capabilities
Watch this video to see the CryptoGuard capabilities in Intercept X stop Ryuk dead.
Take a free trial of Intercept X and get 30-days free anti-ransomware protection.
Your dedicated team of threat hunters and response experts
While many strains of ransomware are distributed via large-scale spam campaigns, Ryuk uses automated means to gain an initial foothold, then employs human ingenuity to evade detection. In other words, there’s a human behind the attack whose goal is to circumvent or manipulate your existing security controls.
For active adversary attacks like these, having a dedicated team of threat hunters and response experts can make all the difference. The Sophos Managed Threat Response team proactively hunt, detect and respond to attacks in real-time to neutralize ransomware and other advanced threats before they can compromise your data. Find out more about Sophos MTR today.
Best practices to stop ransomware
Whatever the size of your company and whatever industry you’re in, we recommend you follow these best practices to minimize your risk of falling victim to a ransomware attack:
- Educate your users. Teach them about the importance of strong passwords and roll out two-factor authentication wherever you can.
- Protect access rights. Give user accounts and administrators only the access rights they need and nothing more.
- Make regular backups – and keep them offsite where attackers can’t find them. They could be your last line of defense against a six-figure ransom demand.
- Patch early, patch often. Ransomware like WannaCry and NotPetya relied on unpatched vulnerabilities to spread around the globe.
- Lock down your RDP. Turn off RDP if you don’t need it, and use rate limiting, 2FA or a VPN if you do.
- Ensure tamper protection is enabled. Ryuk and other ransomware attempt to disable your endpoint protection. Tamper protection is designed to prevent this from happening.
- Educate your team on phishing. Phishing is one of the main delivery mechanisms for ransomware.
- Use anti-ransomware protection. Sophos Intercept X and XG Firewall are designed to work hand in hand to combat ransomware and its effects. Sophos Managed Threat Response (MTR) provides a team of threat hunters who proactively hunt, detect and neutralizeattacks that require human intervention.